Virus and Spyware Removal Guides, uninstall instructions
What kind of malware is Epsilon?
Epsilon is the name of a malware designed to steal sensitive information. This stealer targets data from browsers, gaming-related and various other applications, as well as cryptocurrency wallets. Epsilon stealer has been observed being proliferated via campaigns targeting video game players.
What kind of malware is Atom?
Marketed as an economical keylogging solution tailored for entry-level hackers and criminals, Atom logger boasts the ability to capture keystrokes, visited websites, chats, instant messages, emails, screenshots, and additional data.
This keylogger is promoted and available for purchase within underground cybercrime forums commonly visited by hackers and scammers. With a price tag of just $15, Atom logger presents an affordable option, catering to criminals operating on a budget.

What kind of application is IchthyosaurusComunicus?
Upon inspecting the IchthyosaurusComunicus application, it was observed that it has the ability to access diverse data, oversee apps, extensions, and themes within the Chrome browser, and enable the "Managed by your organization" feature. It is crucial to highlight that the distribution method for IchthyosaurusComunicus involves a malicious installer.
What kind of malware is Pig865qq?
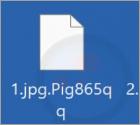
In our regular examination of malware samples submitted to the VirusTotal website, we have identified the Pig865qq ransomware, a variant associated with the GlobeImposter family. Pig865qq encrypts files, appends the ".Pig865qq" extension, and displays a ransom note ("HOW TO BACK YOUR FILES.exe").
An example of how Pig865qq modifies filenames: it changes "1.jpg" to "1.jpg.Pig865qq", "2.png" to "2.png.Pig865qq", and so forth.
What is "Our Security Scans Have Detected Potential Vulnerabilities"?
After closely examining this fraudulent scheme, our assessment indicates that it adheres to the structure of a technical support scam crafted to mislead unsuspecting visitors into performing certain actions. Such scams are commonly orchestrated to extract funds or information or to disseminate malware.
What kind of page is sbrakepads[.]com?
During a routine investigation of unreliable websites, our research team discovered the sbrakepads.com page. Upon inspection, we determined that this rogue webpage promotes browser notification spam and redirects visitors to other (likely dubious/malicious) sites.
Most users access pages like sbrakepads[.]com through redirects generated by websites that utilize rogue advertising networks.
What kind of page is qtadsmail[.]com?
Qtadsmail[.]com is a rogue page discovered by our research team during a routine investigation of questionable websites. It operates by promoting browser notification spam, and this webpage is also capable of redirecting visitors elsewhere (likely dubious/malicious sites).
Users primarily access qtadsmail[.]com and pages similar to it via redirects caused by websites utilizing rogue advertising networks.
What kind of page is mastason[.]com?
Our research team found the mastason[.]com rogue page while investigating suspicious websites. The webpage is designed to promote browser notification spam and redirect users to other (likely unreliable/dangerous) sites.
The majority of visitors to mastason[.]com and similar pages access them through redirects caused by websites that use rogue advertising networks.
What kind of malware is Hunters International?
Hunters International is a malicious program initially believed to be the rebrand of Hive ransomware following disruption of the latter's operations in 2023 by the FBI and Europol. The speculation regarding a rebrand was refuted by the group behind Hunters International and is further corroborated by other evidence.
Typically, ransomware is used to encrypt victims' data in order to demand ransoms for its decryption. However, Hunters International's group has announced that their operations are geared towards data exfiltration from large entities and not file encryption. This is confirmed by known attacks involving this ransomware.
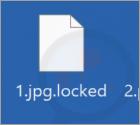
The sample of Hunters International we analyzed – appended encrypted files with a ".locked" extension; e.g., a file originally named "1.jpg" appeared as "1.jpg.locked", "2.png" as "2.png.locked", etc. It is noteworthy that this ransomware is capable of forgoing filename alteration. After the encryption is completed, the ransomware drops a ransom note titled "Contact Us.txt".
What kind of is "CPU-Z virus"?
"CPU-Z virus" refers to malicious content distributed under the guise of CPU-Z – a legitimate freeware system profiling and monitoring application. Using the names and graphics associated with genuine products or bundling them with harmful software or malware is not an uncommon technique.
One noteworthy example of "CPU-Z virus" is a trojanized CPU-Z version intended to infect systems with data-stealing malware. This campaign has been observed being promoted through malicious Google Ads using a search engine poisoning technique.
More Articles...
Page 148 of 2134
<< Start < Prev 141 142 143 144 145 146 147 148 149 150 Next > End >>