How to Remove KeRanger Ransomware
![]() Written by Tomas Meskauskas on
Written by Tomas Meskauskas on
KeRanger Ransomware Removal Instructions
KeRanger is ransomware-type malware that stealthily infiltrates systems and then encrypts stored files. Distributed via the Transmission BitTorrent client, KeRanger is the first ransomware that successfully works on the Mac OSX operating system.
What is KeRanger Ransomware?
The software is open-source and, therefore, cybercriminals have edited the source code and concealed KeRanger ransomware within. Once infiltrated, KeRanger remains silent for three days and only then starts encrypting files.
To encrypt, cybercriminals employ 2048-bit RSA encryption and, therefore, a private key is required to decrypt all files affected by KeRanger. Note that this ransomware adds a ".encrypted" extension to each encrypted file. Following successful encryption, KeRanger demands a ransom payment from victims in exchange for decryption software. If the user declines to do so, files affected by this malware will remain encrypted forever.
After encrypting the files, KeRanger creates a README_FOR_DECRYPT.txt file in each folder containing encrypted files. This text document contains all details regarding the encryption and step-by-step payment instructions.
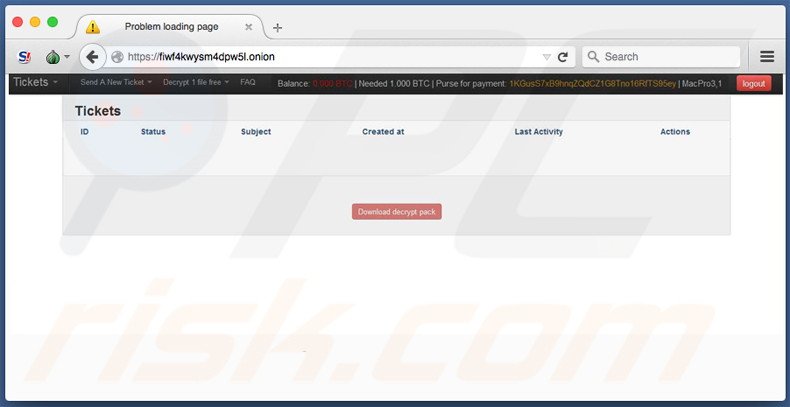
It is stated that the user must pay a ransom of 1 BitCoin (approximately $410.3). Payment must be made using the Tor browser - all details ('how to' and where to buy BitCoins, the link for the payment, etc.) are provided within the aforementioned text file.
Users are able to decrypt one selected file free of charge as insurance. Another interesting feature is the support service - users may ask questions and receive help to solve problems relating to payments.
As mentioned previously, files can only be decrypted using the private key, which is generated during encryption. This key is stored on remote servers controlled by cybercriminals. Unfortunately, there are currently no third-party tools capable of decrypting affected files. Therefore, the only solution to this problem is to restore your system/files from a backup.
KeRanger is similar to other crypto-ransomware infections such as CryptoLocker, TeslaCrypt, Locky, and other ransomware that also encrypts files and demands a ransom. The main difference between these ransomware infections is the encryption algorithm and ransom amount.
All are distributed in the same ways: fake software updates/installers, infectious email attachments, malicious files distributed via P2P networks (for example, Torrent), and trojans. Therefore, express caution when downloading files from untrusted sources, or opening attachments sent from unrecognized/suspicious email addresses.
Furthermore, keep your installed software up-to-date and use a legitimate anti-spyware or anti-virus suite. There is a high probability that your files will remain encrypted even if you pay the ransom. Therefore, do not pay any ransoms or attempt to contact cybercriminals.
Security researchers from Bitdefender claim that KeRanger is actually a rewrite of a Linux.Encoder ransomware.
KeRanger README_FOR_DECRYPT.txt file:
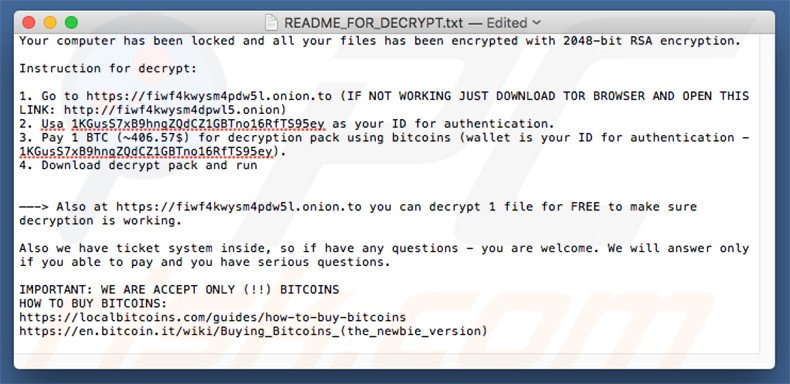
Text presented within this file:
Your computer has been locked and all your files has been encrypted with 2048-bit RSA encryption.
Instruction for decrypt:
1. Go to https://fiwf4kwysm4dpw5l.onion.to (IF NOT WORKING JUST DOWNLOAD TOR BROWSER AND OPEN THIS LINK: http://fiwf4kwysm4dpwl5.onion)
2. Usa 1KGusS7xB9hngZQdCZ1GBTno16RfTS95ey as your ID for authentication.
3. Pay 1 BTC (~406.57$) for decryption pack using bitcoins (wallet is your ID for authentication - 1KGusS7xB9hngZQdCZ1GBTno16RfTS95ey).
4. Download decrypt pack and run
——-> Also at https://fiwf4kwysm4pdw5l.onion.to you can decrypt 1 file for FREE to make sure decryption is working.
Also we have ticket system inside, so if have any questions - you are welcome. We will answer only if you able to pay and you have serious questions.
IMPORTANT: WE ARE ACCEPT ONLY (!!) BITCOINS
HOW TO BUY BITCOINS:
https://localbitcoins.com/guides/how-to-buy-bitcoins
https://en.bitcoin.it/wiki/Buying_Bitcoins_(the_newbie_version)
Screenshot of Transmission BitTorrent application:
List of KeRanger ransomware files:
~/Desktop/README_FOR_DECRYPT.txt
~/Library/.kernel_complete
~/Library/.kernel_pid
~/Library/.kernel_time
~/Applications/Transmission.app/Contents/Resources/General.rtf
/Applications/Transmission.app/Contents/Resources/General.rtf
/Volumes/Transmission/Transmission.app/Contents/Resources/General.rtf
List of file types targeted by KeRanger ransomware:
.3dm, .3ds, .3g2, .3gp, .7z, .ab4, .accdb, .accde, .accdr, .accdt, .ach, .acr, .act, .adb, .ads, .ai, .ait, .al, .apj, .arw, .asf, .asm, .asp, .asx, .avi, .back, .backup, .bak, .bank, .bay, .bdb, .bgt, .bik, .bkf, .bkp, .blend, .bpw, .cdb, .cdf, .cdr, .cdx, .ce1, .ce2, .cer, .cfp, .cgm, .class, .cls, .cmt, .cnv, .cpi, .cpp, .cr2, .craw, .crt, .crw, .cs, .csh, .csl, .csv, .dac, .db, .db3, .dbf, .dbr, .dbs, .dc2, .dcr, .dcs, .dcx, .ddd, .ddoc, .dds, .der, .des, .design, .dgc, .djvu, .dng, .doc, .docm, .docx, .dot, .dotm, .dotx, .drf, .drw, .dtd, .dwg, .dxb, .dxf, .dxg, .ebd, .edb, .eml, .eps, .erf, .exf, .fdb, .ffd, .fff, .fh, .fhd, .fla, .flac, .flv, .fm, .fp7, .fpx, .fxg, .gdb, .gray, .grey, .grw, .gry, .hbk, .hpp, .ibd, .idx, .iif, .indd, .java, .jpe, .jpeg, .jpg, .kdbx, .kdc, .key, .laccdb, .lua, .m4v, .maf, .mam, .maq, .mar, .maw, .max, .mdb, .mdc, .mde, .mdf, .mdt, .mef, .mfw, .mmw, .mos, .mov, .mp3, .mp4, .mpg, .mpp, .mrw, .mso, .myd, .ndd, .nef, .nk2, .nrw, .ns2, .ns3, .ns4, .nsd, .nsf, .nsg, .nsh, .nwb, .nx1, .nx2, .nyf, .obj, .odb, .odc, .odf, .odg, .odm, .odp, .ods, .odt, .oil, .one, .orf, .otg, .oth, .otp, .ots, .ott, .p12, .p7b, .p7c, .pages, .pas, .pat, .pbo, .pcd, .pct, .pdb, .pdd, .pdf, .pef, .pem, .pfx, .php, .pip, .pl, .plc, .pot, .potm, .potx, .ppam, .pps, .ppsm, .ppsx, .ppt, .pptm, .pptx, .prf, .ps, .psafe3, .psd, .pspimage, .ptx, .pub, .puz, .py, .qba, .qbb, .qbm, .qbw, .qbx, .r3d, .raf, .rar, .rat, .raw, .rdb, .rm, .rtf, .rwz, .sas7bdat, .say, .sd0, .sda, .sdf, .snp, .sql, .sr2, .srf, .srt, .srw, .st4, .st5, .st6, .st7, .st8, .stc, .std, .sti, .stw, .stx, .svg, .swf, .sxc, .sxd, .sxg, .sxi, .sxm, .sxw, .tex, .tga, .thm, .tlg, .txt, .vob, .vsd, .vsx, .vtx, .wav, .wb2, .wbk, .wdb, .wll, .wmv, .wpd, .wps, .x11, .x3f, .xla, .xlam, .xlb, .xlc, .xlk, .xll, .xlm, .xlr, .xls, .xlsb, .xlsm, .xlsx, .xlt, .xltm, .xltx, .xlw, .xpp, .xsn, .yuv, .zip, .tar, .tgz, .gzip, .tib, .sparsebundle
Table of Contents:
How to Remove KeRanger Ransomware?
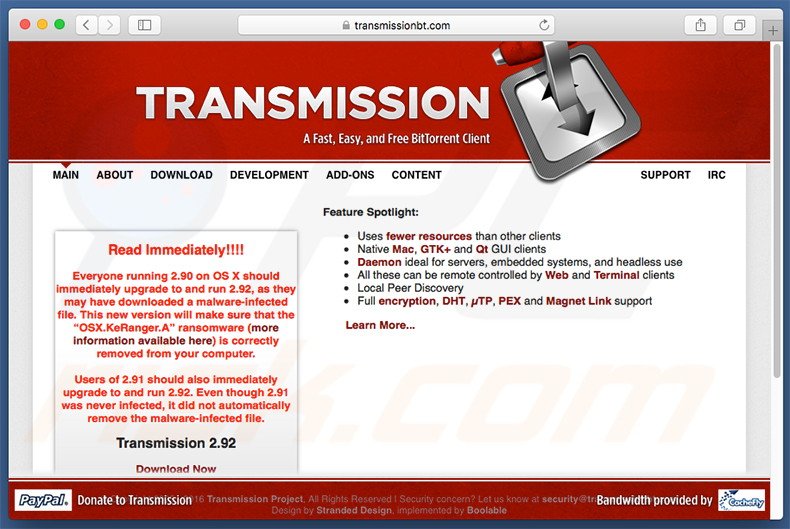
As mentioned previously, KeRanger is distributed using Transmission BitTorrent (2.90 version). Therefore, to remove this malware, you must upgrade this software to version 2.92. Once executed, an upgraded version will automatically remove "OSX.KeRanger.A" ransomware.
Users who have installed version 2.91 should also upgrade it since although this version was never infected, it is not capable of removing the KeRanger ransomware. Note that this will not decrypt the files - it will only remove the ransomware and prevent further encryption.
Transmission BitTorrent application installer set-up:
Official Transmission BitTorrent website:

▼ Show Discussion