Researchers Sink 52,000 Compromised Servers
In a collaborative effort between researchers working at Abuse.ch, BrillantIT, and Proofpoint have managed to sinkhole the command and control infrastructure behind EITest. What has been referred to as the “King of Traffic Distribution” EITest is a network of hacked servers abused by cyber-criminals to redirect users to malware, exploits kits, and tech support scams. This collection of compromised servers is used by cybercriminals to siphon off legitimate traffic from these sites and redirect users to malicious web pages. This is done by hackers installing backdoors on the servers. This type of malicious activity is called “traffic distribution” within the infosec community. It has become a major source of income for cybercriminals and those involved have gone so far as to build such botnets of hacked sites and then rent them out as a service to fellow crooks. They then do with them as they please.
The Scourge known as EITest
A quick history of EITest reads as follows. EITest first appeared in 2011 as was seen as a traditional malicious traffic distribution system. Its authors used it primarily to drive traffic towards their self-developed exploit kit known as Glazunov, which they used to infect users with the Zaccess trojan. It was never considered a massive threat. However, in 2013 the authors saw the potential behind their creation and in 2014 began renting out EITest to other malware authors. This was primarily done by selling hijacked traffic from hacked sites for $20 per 1,000 users, selling traffic blocks of a minimum size of 50,000 users, according to Proofpoint researcher Kaffeine.
In 2017 the authors behind EITest evolved once more to include the distribution of countless ransomware families, redirecting huge swaths of traffic towards the Angler and RIG exploit kits, and recently in sending waves of users towards social engineering sites. One of the latest instances of sending users to social engineering websites involved the abuse of a fake Chrome Font Pack (the details of which were published again by Proofpoint). The authors are also known to use browser lockers, tech support scams, and fake updates to redirect user traffic.
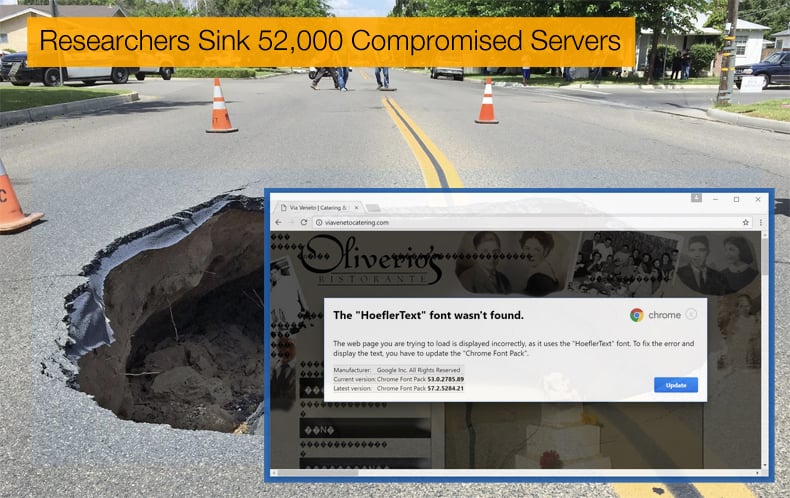
Researchers at Proof point contend that EITest is one of the oldest and largest infection chains seen. It became a daily pain for security researchers to contend with. Thus the sinkholing of the command and control servers can be seen as a definite victory for those involved in the combined effort to stop such a far-reaching campaign. By stopping EITest it has been estimated that sinkholing this infection chain disrupted over two million potential malicious redirects per day with significant implications for downstream buyers of EITest traffic.
How EITest was sunk
It was work done by researchers at BrilliantIT in early 2017 in analyzing and breaking down the code used by the EITest authors. Much of it was scripted in python and was a nightmare to analyze. This was due in part to the continually evolving complexity of the threat. In the report published by BrilliantIT, one can see how complex the threat was. The ultimate analysis conducted by researchers enabled them to determine exactly how infected sites would connect to the command and control infrastructure. This unraveling of the command and control structure proved to be vital in the sinkholing operation.
The sinkholing was done by only needing to seize one domain (stat-dns.com). By seizing this one domain they managed to hijack the entire EITest operation. After analyzing the traffic flowing into the sinkhole, researchers got an insight into EITest's massive operation, revealing that the botnet handled about two million users per day coming from over 52,000 hacked websites, most of which were WordPress sites. As to whether the sinkholing of the command and control infrastructure will spell the absolute end of those behind EITest only time will tell. Proofpoint, however, has confirmed that:
“Following the successful sinkhole operation, the actor shut down their C&C proxies, but we have not observed further overt reactions by the operators of EITest,”
It would appear that EITest’s authors have given up on trying to retake control over their former network. This does not mean that they will not create another. There are also still other traffic distribution networks still online. Those being Fobos, Ngay, and Seamless. Such sites are still seen as a viable way for cybercriminals to make money.
Traffic Distribution Systems are Definite Moneymakers
Often referred as simply TDS, such systems have the possibility of generating a lot of money for their authors. TDS has come to mean a system that is a web application that takes incoming traffic, filters it based on various criteria, and then redirects the user to a "landing page" that can be an exploit kit, tech support scam, or website pushing a fake update. This is mainly down by using malicious ads (malvertising) that secretly swoops the user off a legitimate site, then to the TDS. The second method employed to do this is by using hacked websites that redirect random users from the legitimate site to the TDS. This was the method employed by the authors of EITest.
TDS systems have evolved from being merely components of exploit kits to a major threat. In a separate report published by Proofpoint, TDS systems can now be seen as Crimeware-as-a-Service and are regularly detected in web-based malware distribution operations. In the above Proofpoint report BlackTDS, one of the newer platforms launched in December 2017, was analyzed and can be seen as TDS as Crimeware-as-a-Service evolved. BlackTDS is nothing more than a portal where cybercriminals sign up for an account. Inside, after paying the appropriate fees, they have a web panel where they can decide what type of users they want to infect based on details such as country, OS type, browser version, language settings, and time of day for example. BlackTDS customers only have to provide the final landing spot where the TDS should redirect users, making the entire operation a point-and-click experience even for the most novice crook. This ease of access is worrying as those with limited coding or hacker knowledge can now benefit from cybercrime. Schemes like this drastically decrease the skills entry point into such crime.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion