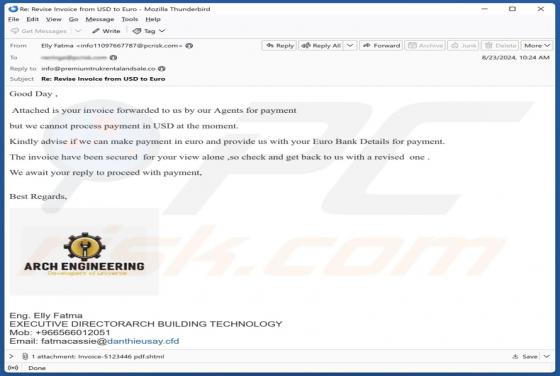
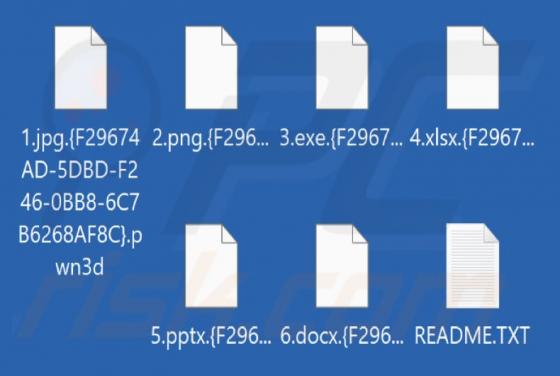
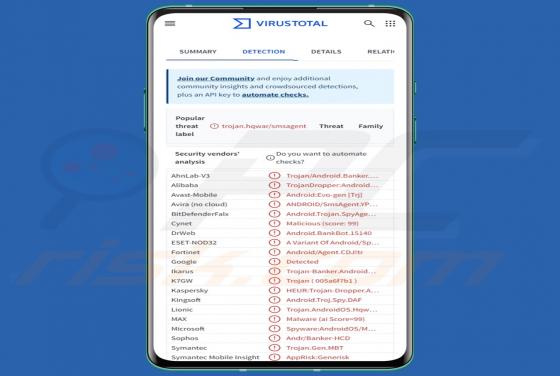
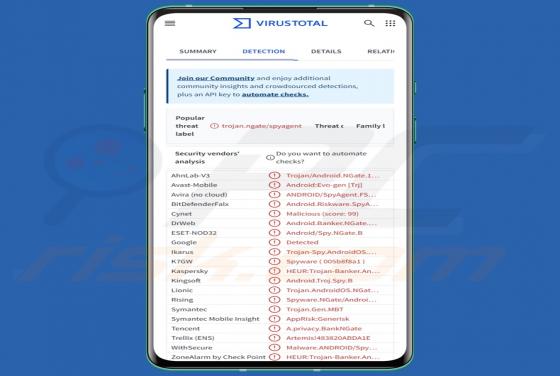
Department Of Employment & Labour Email Scam
After inspecting this "Department Of Employment & Labour" email, we determined that it is fake. This spam letter is presented as an ITT (Invitation To Tender), wherein recipients are called to bid on provisioning a project. The purpose of this phishing email is to deceive victims into disclos