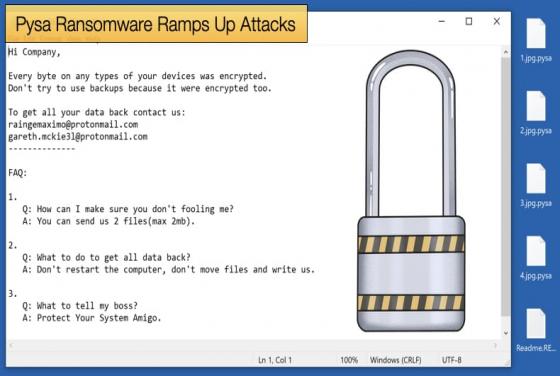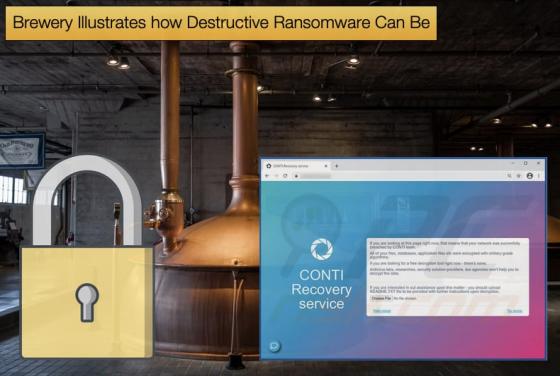

Brewery Illustrates how Destructive Ransomware Can Be
Towards the end of the holiday season Portland, Oregon-based brewery McMenamins confirmed it had suffered a ransomware attack dating back to December 12, 2021. On December 16, 2021, Bleeping Computer reported that the Brewery has suffered a ransomware incident. The brewery did confirm that it ha