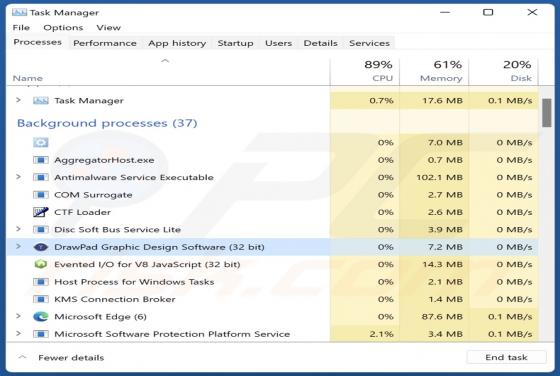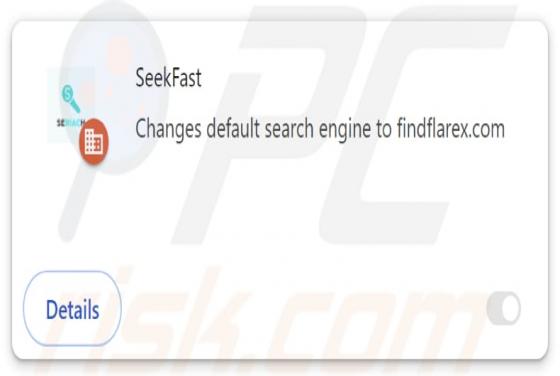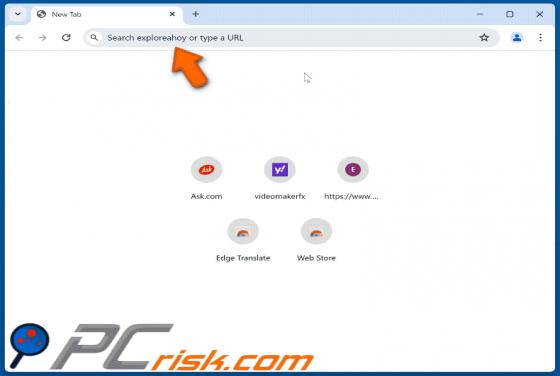
Exploreahoy.com Redirect
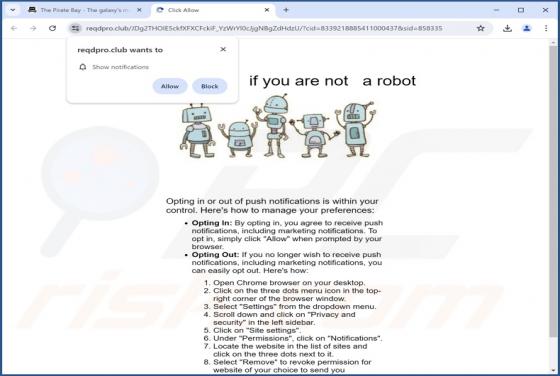
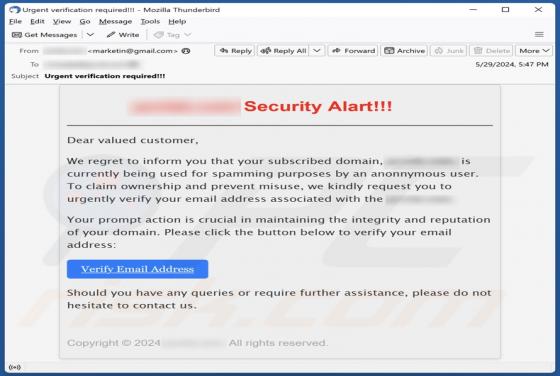
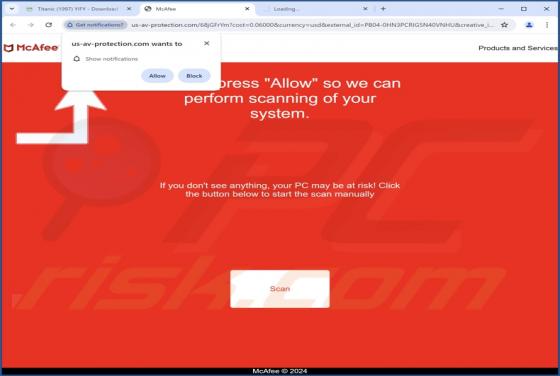
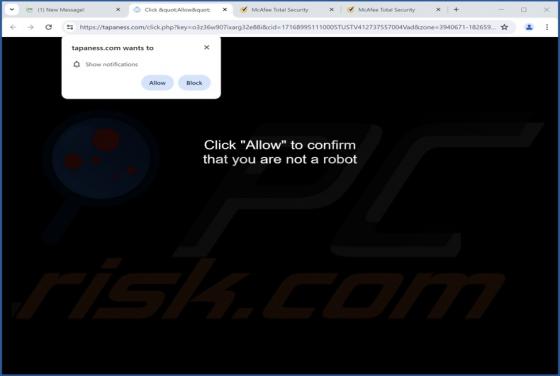
Exploreahoy.com is the address of a fraudulent search engine. Websites of this kind typically cannot provide search results, so they redirect to genuine Internet search engines. These fake sites are commonly promoted by browser hijackers. It is noteworthy that users who experience redirects to ex