Hacker Steals over 150,000 USD from ICO Participants
On a weekly basis, it appears someone gets swindled from their cryptocurrency in one form or the other. Whether Bitcoin, Ethereum, Litecoin, or Monero hackers have been quick to pounce on the new technology seemingly rewriting the rules of economics and trade. Some hackers use nasty pieces of malware while others are content merely to trick users into sending cryptocurrencies to the wrong address. In the latest instance, trickery was the name of the game. An as yet unknown attacker has tricked Experty ICO participants into sending Ethereum funds to the wrong wallet address. This was done by merely sending emails with a fake pre-ICO sale announcement to Experty users who signed up for notifications.
An ICO (Initial Coin Offering) is similar to a classic IPO (Initial Public Offering), but instead of stocks in a company, buyers get tokens in an online platform. Users can then keep the tokens until the issuing company decides to repurchase them, or they can sell the tokens to other users for Ethereum. ICOs are becoming a popular alternative to the classic IPO as it allows them to generate capital they would otherwise struggle in getting from traditional financial institutions. This is where Experty comes in by offering a service where users pay with cryptocurrencies instead of money. This was termed a blockchain-based VoIP calling system and was intended to help the company raise funds in the form of the Ethereum cryptocurrency. The notion generated a lot of interest and Inc.com ranked the Experty ICO as one of the top 10 ICOs to watch in 2018.
Users Tricked by Fake ICO Announcement Email
The brief campaign only spanned two days, those being January 26 and 27, in which Experty users who had signed up to receive notifications began to receive the fake email. In the email, users were asked to send money to an Ethereum wallet if they wanted to buy EXY (tokens provided by Experty) tokens and be part of the ICO. The email could be proved as fake as because the actual Experty ICO was scheduled for January 31, and not the week of the campaign. The email users received was not sent by the Experty team, but by a hacker. A copy of the email can be viewed courtesy of security researcher Indrajeet Bhuyan. The Ethereum wallet address in this email is not associated with the Experty team, who previously announced they would be handling sales of Experty tokens only via the Bitcoin Suisse service.
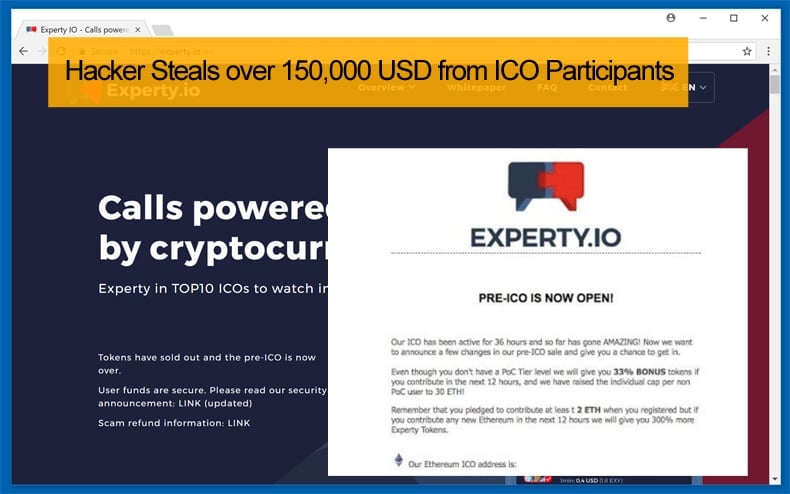
The Ethereum wallet address of the hacker currently shows that the trick has earned the person well over 150,000 USD. This amount was generated from a total of 74 transactions. However, this amount could be far higher as some of the emails had a different wallet address. Both Experty and Bitcoin Suisse are now warning users not to send money to this wallet or any other address associated with the fake emails.
Statements Released by both Experty and Bitcoin Suisse
In a statement released by Experty, the hacker was able to get his hands on this list of emails by compromising the computer of one of the people who carried out Experty's PoC (Proof-of-Care) review. Under normal circumstances, the emails of people who signed up to be notified of the Experty ICO are kept private. Bitcoin Suisse stressed in their statement that no personal information, such KYC (Know Your Customer) details, were leaked. It was also noted in the statement that users associated with Experty received emails from the following address ico.experty.bitcoinsuisse@tindie.com. These are not from Bitcoin Suisse or Experty. As such users are told in no uncertain terms to send funds to the wallet addresses provided.
In another statement released by Experty, it was stated, “We are deeply apologetic for the inconvenience this may have caused you and as a gesture of goodwill, we will be giving 100 EXY tokens to everyone who has their ETH address in our database…We are taking precautions and increasing security to ensure that this does not happen again… The Experty community is our number one priority and always has been. We will continue to work towards a safer and prosperous future, and we hope that you will be there with us.”
For those users who unfortunately sent funds to the hacker’s wallet getting those funds back will be an impossible task. Users who sent Ethereum to the hacker's wallet will not be able to get their money back. Other companies who had their ICOs compromised in the past year have offered the equivalent of their respective tokens as reparations for any incidents.
Participating in ICOs bears other Risks
In an article published in Forbes, it has become increasingly clear that ICO is a hotbed for scammers. One of the reasons for this is the lack of answers with regard to whether or even how securities law applies to ICOs. In early December 2017, Cyber Unit took its first action, against PlexCoin, which promised investors a more than 13x return within a month. Since August of that year, PlexCoin had raised $15 million from investors both in the U.S. and beyond. In order to prevent PlexCoin from swindling further Cyber Unit was granted an emergency asset freeze against Dominic Lacroix, whom it called a "recidivist Quebec securities law violator," his partner Sabrina Paradis-Royer and PlexCorps. It also filed charges against LaCroix and PlexCorps alleging that they sold securities claiming investments in PlexCoin would bring profits of 1,354% profit in less than 29 days.
While ICOs may offer a great investment opportunity investors should be wary and do their research. For instance, if an ICO does not need a blockchain infrastructure or a native token it may be a scam and alarm bells should ring. Another thing to look out for is whether the ICO is proposing open-source code and it is non-existent or empty GitHub page it would be wiser not to part with your hard-earned money. One of the universal truths behind scams is if it is too good to be true it is probably a scam and you should be wary.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion