ALERT: New version of CryptoMix Detected
As of the first of May 2017 a new version of the CryptoMix, or CryptFile2, ransomware has been detected. This new version uses the Wallet extension for encrypted files. Previously, the Wallet extension was used on Dharma/Crysis and Sanctions ransomware. This new version of CryptoMix is currently using the following payment email addresses: shield0@usa.com, admin@hoist.desi, and crysis@life.com. This variant was first detected by Robert Rosenborg an independent security researcher and later confirmed by MalwareHunterTeam. Lawrence Abrams conducted some research into the new version and contends that what makes this version so frustrating and insidious is that it makes it harder for victims to detect what ransomware they are infected with.
Currently, at the time of writing, no guides exist to remove this version from the affected systems. If you believe you have been infected with this new version you must lock down the network you are on as Wallet will also scan unmapped network shares for files to encrypt.
Combating Evolving Ransomware
As the above mentioned new version of CryptoMix has no guide yet on how to combat it is perhaps prudent to go over how ransomware attacks can be combated and hopefully prevented. As with anything related to the broader category of cyber threats they are ever evolving and require constant monitoring. Ransomware gets its name directly from the attacker's intention, a ransom is demanded in order to decrypt files encrypted by the attacker. Often payment is to be made in Bitcoin or some other form of untraceable electronic payment method. The victim will receive a ransom note, the defining characteristic of ransomware, instructing how and when payment must be made in order to decrypt the affected files.

Sadly, such attacks are on the rise as cyber criminals feel that there is more to be squeezed from victims fairly effortlessly. Although the encryption methods used are advanced how the files are installed onto the victim's system have not changed. The primary method of this attack is via a phishing attack more often than not via a scam email. Often schools and hospitals are most at risk from a ransomware scam. This is due to the fact that many employees have network privileges and it only takes the action of one employee to compromise the entire network. This vulnerability was recently discovered by Cambrian College when the school's network was attacked in such a method and the cyber-criminal asked for 30 Bitcoins, roughly 47,000 USD. The University of Calgary also experienced such an attack in 2016. It is not only institutions that are attacked but also individuals with ransoms anywhere from 500 USD and upwards been asked to decrypt files. Often a timeframe is attached to the demand, if money is not received in time files may be permanently deleted.
One of the best ways to defend against such attacks is to educate staff as to the risks associated with ransomware, phishing, and other cyber-attacks. Having an aware workforce that contacts cyber security specialists immediately when emails are received that resemble an attempted phishing attack could prevent a ransomware attack. Another option that is easy to implement amongst the workforce is creating a backup policy requiring staff to back up data as a matter of course as a means to further protect data. Just as these measures can be adopted by staff they can just as easily incorporated into the individual’s life to help prevent such attacks. Obviously, these measures are not fool proof but they do go along to prevent such and similar attacks from occurring.
To Pay or not to Pay
What if you are a victim of such an attack? What next? To pay or not to pay seems the question to ask. This will be a difficult question to answer. The whole scam is designed to give the victim two equally unappealing options. You either pay the ransom or lose potentially valuable data. With the two schools mentioned above Cambria College did not pay the ransom, while the University of Calgary paid nearly 15,000 USD in order to have access to their files. Often what needs to be addressed is how important the encrypted files are to the organization or individual attacked. The University of Calgary deemed that a potential 10,000 users would have lost data and this would have been unacceptable. They went public with the knowledge in an attempt to combat this scourge by creating awareness. They also hired a data breach coach, who recommended paying the ransom, to instruct as to best practice policies to prevent further attack.
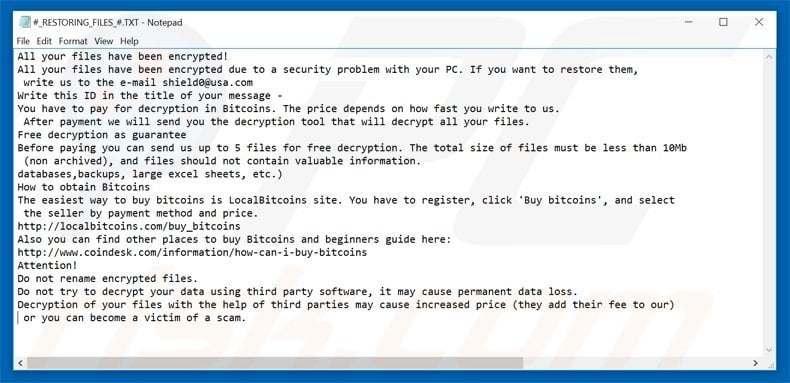
It is important to remember that even if you pay there is no guarantee that you will get access back to those encrypted files. You are not dealing with upstanding, morally informed citizens. There is also no guarantee that if you pay you will not be hit by the same cyber criminal again. If you make no changes to your security policies you will likely be hit again in a similar method with a newer version of any of the differing ransomware mentioned above. To pay or not to pay is truly a damned if you do, damned if you don’t scenario. In an ideal world, those behind the attacks would never be paid but reality is far from ideal.
As was mentioned above an educated workforce as to the threat landscape the organization or themselves as individual technology users face is the best prevention. Currently, many different cyber security companies have reported as many as 374 different types of ransomware. This will likely grow in number. The growth rate since the first versions of ransomware was detected has been exponential. Ransomware will evolve as all cyber threats do and ransomware attacks will continue to rise the more successful they are at extracting ill-gotten electronic currencies from victims. Knowing how the threat operates, is deployed, and the potential results of the attack will lead to a better-educated populace that will make far more informed decisions as for how to respond to suspicious activity and malicious attacks.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion