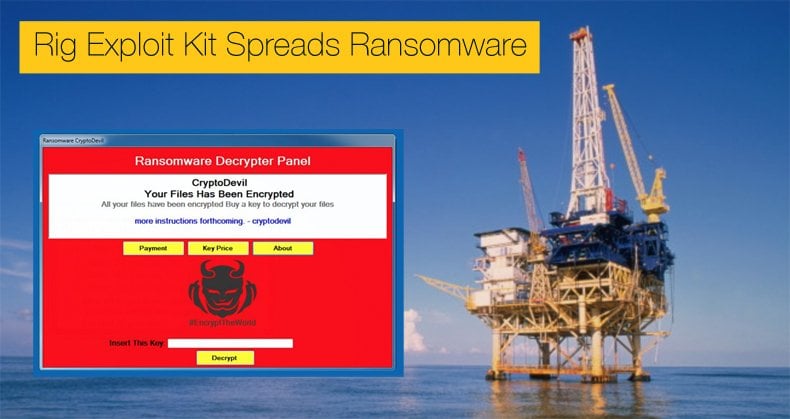
Rig Exploit Kit Spreads Ransomware
Heimdal Security says the Rig Exploit Kit has been used to plant Cerber ransomware on domains ending with the .news suffix, including the shortened list shown below. (Cerber has the unique feature of talking to its victims.)
An exploit kit is a set of tools developed by criminal gangs. They keep a staff of programmers to keep the product up-to-date and add improvements.
Virustotal reports show that only 2-5 out of 68 Anti-Virus products they tested can detect this type of attack. (You can enter the URL of any site here and Virustotal will check it.)
mind.pci [.] news (Virustotal report)
fun.rum [.] news (Virustotal report)
open.oral [.] news (Virustotal report)
It is not necessary for users to visit these .news websites. Instead the hackers update WordPress files and other web content that loads iFrames with advertising. The hackers use DoSWF, JavaScript, Flash, and VBscript to direct users to sites where the Rig Exploit kits are hosted. The victim does not even need to click on any of the .news links to be infected.
The Rig Exploit kits looks for and then attacks any of the products shown below to gain remote code execution privileges.
Google Update Attacked
Hackers have even found that by putting a file called goopdate.dll in the same path as GoogleUpdate.exe it will load their .dll and not Google’s. Since GoogleUpdate.exe is the legitimate signed product, no warning is given to the user. They have been using this technique to spread the CryptoLuck ransomware.
Neutrino EK Unmasked
Heimdal Security also says that criminal hacker gangs had been using the Neutrino EK to spread the CrypMIC ransomware using drive-by downloads.
Neutrino became a leading EK after the arrest of a key individual behind the Angler EK. Now Security Intelligence reports that Rig has stepped into the void left when Neutrino’s methods were uncovered by Cisco and GoDaddy. Cybercriminals using Neutrino had been buying advertising space on OpenX and Revive advertising platforms. That gave them a place to load JavaScript that would direct users to their exploit kit landing page on infected web servers.
List of Affected Products and Versions
The list of software vulnerable to Rig is long, especially the list of Adobe products. (Click this link to find the version of the Adobe Player you are using.) All of the products have been patched. Below are the products along with their patch date. The Adobe products were patched between 2015 and 2016.
- Adobe Flash Player before 18.0.0.324 and 19.x and 20.x before 20.0.0.267 on Windows and OS X, 13.x through 13.0.0.302 on Windows and OS X.
- Adobe Flash Player 14.x through 18.0.0.203 on Windows and OS X.
- Adobe Flash Player before 11.2.202.559 on Linux.
- Adobe Flash Player 11.x through 11.2.202.481 on Linux.
- Adobe Flash Player 21.0.0.226.
- Adobe AIR before 20.0.0.233.
- Adobe AIR SDK before 20.0.0.233.
- Adobe AIR SDK 12.x through 18.0.0.204 on Linux Chrome.
- Chakra JavaScript scripting engine in Microsoft Edge. Patched November 8, 2016.
- Internet Explorer versions 9, 10, 11. Patched October 11, 2016.
- Silverlight version 5.0. Patched January 12, 2016.
Since these products have all been patched against the Rig exploits, the user just needs to update their products. And they need to push an education campaign to other users to help them learn how to update their products or just turn on the mechanism for doing that automatically if that is not already in place.
Persons who have been attacked by the ransomware will have to pay the ransom if they have no backup. This is one reason why no data should be kept on the local machine but kept in the cloud. Then the OS can simple we wiped. Of course that does not work it the infected data is a database hosted in the cloud.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion