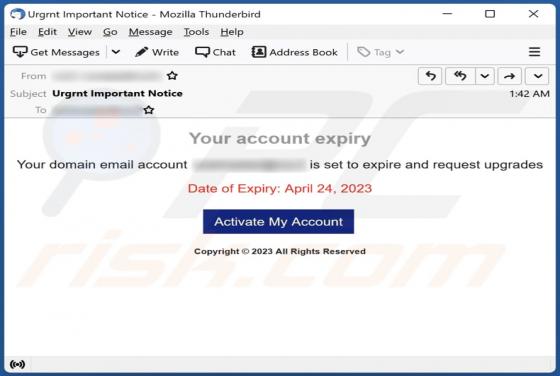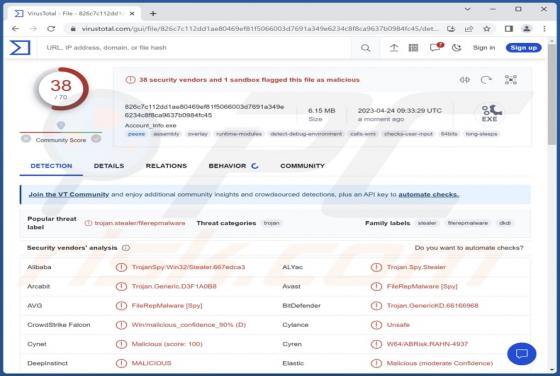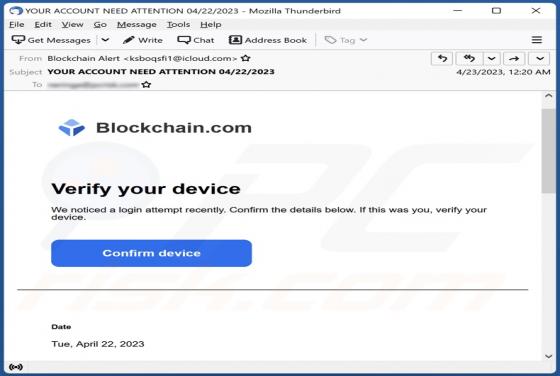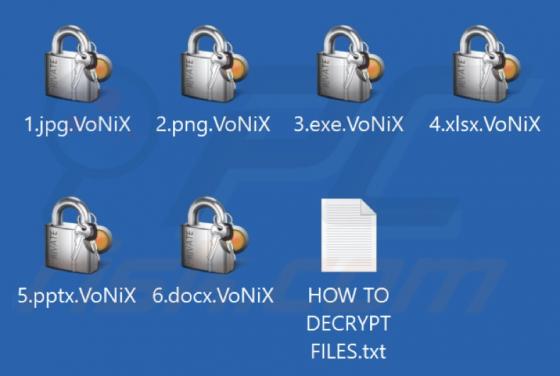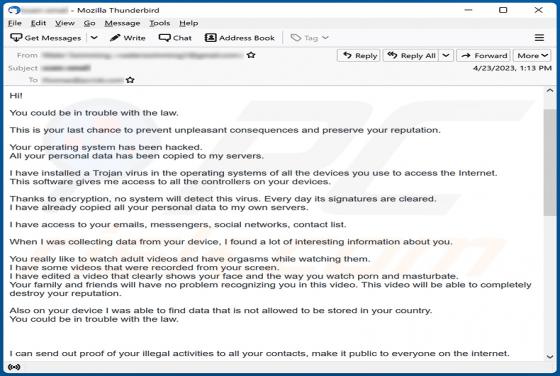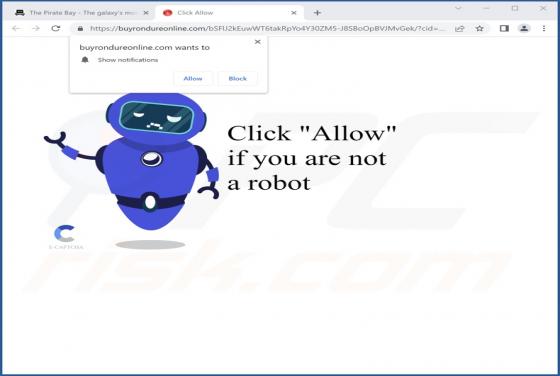
Buyrondureonline.com Ads
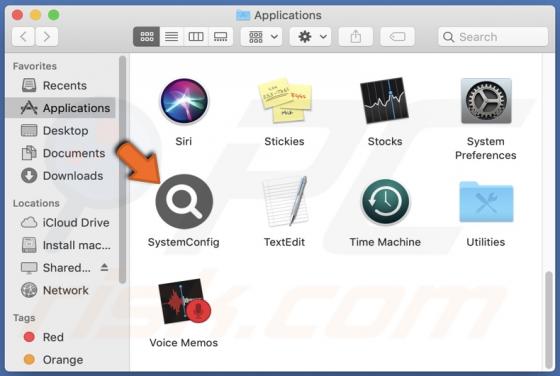
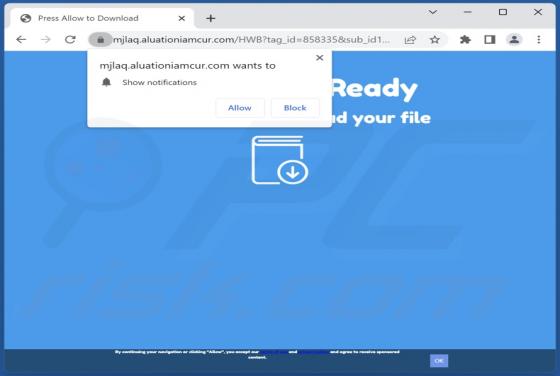
Our research team discovered the buyrondureonline[.]com rogue page while investigating suspicious websites. It operates by promoting browser notifications spam; at the time of research, it did so by using fake CAPTCHA verification. Additionally, this webpage can redirect visitors elsewhere (likely