Virobot Malware Emerges
A recently discovered malware strain can be seen as a Swiss Army knife. Not only can it function as ransomware it can also log and steal their keystrokes and add infected computers to a spam-sending botnet. Multi-tasking malware is by no means a new phenomenon, malware authors will look to add new components and functions to existing malware strains in an attempt to make them more versatile. While not a new phenomenon, these multi-tasking nasties have an unexpected side effect of making classification difficult. This, in turn, causes much strife amongst the InfoSec community.
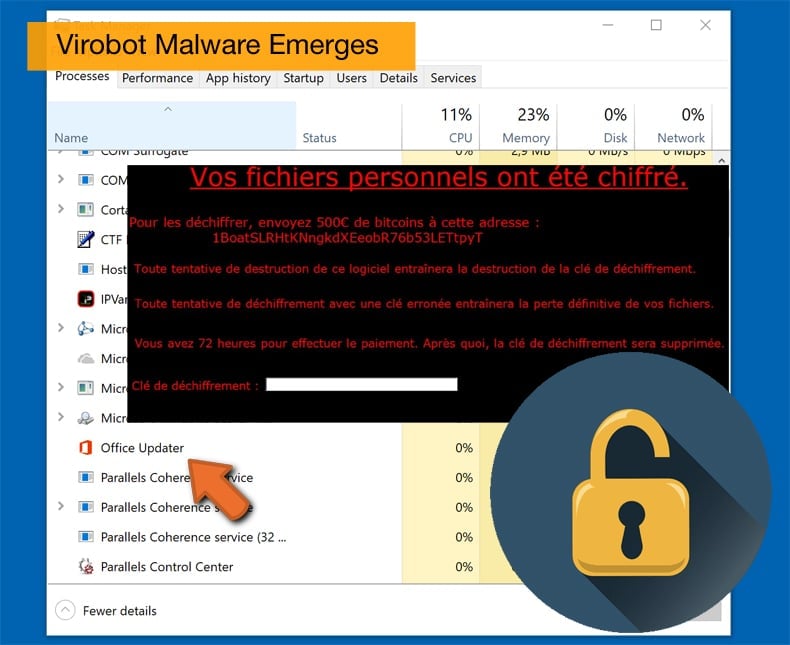
The malware, dubbed Virobot, was recently discovered by researchers at TrendMicro (sample discovered by security researcher MalwareHunterTeam). The malware which is capable of working as a botnet, ransomware, and keylogger has been classified as a ransomware strain by those same researchers, fortunately, it would appear that the malware is still under development. This is in part due to the uniqueness of the ransomware component. According to TrendMicro, the ransomware component has no ties to previous ransomware strains but that is where the uniqueness ends.
Virobot’s ransomware component operates like most ransomware variants, following the same modus operandi of all previous threats. If a user is tricked into downloading and running the ransomware attached to email documents, the ransomware will generate a random encryption and decryption key, which it also sends to a remote command and control server. The encryption process relies on the RSA encryption scheme, and Virobot will target files with the following extensions: TXT, DOC, DOCX, XLS, XLSX, PPT, PPTX, ODT, JPG, PNG, CSV, SQL, MDB, SLN, PHP, ASP, ASPX, HTML, XML, PSD, PDF, and SWP. Like with the vast majority of other ransomware variants once the encryption operation is completed Virobot shows a ransom note on the user's screen, interestingly though written in French rather than the sometimes broken English used by other strains. Researcher’s at TrendMicro found this particularly odd as Virobot was found been used in a campaign targeting users residing in the US.
The French Connection
Virobot is not the only recently discovered malware strain to boost a French connection. At the end of August, security researchers, again at TrendMicro, noticed that a ransomware strain named PyLocky, created to imitate the much more famous Locky ransomware, has also been very active in targeting France. It is important to note there appears to be no direct connection between Virobot and PyLocky. In the analysis conducted by TrendMicro PyLocky first appeared in July with almost two-thirds of PyLocky spam was being sent to victims in France, along with a number sent to addresses associated with the New Calendoa, a French territory in the South Pacific.
Ransomware campaigns are normally conducted in a tried and tested, if unoriginal way, by been reliant on a spam email campaign to infect potential victims. With PyLocky the spam email campaign was reliant on getting user’s to click and download the malicious payload, to do this it used subject headers and file names focused around invoices in the hope of getting an employee to click on it. The malicious URL contains a ZIP file which when run drops several C++ and Python libraries malware components along with the main ransomware executable 'lockyfud.exe' which is created using PyInstaller, a legitimate tool used to bundle Python applications into stand-alone executables.
An interesting facet of PyLocky is how it attempts to avoid detection. In order to avoid detection by sandbox security software, the malware will sleep for 999,999 seconds, that being eleven and a half days, if the computers visible memory is less than 4GB.
Ransomware or not?
At the moment there is no debate as to whether PyLocky is a ransomware strain or not. Matters with Virobot are not that simple in light of the multi-tasking features the malware boasts. TrendMicro not only analyzed the ransomware component but also the other components. Researchers concluded that the keylogger system was very simplistic, logging all local keystrokes and sending the raw data to the command and control server. However, the botnet component is far more powerful with the module also allowing the Virobot operator to download other malware from the ransomware's command and control server and execute it. The botnet is also capable of working as the malware’s spam module using the locally installed Outlook app to send spam to the user's contact list. Trend Micro reported that Virobot would use this module to spread a copy of itself or another malicious file downloaded from its command and control server.
Detecting Virobot can lead to problems as the ransomware component shares common detection indicators with other strains, such as appending the .ENC file extension to encrypted files, an extension used by many other strains. For now, the only reliable way to detect Virobot is the use of a French ransom note. While detection is reliant on the ransom note the threat has been temporarily mitigated because at the time of writing the Virobot command and control server was down meaning that it cannot encrypt victim’s files.
As to whether Virobot can be classified as ransomware or not, it would seem the jury is out. In a tweet by the Malware Hunter Team, they contest that it is a botnet. While this may be a matter of a person’s point of view and seem unimportant to the majority of user’s it does show how the lines between different malware strains have blurred considerably over the last couple of years. For example, malware strains such as MysteryBot, LokiBot, Rakhni, or XBash, have often come with multi-functional features, blending everything from ransomware to crypto miners in the same package.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion