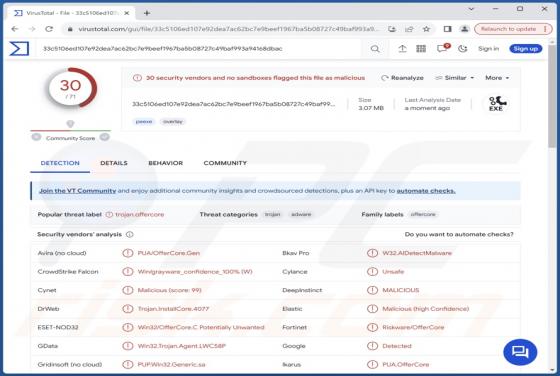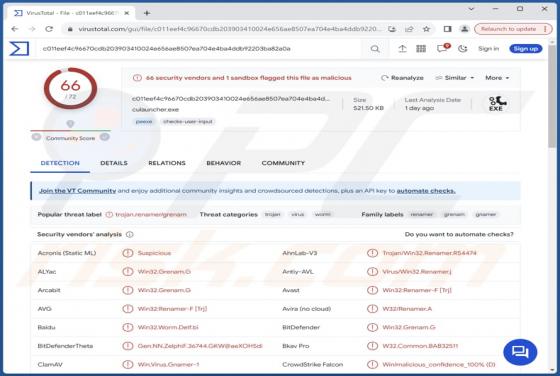
Troll Stealer
Written in Go language, Troll is a piece of malware that specializes in stealing sensitive information from infected computers. This malware operates through a multi-faceted approach, initially infiltrating systems via a deceptively innocent facade - a dropper masquerading as a benign security pro