BEC Scams cost over 12 Billion USD Globally
Becoming a victim of a scam or hack is certainly a dent to one's ego. When the losses are tallied up you may wish it was just your ego that was bruised rather than your bank balance. On July 12, 2018, the Federal Bureau of Investigation (FBI) issued a public service announcement revealing the losses and potential losses caused by business email compromise (BEC) and email account compromise (EAC). According to the FBI, the total loss and potential loss amounted to over 12 billion USD between October 2013 and May 2018. The amount was calculated by including money that was actually lost by victims and money they could have lost if they had fallen for the scam. A BEC is a type of phishing attack where a cybercriminal impersonates an executive, often a CEO, and attempts to get an employee, customer, or vendor to transfer funds or sensitive information to the phisher. Unlike traditional phishing attacks, which target a large number of individuals across a company, BEC attacks are highly targeted and focussed. Cybercriminals will scrape compromised email inboxes, study recent company news, and research employees on social media sites in order to make these email attacks look as convincing as possible. This high level of targeting helps these email scams to slip through spam filters and evade email whitelisting campaigns. This making it far harder for employees to decide whether the email is legitimate or not.
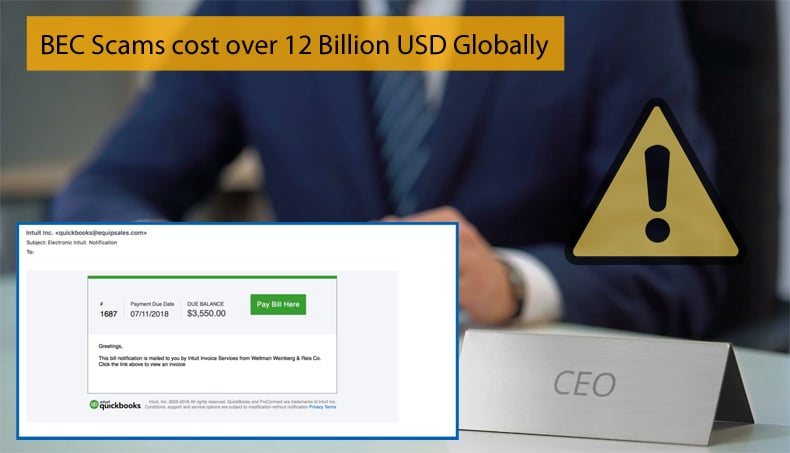
An EAC scam is incredibly similar to a BEC scam. The main difference is that an EAC scam targets individuals rather than businesses. A typical EAC scam will provide when a cyber criminal uses social engineering and other computer intrusion techniques to compromise the email accounts of unsuspecting victims. In many cases, a criminal actor first gains access to a victim’s legitimate e-mail address for reconnaissance purposes. The criminal actor then creates a fake email account that closely resembles the legitimate account, but is slightly altered by adding, changing, or deleting a character. The fake email address is designed to mimic the legitimate email in a way that is not readily apparent to the targeted individual. The criminal actor then uses either the victim’s legitimate email or the spoofed email address to get sensitive information or attempt fraudulent fund transfers.
FBI Findings
In the FBI’s investigation, it was found that such scams had been observed in 50 US states and 150 different countries, with money being sent to 115 countries. The top destinations for money generated by BEC scams are Asian banks in China and Hong Kong. That being said a significant number of this scams involve financial organizations in the UK, Mexico, and Turkey. The FBI also found that over 78,000 complaints have been made globally between October 2013 and May 2018, with over 41,000 victims reported in the United States alone. In terms of money, this amounted to a combined loss and potential loss of 12.5 billion USD, with US losses totaling nearly 3 billion USD. The worrying stat in this is that losses had increased by 136% between December 2016 and May 2018.
In 2016 the FBI releases an earlier public service announcement informing and warning of BEC scams. In that release, it was shown that for the period of October 2013 and December 2016, there had been 40,203 incidents globally with exposed losses totaling over 5.3 billion USD. In 2017, the bureau received over 15,000 BEC and EAC and reported losses for those incidents came to 675 million USD. From 2016 to 2018 the massive 136% spike in reported incidents should be a cause of concern for anyone in charge of a business’s information security.
In the latest report, it was also found that cybercriminals are increasingly targeting real estate businesses. This includes title companies, law firms, real estate agents, buyers and sellers which amounts to almost every level of a typical real estate transaction. Victims most often report a fake and suspicious email being sent or received on behalf of one of any of these real estate transaction participants. The email contains instructions directing the recipient to change the payment type and/or payment location to a fraudulent account. The funds are usually directed to a fraudulent domestic account which is then quickly dispersed through cash or check withdrawals. With the funds been withdrawn from the fraudulent account recovering of the funds is a near impossible task.
Protecting against such Scams
In an article written for Security Week by Josh Lefkowitz, CEO of business risk intelligence firm Flashpoint, detailed how businesses can defend against such scams. It is important to remember that the vast majority of BEC scams are not reliant on a piece of malware but rather social engineering. This makes it hard for antivirus solution to detect and prevent such scams from happening as such solutions are designed to detect emails containing malware and malicious links and so forth. Thus a human understanding of the threat is vital to prevent such scams.
As human education is so important in defending against these scams automated intelligence cannot be the start and end of a defense. This point is made further by the fact that the indicators of compromise (IoC) often involve analysis of the attacker’s syntax, dialect, or other behavioral characteristics. Automated intelligence offerings and traditional network security solutions are generally not designed to identify these types of IoCs, which is why human-powered intelligence and subject matter expertise are crucial to prevent a financial loss from occurring.
This means that awareness and education, and the investment in those facets, will be of more use than adopting another security solution that is not capable of defending against such threats. Traditionally, education of a workforce has been done by enterprise-wide efforts to raise awareness of BEC scams. These have been proven to help employees more accurately detect and report malicious emails and other socially engineered attacks. Often such measures adopted by a business apply equally as well to the individual.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion