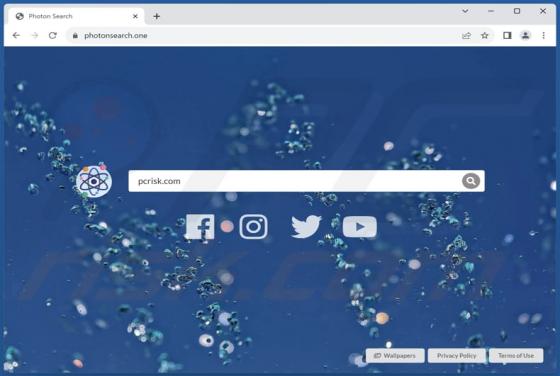
Photon Search Browser Hijacker
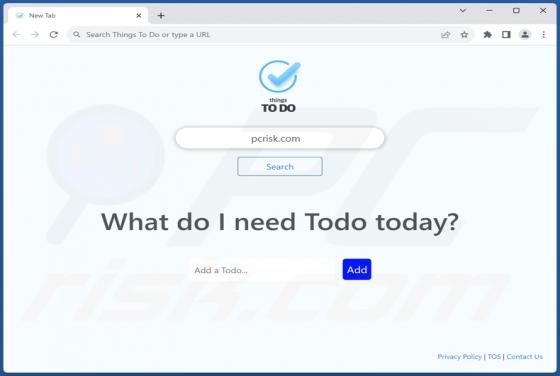
While assessing the Photon Search browser extension, we observed its intention to promote a fake search engine by manipulating web browser settings, a behavior often known as browser hijacking. It is essential to note that browser hijackers like Photon Search are typically advertised through dubio