CreedNetwork Adware (Mac)
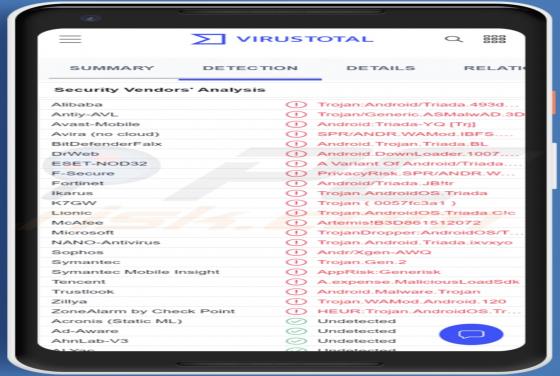
CreedNetwork is a rogue application discovered by our research team during a routine investigation of new submissions to VirusTotal. We inspected this piece of software and determined that it operates as adware. It is noteworthy that CreedNetwork is part of the AdLoad malware family. Adw