Cross-Site Request Forgery (CSRF) and Magento Remote Code Execution
Cross-Site Request Forgery (CSRF) is a hacking technique of getting a user who is logged into an application to execute certain commands while authenticated and logged in. The Magento shopping cart (version 2.1.6 and below) has a security issue that allows that. Magento has known about this for some months but as of April 2017 still had not fixed it. Defense Code contacted the company and told them this is a red critical security problem.
Magento is an ecommerce engine for web sites. Defense Code reports that a hacker can exploit the site by using a feature that previews a video before it loads a Vimeo video. The hacker can change the POST to a GET, either in a malicious web page or HTML embedded in an email) and request a file that is an invalid image file, like a .php program. The system will respond saying the file type is invalid but will download it anyway.
When the malicious PHP file is downloaded then it can be called from the internet. So you can get a command shell and pass it arguments. Like with this php code:
It also downloads a .htaccess file which is Apache web server security. That sets the settings there to allow PHP code to run.
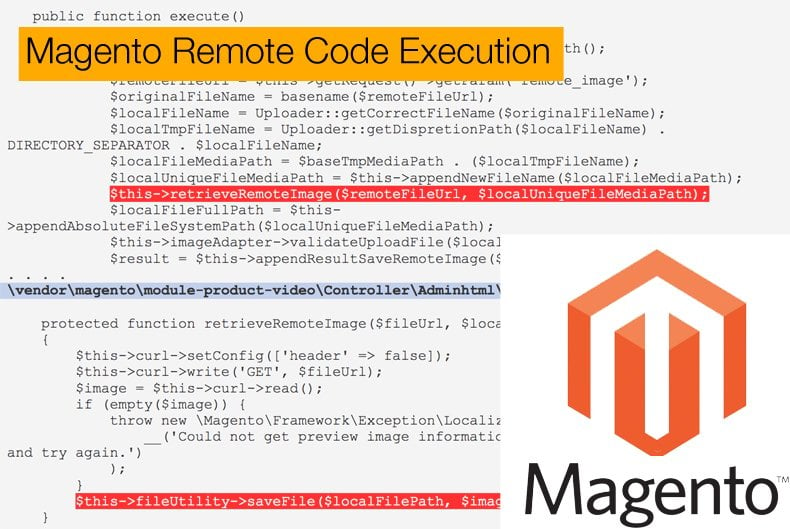
This exploits does not require pressing any button. By implanting HTML code in an email a Magento user gets the HTML GET or the hacker can entice the user into loading a page that does. They do not have to click on the actual video preview links or any link at all.
What is not clear is if the hacker can upload a .php file as a .jpg file in Vimeo or whether the hack points to a PHP file on a server of the hacker’s choosing.
The Comments Section Attack Vector
The paper by Defense Code raises an attack vector many of us probably have not thought of. Anyone can load this exploit by embedding html tags in the comments section of a web page, like a newspaper comments section. Some comment sections let you put simple HTML to make bold letters and colors etc. When the comments load the two files needed for the exploit download.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion