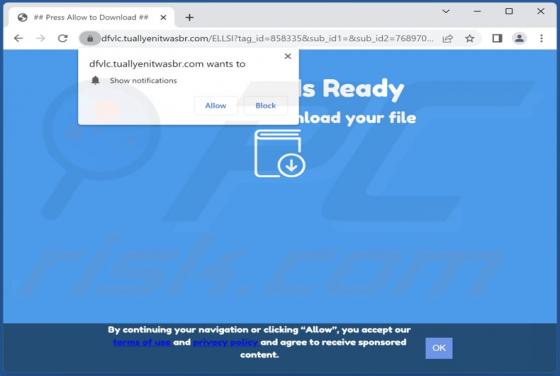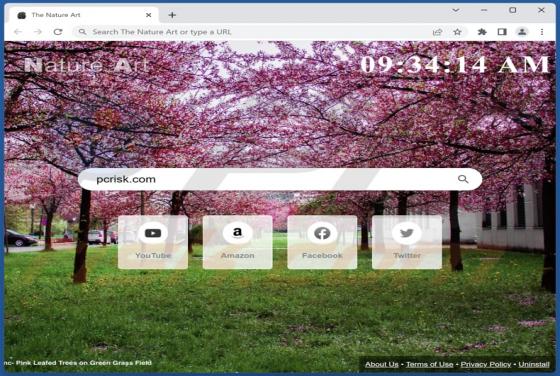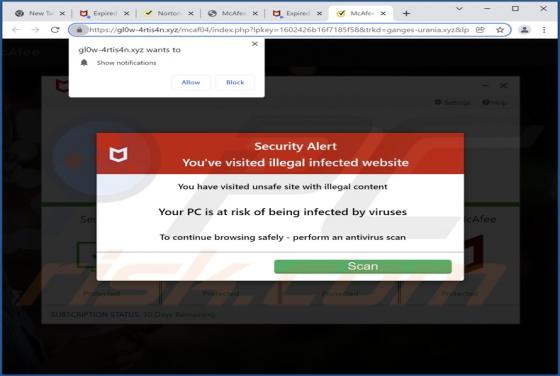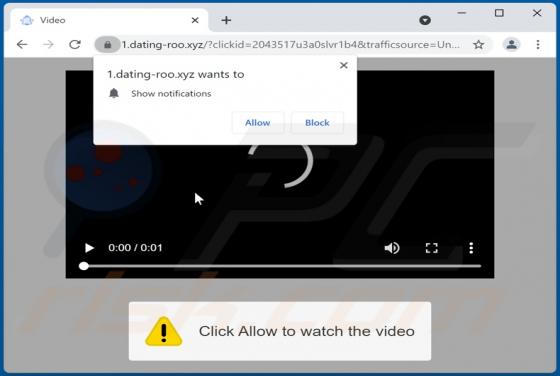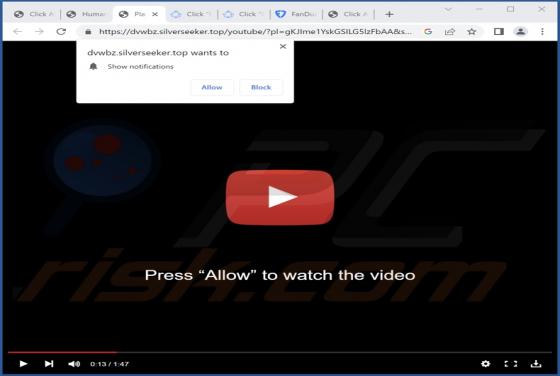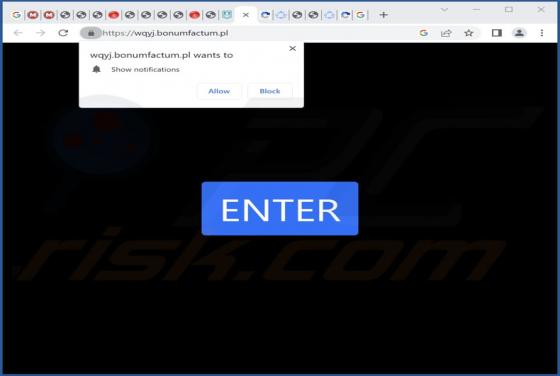
Bonumfactum.pl Ads
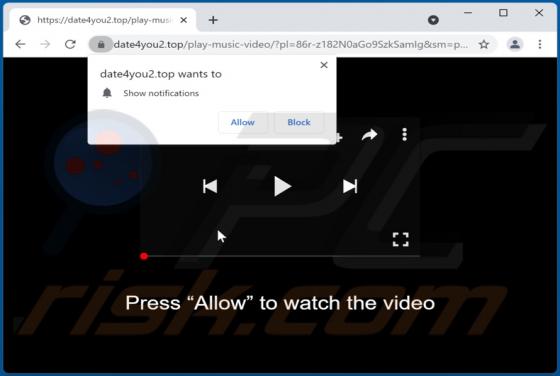
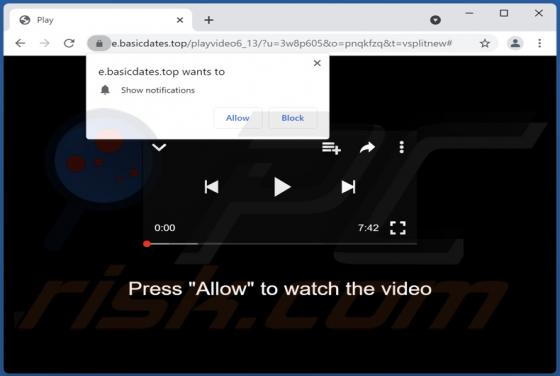
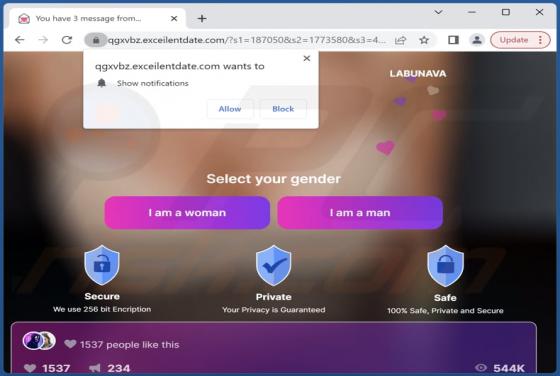
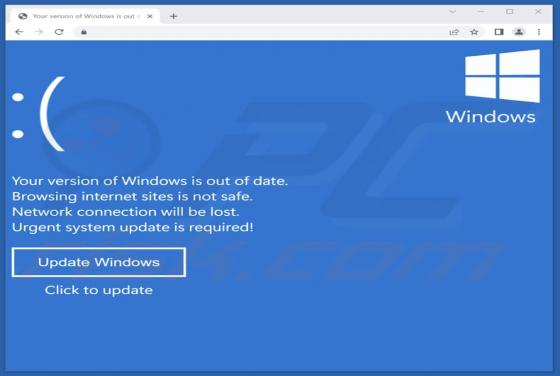
Upon examining bonumfactum[.]pl, we found that it is a shady website that can send untrustworthy notifications. Also, it may redirect visitors to other pages of this kind. Our team discovered bonumfactum[.]pl while inspecting dubious ads and sites that use rogue advertising networks. Upon