Bart Ransomware
Bart Ransomware is a new ransomware reported in the media only a few days ago. Proofpoint wrote a detailed technical analysis of it here.
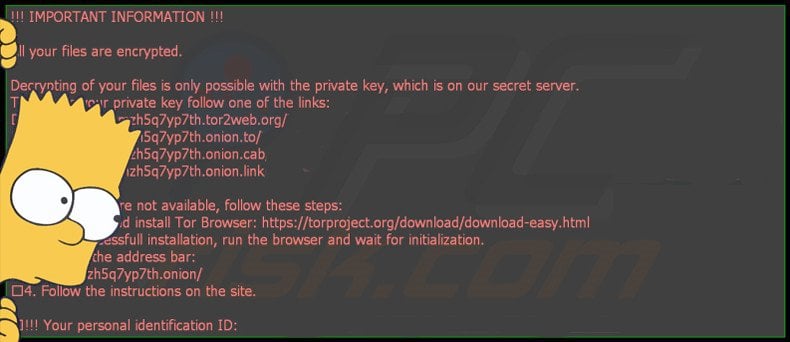
Like other ransomware, this sets the wallpaper to show the ransom message, then directs the user where they can pay the ransom to obtain the passcode to their files. It does not lock the computer screen.
This ransom, at $2,000, is a lot higher than others we have seen.
The name of the ransomware “Bart Doh!” might give a clue as to who wrote it, or at least how old they are.
The expression “doh!” is an exclamation in English that means “darn” or “drats.” It was made famous by the cartoon “The Simpsons” which has been running on television for more than 30 years. Bart Simpson would say “doh!” when he said or did something stupid.
Another clue as to the demographics of the virus writer is it does not attack computers whose language is Russian or Belarusian.
How it Works. What to Look for.
Bart ransomware encrypts single files and not the entire disk or the boot sector. That means at least the victim can continue to use their computer and not be locked or unable to restart it. The only indication that certain files have been locked is the desktop has been changed and certain files have been encrypted, which you would notice when you try to open them.
The infection works as do more than 90% of malware attacks, which is through a phishing attack. The phishing email contains zip files that contain JavaScript.
Anyone clicking on a zip file that contains JavaScript should get a warning from either or both of their antivirus software and the operating system. JavaScript are instructions. A zip file should contain no instructions. People are most likely ignoring these warnings, in which case this infection is their own fault. So train your users on security.
The zip attachments are disguised to look like photos with names like “photos.jpg.” But inside the zip files are JavaScript files, which you can detect because their file name suffix is .js.
JavaScript is used in web pages to make them interactive. But it is also a programming language that can be run from the command prompt. The commands it executes here is to download the Bart ransomware and then run it.
Some other Observations
One thing the Proofpoint analysis tells us yields up one obvious conclusion. They say the virus does not attach to any command and control center. That means the virus does not logon to the hacker's server to do anything when it is running, like obtain an encryption key. Nor does it do that when the user makes the bitcoin payment.
That means it is not using any data from the hacker’s server to calculate the encryption key. So the logic to do that is inside the malware itself. That means that once one person pays for a key to unlock their computer that key has a large probably that it will work for other people.
In other words the key is not calculated based on anything that would uniquely identify the victim’s computer, like the MAC address of their network card, or their relationship to the hacker. So the algorithm used to generate the key used to encrypt and the key used to decrypt has to exist independent of any session information obtained from the hacker’s server.
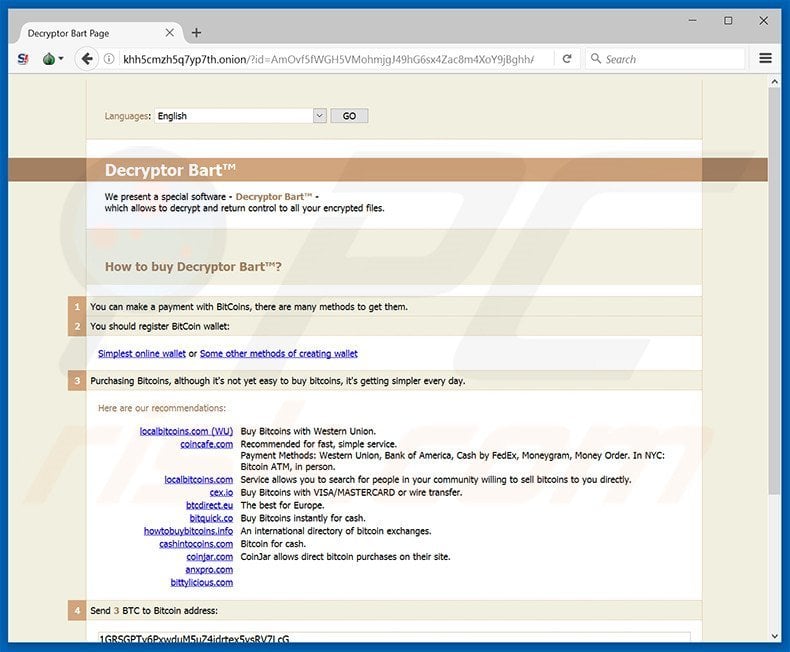
So hopefully victims of this can Google the virus name and in the near future someone would have published a list of keys that have previously worked.
How to Stop Bart
Since this virus is spread via phishing, it could be stopped by crowdsource anti-spam software if it matches two conditions. This is based on two principles of how that works.
First, specific aspects of the spam emails get reported in crowdsource online databases, like SpaumHaus, as people report that these are spam. That includes specific words in the emails. And it might include the IP address of the SMTP mailer used to send the spam, but only if that server is flagged as compromised by many people.
Secondly, by default anti-spam software installed on a company’s email server, or those used by large email providers like Google, will look with suspicion on any zipped attachments. They look inside those zipped attachments and will notice that these zipped files contain JavaScript.
That is a red flag. Those anti-spam systems also use anti-virus. So they will compare that JavaScript and any other objects they find in those zip files and mark those if they match known viruses.
If these two items match that means the mail will get moved to the spam folder in your email. Hardly anyone looks there so only if the spammers have been blatant in sending out many thousands of these emails will their emails get blocked that way. There are some inherent weaknesses in these systems and approach, which is why so many of us get spam email anyway.
Now, as to how to defeat Bart: you can’t.
There is no way that you can use bruteforce to try to guess the password unless you are a programmer willing to spend time to try that and even then you will probably run into some difficulty, like the inability to pass the key to the virus automatically.
The only way to defeat this would be to retrieve any files that have been encrypted from a point-in-time backup prior to when the device was hacked.
Some systems, like Google docs, support this type of versioning.
Of course you would need to completely erase your device by reinstalling the operating system to get rid of the ransomware first. If you are following best practices, meaning keeping all your data in the cloud, then erasing your computer should not be an inconvenience for you.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion