Verified Twitter Accounts Targeted
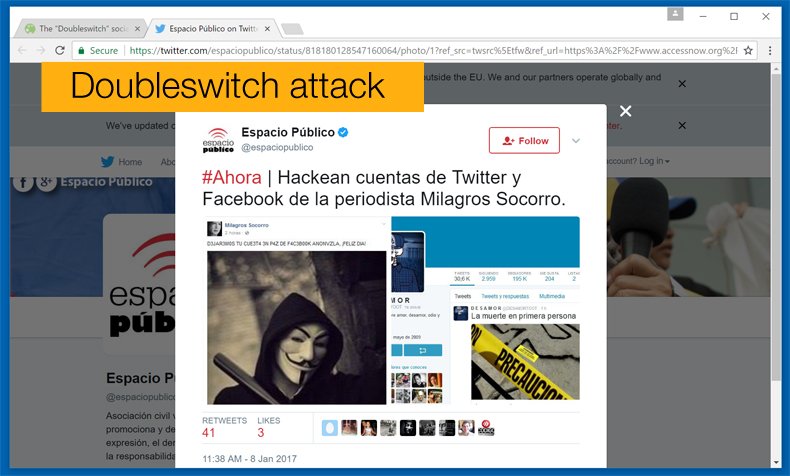
Recently verified Twitter accounts of journalists in Venezuela had been hacked in order to promulgate misinformation in the form of fake news. Recent hacks of the Qatari news agency have resulted in a massive political falling out between the small Gulf nation and its neighbors, mainly with Saudi Arabia and the United Arab Emirates, over a fake news story alleging Qatar’s involvement with Iran. This is an oversimplification of a complex situation but it does appear that the hack and subsequent publishing of fake news stories sparked the recent diplomatic feud in conjunction with President Trump’s recent visit to Saudi Arabia.
In the case of the Venezuelan journalists, their Twitter accounts were hacked in a method not been seen before in order to promulgate fake news in the hope that that misinformation will spread to the journalist's followers. This would not only negatively impact the journalist’s reputation, potentially destroying a chosen career, but also make it harder for followers to gain access to factual news in Venezuela, a government which has recently authorized censoring the internet and surveillance in a misguided method to suppress the political unrest.
While targeting journalists and human rights advocates is not new in an effort to promulgate fake news and other forms of misinformation, this method of hijacking verified Twitter accounts is new. Given how effective past fake news campaigns have been at sowing confusion, it is reasonable to assume these attacks will become more complex as we are potentially now seeing.

Hijacked Account
AccessNow a non-profit organization which looks to protect activists, journalists, organizations, and human rights defenders by providing free digital security advice and emergency assistance were informed by the above-mentioned journalists. The organization has dubbed the method attack as “Doubleswitch”. The attack begins by having your account hacked, this can be done across multiple attack vectors and it is unknown how the two above mentioned accounts were hacked. It appears though that the method probably employed is via a phishing email. This is still a tried and tested attack vector.
Once the hackers have access to your account they change your Twitter handle in a very slight way, with the hopeful result of your followers not recognizing the change. The associated email address is also changed, this has the result of effectively locking out the original account holder from their account. Even if the original user attempts to change their password, the relevant email will be sent to the changed email address. The hacker can then inform Twitter that the matter is resolved. Another fact key to the overall success of the hack is that once the handle is changed this then becomes available once more to the public.
The final step to the attack begins when the hacker creates a new account using your old handle but with their email address. This effectively locks out the original user from what was their account. The hacker can now begin to steal the user’s online identity and post whatever they deem beneficial to a greater smear campaign or disinformation campaign. As was mentioned the account cannot be retrieved via the traditional methods of changing passwords and so forth.
Recovering the Account
As can be imagined recovery of the account is made harder by not allowing for the traditional method of changing your password and following the verification procedures. Fortunately, Twitter has another method for those affected by this and similar attacks to recover their accounts. This is done through an online form sent directly to a team at Twitter which will review and investigate the incident in order to help the affected user recover their account. Often by this stage, a lot of damage has already been done to the original user's account. This makes it, rather, unfortunately, an efficient tool at smearing a reputation or spreading fake news. AccessNow assisted the two journalists mentioned above in retrieving their account in this method. This attack method does not seem able to successfully bypass two-step verification procedures. However, the attack method does not only attack Twitter accounts but can be used on Facebook and Instagram accounts as well.
While the two-step verification process might help prevent an account been hacked in such a method it is often not employed by users in Venezuela and other countries with strict internet usage rules and broad censorship of the internet. This is because many journalists, human rights defenders, and social activists are unwilling to associate personal information with mobile numbers with online accounts for fear of being spied upon.
The following is a neat summary of the attack and how to prevent it in future provided by AccessNow:
- Hijackers can permanently lock out or extend the period of time they control a social media account by changing the username, and then deleting the original account.
- The Doubleswitch attack confuses potential followers and makes the standard recovery mechanisms ineffective.
- Social media platforms typically do not notify users of changes to their usernames.
- This attack is reproducible on other social media services, including Facebook and Instagram.
In order to prevent an attack:
- Users at risk should enable multi-factor authentication to prevent adversaries from taking control of an account in the first place;
- Twitter — and social media platforms with similar account features, such as Facebook and Instagram — should update features and rules to address the Doubleswitch attack;
- To ensure a lasting solution, social media platforms like Twitter should consult with victims and relevant stakeholders while updating the policy, instead of doing so unilaterally, which may result in a short-term solution;
- Social media platforms should also implement alternative ways to authenticate users, such as app-based authenticators, which do not require a phone number to implement.
- Phone numbers can expose the identities of users and place them at greater risk.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion