Cryptography and Ransomware
Ransomware is based on the idea that the victim cannot decrypt their encrypted files with a key because it would be impossible to guess the value of the key. The hacker who has encrypted a file like this will sell the victim this key.
So you could say that they have held their file hostage and are demanding ransom, which is why they call it ransomware.
Ransomware Cryptography Explained
It might seem counterintuitive that the output of an encrypted file is text even if the input is not. That is because the bits in the file are what is encrypted, and bits are just numbers.
Let’s look at an example.
If you ask Ubuntu what type of file a Word document in.doc using the file command:
file in.doc
It will say:
in.doc: Microsoft Word 2007+
This file is in a binary format that cannot be displayed with a text editor. If you try to display it you will get gibberish like this:
U��4����F+LH|x�2�@�ڮ8j
^����&��b0c5���Xi� �,I�($�G��9��d������cLB�^Lh\%��iz)-^L���v�F��\k���mسV�Q��[B.�
_��p n�
<#�=�$�
So what does it look like when encrypted?
Hackers are going to use the same tools as honest programmers, most of whom use openssl, which is built into Linux systems. Openssl is open source software that implements the encryption techniques invented by mathematicians and cryptologists some decades ago, like AES (Advanced Encryption Standard).
Here is how to encrypt a file using openssl from the command line. When we type this command we enter the passcode when prompted:
openssl enc -aes-256-cbc -in in.doc -out out.doc.enc
enter aes-256-cbc encryption password:
Then ask Ubuntu what format the encrypted file is in and it will tell you ASCII text.
file out.doc.enc
out.doc.enc: ASCII text
And when we look at the top of this file you can see that it is plain text:
U2FsdGVkX1+ZFWfn7HwskHQYivyAxAzSAPaycHFi5L1VVRGe38NznYLVnIdpJAUz
wa146rhYLwakr8d3Xo+vnwRYPtzv1JXmknIzgYumDTkKPyA4vzBWZq3e246JDBND
762HHa4akkZOcFbPwaSRBaiD4JR2JX2fbOoet7d2sBag2UO+g7rwFX467j2Rx3GV
hdz3PhGKLu+LrwJ2Jx86ZNrAtF/5AC2nqMOZiZYEKDuUIa/T+OpRx9LjYUONAGn6
2wwf7g18HGnE3+K9THlq0zIiVvfnRXPW8RlFSxZ3n3nYICI5Jm9hW9ASwF1Yj1mw
wn4JPb7uIwDrg+k2QZDFT2aQUboNkJRhPBi4oSWlZjpm5qrzmIZXhsh6jS+vwfFZ
To decrypt this file we write:
openssl enc -d -aes-256-cbc -in out.doc.enc -out out.doc.dec
But that only works if you know the key that you typed above.
In this example, we are saying to use the AES encryption algorithm with a 256 bit key and to use block cipher mode (cbc).
A block cipher means a series of bits used as a single unit to product text. That text, which is called ciphertext, is then what is encrypted by the encryption algorithm. The reference to block means that data is stored in units of fixed length known as blocks.
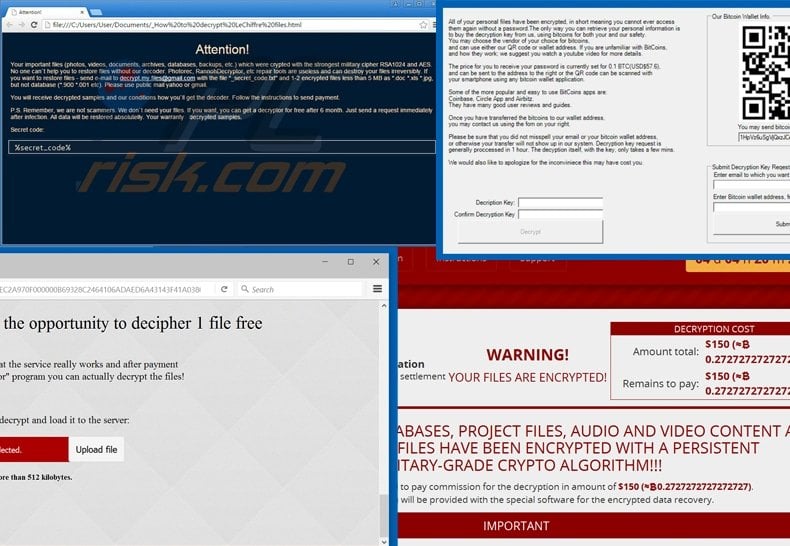
The Way Cryptography Works
All encryption algorithms are based on the same basic mathematical problem, which is the difficulty in determining whether a number is prime. Encryption keys are usually the product of two price numbers, or some variation of that. Find one prime factor and you know the other.
A prime number is a number that cannot be factored. All other other numbers, like 6, can be written as a product of prime numbers, 6=2x3. But to find those factors, a computer has to churn through all the numbers less than or equal to the square root of that number (See if you can understand why you only need to go up to the square root.) to see if any of those numbers divide the target number. In 2,000 years no mathematician since Euclid has found a faster way. Many have tried.
What makes this difficult to crack is the key size is such a large number that it is impossible to factor with today’s computing power.
For example, a 256 bit key means there are 2 raised to the 256 possibilities. (It is 2 because each bit can be a 0 or a 1). That is a number with 77 zeros. It would take a computer many, many years to churn through all of those possibilities. (Cryptographers at Princeton University wanted to show how long it would take a computer to guess the value of a 1024 bit encryption key. They connected hundreds of computers together to work on the problem. It took 2 years.)
The way to construct one of these keys is explained with an example in this RSA encryption algorithm example.
Brute Force Proof
If you try to login to Windows too many times the operating system will lock your account when you are in a corporate environment and there is some kind of software, like Active Directory, that issues userids and passwords.
But a ransomware victim could try a brute force attack to unlock a file, as there is no limit on how many times they can try that. But what makes the encryption unbreakable is there are so many possibility encryption keys to guess as to make that all but impossible.
The only way to defeat this is if there is a flaw in its implementation. In other words the mathematics behind the algorithm are solid. But a programmer has to turn that idea into working code. They do that with different programming libraries, like in Java. It could be the case that they made a mistake there. A hacker could study that and find some weakness. For example there could be a bug that might expose data in clear text in memory.
Ransomware
Cerber, Locky and Troldesh are common ransomware infections. They use public key encryption. That uses two keys: a public key and a private key. The hacker encrypts the data with a public key. It can only be decrypted with a private key.
It is surprising that they would use this approach and not an encryption algorithm like AES. This is because the private key would have to be present on the victim’s machine. You are supposed to remove your private key from a computer when you encrypt data as that can be used to decrypt it.
So the hacker sends themselves a copy of the private key when they run their ransomware and then deletes it from the victim's computer. The hackers threaten the victims that they will delete the private key if the victim does not pay the ransom within a certain period of time.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate

▼ Show Discussion