GVU Virus
![]() Written by Tomas Meskauskas on (updated)
Written by Tomas Meskauskas on (updated)
What is GVU?
If you see this message (screenshot below) blocking your computer screen, your PC is infected with a ransomware infection. This scam originates from a family of ransomware called Adneukine and has been developed by cyber criminals to make money from unsuspecting PC users.
The message states that computer users have been downloading copyrighted content or watching pornography, and must therefore pay a 50 Euro fine. This statement is false. Bundesamt fur Sicherheit in der Informationtechnik (an authority from Germany) does not send messages such as this - it is a scam and computer users should not pay any fines.
Cyber criminals responsible for developing and distributing GVU ransomware hope that computer users will fall for their deceptive message and pay the bogus fine. This particular screen locker is a localized variant targeting computer users from Germany.

The same infection infiltrating a computer from the USA would appear in English as if being sent from the Internet Crime Complaint Center. There are several families of ransomware infections employing various deceptive methods in order to make their fake messages appear authentic.
Note that statements regarding video and sound recording are fake and implemented with the purpose of further intimidating PC users into paying this fake fine.
One screen locker from the Reveton family uses voice messages to scare PC users. If your computer screen is blocked by this fake GVU message, do not pay the fine. The correct way to deal with this deceptive message is to eliminate it from your PC. The first screenshot below is from the Reveton family of ransomware.
Other variants of the GVU ransomware virus:
Update 2015/02/05 - Cyber criminals have updated the design of GVU ransomware virus:

GVU ransomware is distributed through 'botnets'. Cyber criminals infect users' computer with Trojans, which download and execute this type of ransomware infection. Other known methods of proliferating the GVU virus include fake software updates, infected video codecs, and drive-by downloads.
Commonly, ransomware infects users' computers by exploiting security vulnerabilities found in flash and java software. To prevent GVU virus infiltration, always use antivirus and antispyware programs to protect your computer. If your PC is already infected with the GVU virus, use the removal guide provided to unlock your PC.
A deceptive message presented by the GVU virus:
Die ganze Tätigkeit dieses Computers ist registriert worden.
Wenn Sie eine Netzkamera verwenden, wurden Videos und Bilder für die Identifizierung gespart
Auf Ihrem Computer wurden illegal heruntergelassene Medien ("Raubkopien") gefunden. Diese sind in Form von Musik. Filmen oder Entertairimentsoftware vorhanden.Durch den Download wurden diese Medien vervielfältigt, so dass ebenfalls eine Strafbarkeit gemäß § 106 Urhebergesetz gegeben he.
Der Download von urheberrechtlich geschützten Medien durch das Internet oder einer Dateitauschbörse (Fiksharing) ist illegal und wird gemäß § 106 Urhebergesetz mit Geldstrafe oder Freiheitsstrafe von bis zu 3 Jahren bestraft. Weiterhin ist der Besitz nach § 184 Absatz 3 StGB strafbar und kann auch zur Einziehung des Rechners führen, mit dem die Dateien heruntergeladen wurden. Eine eindeutige Identifizierung Ihrer Person ist mit hüte Ihrer IP-Adresse und des Host names problemlos möglich. Die gefundenen Raubkopien wurden verschlüsselt und in ein geschütztes Verzeichnis kopiert. Um die Sperre aufzuheben und v/eitere Strafrechtlichen konsequenten aus dem Weg zu gehen, sind Sie verpflichtet eine Mahngebühr M Höhe von 50,- zu bezahlen. Zahlbar durch unseren Payment- Partner Ukash . Nach erfolgreicher Bezahlung wird Ihr Computer automatisch entiperrt. Um die Bezahlung durchzuführen, geben Sie den erworbenen Ukash -Code in das dafür vorgesehene Zahlungsfeld ein, wählen Sie den Wert Ihres Codes und drücken Sie anschliessend auf "Absenden". Gutschein muss mit einem Nennwert von 50 C seinAchtung! Wenn die feinen nicht innerhalb von zwei Tagen zu bezahlen, werden alle Daten an das Gericht übermittelt werden.
Instant automatic malware removal:
Manual threat removal might be a lengthy and complicated process that requires advanced IT skills. Combo Cleaner is a professional automatic malware removal tool that is recommended to get rid of malware. Download it by clicking the button below:
▼ DOWNLOAD Combo Cleaner
By downloading any software listed on this website you agree to our Privacy Policy and Terms of Use. To use full-featured product, you have to purchase a license for Combo Cleaner. 7 days free trial available. Combo Cleaner is owned and operated by Rcs Lt, the parent company of PCRisk.com read more.
Quick menu:
- What is GVU?
- STEP 1. "GVU" virus removal using safe mode with networking.
- STEP 2. "GVU" ransomware removal using System Restore.
GVU virus removal:
Step 1
Start your computer in Safe Mode. Click Start, click Shut Down, click Restart, click OK. During your computer starting process press the F8 key on your keyboard multiple times until you see the Windows Advanced Option menu, then select Safe Mode with Networking from the list.
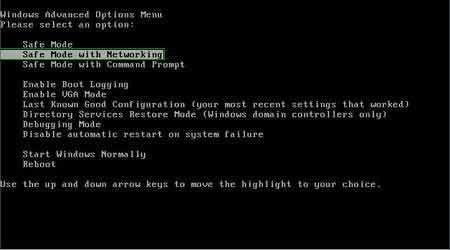
Video showing how to start Windows 7 in "Safe Mode with Networking":
Step 2
Log in to the account infected with GVU virus. Start your Internet browser and download a legitimate anti-spyware program. Update the anti-spyware software and start a full system scan. Remove all entries detected.
After completing these steps your computer should be clean. Reboot your computer in Normal Mode.
Alternative GVU virus removal guide:
If this ransomware blocks your screen when you start your computer in Safe Mode with Networking, try starting your PC in Safe Mode with Command Prompt.
Video showing how to remove ransomware virus using "Safe Mode with Command Prompt" and "System Restore":
1. During your computer starting process, press the F8 key on your keyboard multiple times until the Windows Advanced Options menu appears, and then select Safe Mode with Command Prompt from the list and press ENTER.
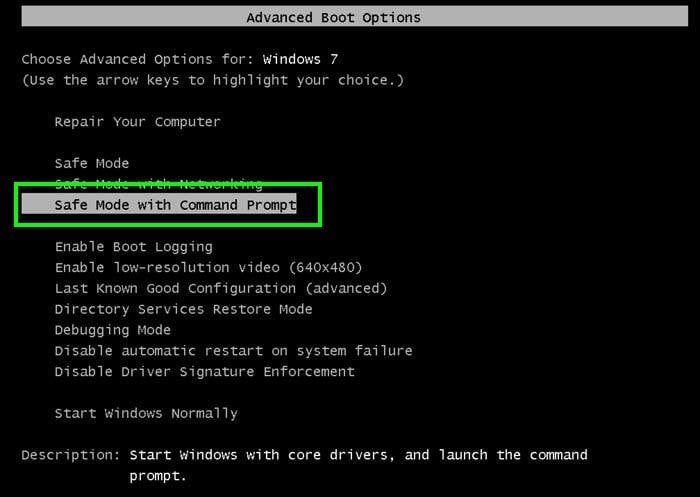
2. When Command Prompt Mode loads enter the following line: cd restore and press ENTER.
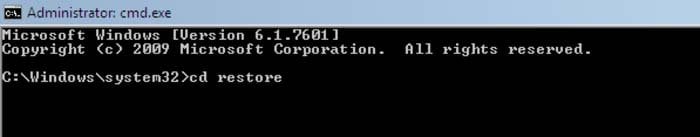
3. Next, type this line: rstrui.exe and press ENTER.
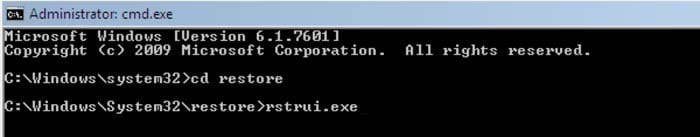
4. In the opened window, click "Next".
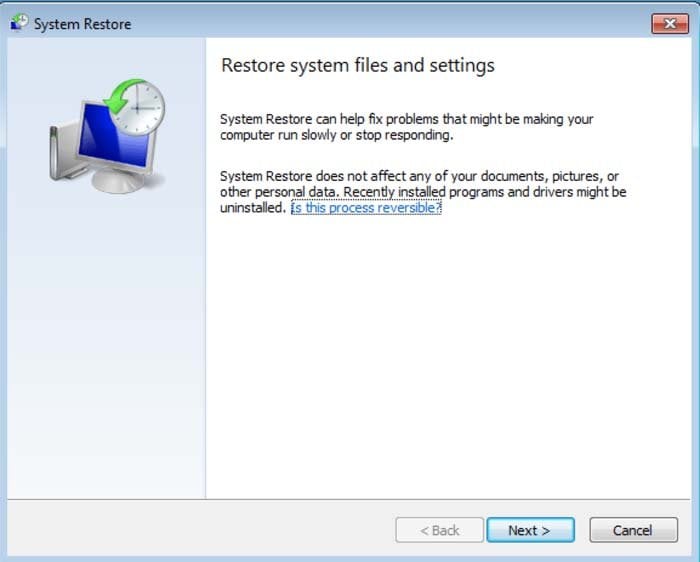
5. Select one of the available restore points and click "Next" (this will restore your computer system to an earlier time and date, prior to the ransomware infiltrating your PC).
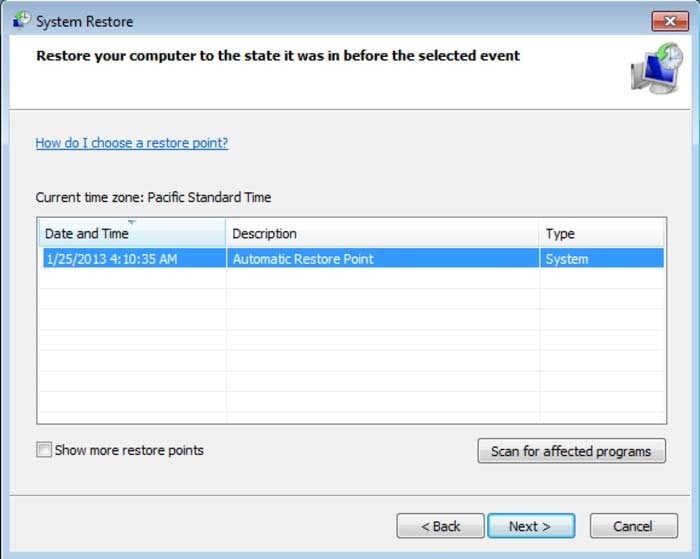
6. In the opened window, click "Yes".
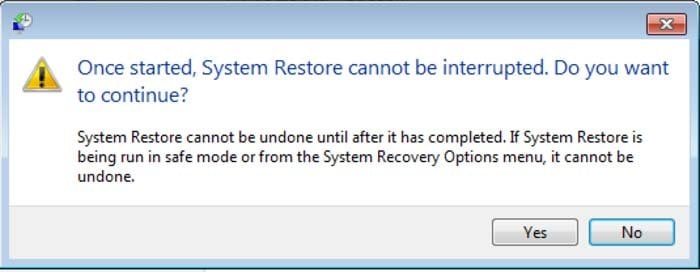
7. After restoring your computer to a previous date, download and scan your PC with recommended malware removal software to eliminate any remnants of the GVU virus.
Other methods used to eliminate this ransomware infection from your PC:
Remove the GVU virus using a Rescue Disk.
Other tools known to remove the GVU virus:




▼ Show Discussion