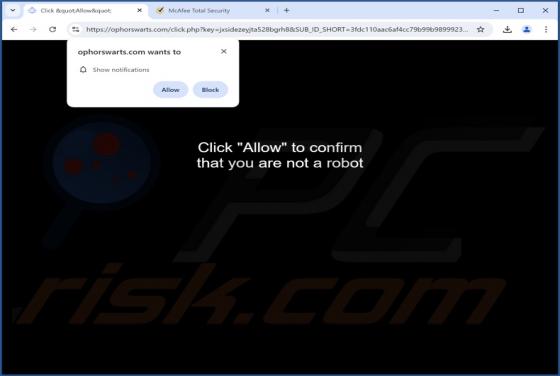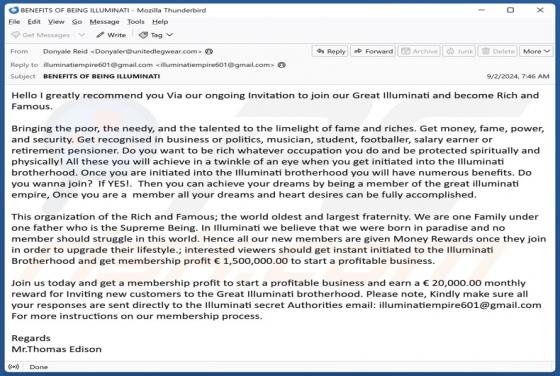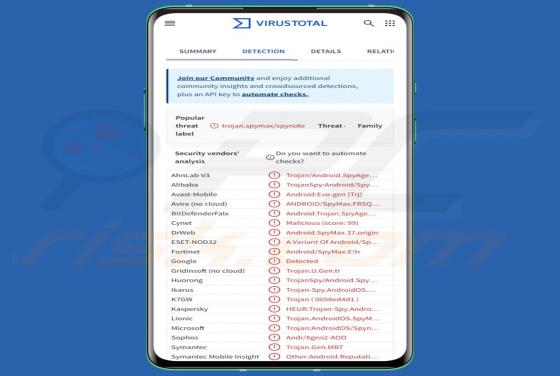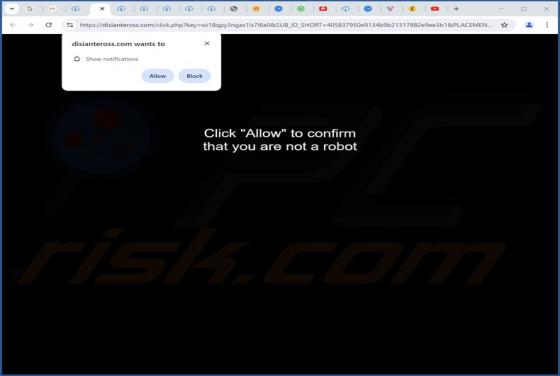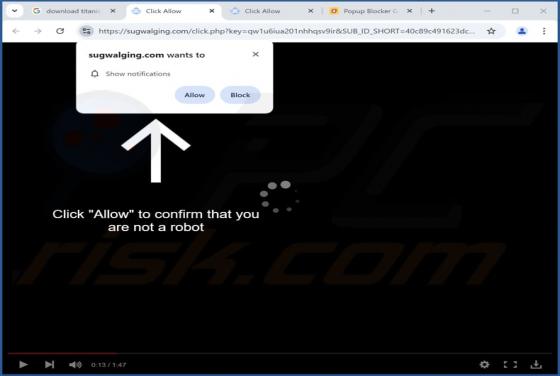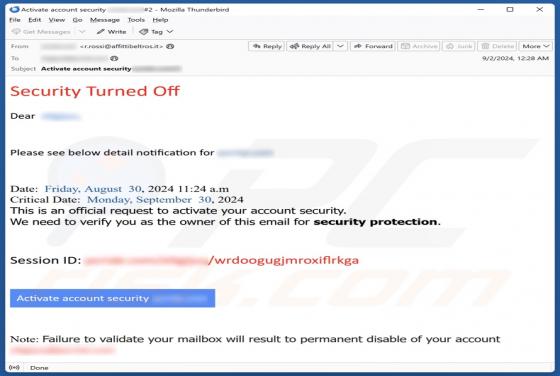
Security Turned Off Email Scam
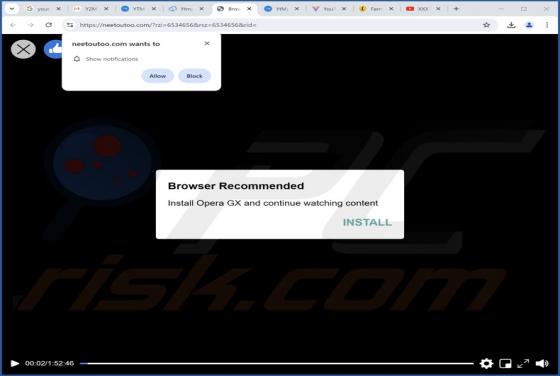
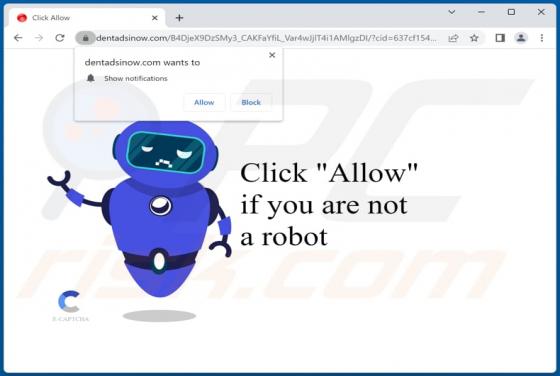
After examining the "Security Turned Off" email, we determined that it is spam. It is a phishing letter targeting recipients' account log-in credentials by claiming that their account has a mandatory security update. Failing to activate the security upgrade will supposedly result in the account be