Chinese Cyber Espionage Group using Datper Trojan
In a recent article published by Cisco Talos team, researchers have seen a Chinese linked cyber espionage group using the Datper Trojan. The group called Tick, who have also been called Redbaldknight and Bronze Butler in the past, have been launching espionage campaigns targeting those in Japan and South Korea for a number of years. In the campaign analyzed by the Talos team, the group also used compromised websites located in the two countries as command and control (C&C) servers.
Since 2016, Tick has developed a reputation for targeting Japan and South Korea by using custom tools for each separate campaign. Although custom tools are often used researchers have been able to uncover certain tactics employed on a near constant basis. Such tactics include similarities in the use of infrastructure and overlaps in hijacked C&C domains or the use of the same IP. Cisco researchers, knowing about the patterns, were able to determine similarities between the Datper, xxmm backdoor, and Emdivi malware families that the threat actor has used in attacks. The use of the xxmm backdoor and Emdivi malware has also been used in previous campaigns orchestrated by the group.
The Datper Trojan analyzed by researchers can execute shell commands on the victim machine, while also obtaining hostnames and drive information. However, the infection vector is yet unknown. Once on the infected machine, Datper would create a mutex object and retrieve several pieces of information from the victim machine, including system information and keyboard layout. Next, the malware attempts to issue an HTTP GET request to the C&C server. Researcher have provided a theory as to how the malware was spread. The researchers believe that the malware could be delivered via web-based assaults, such as drive-by downloads or watering hole attacks. A drive-by download operates by embedding malicious code onto a website, that code then is capable of scanning the user’s PC for security vulnerabilities while the user is visiting the website. Once vulnerabilities are detected the malware will download and install on the now victim’s PC. Watering hole attacks operate is an incredibly similar way.
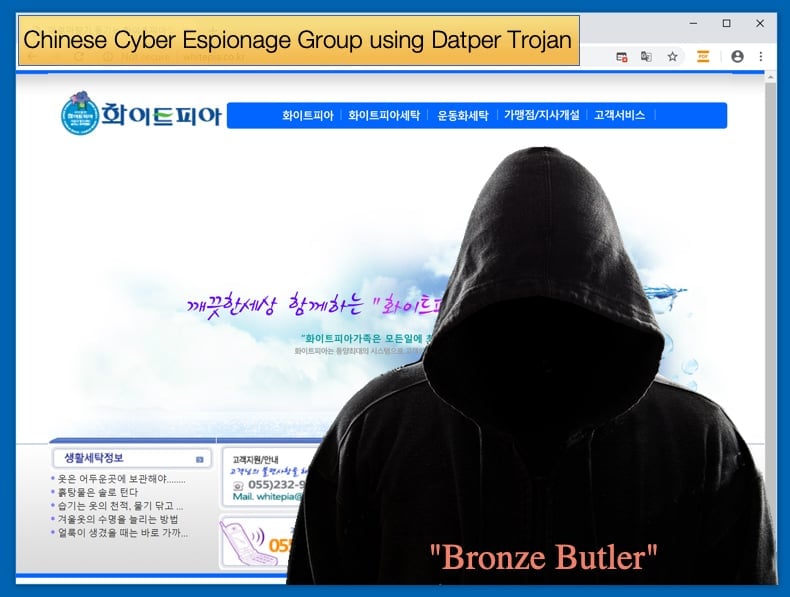
This theory regarding the attack vector is based on the researchers noticing that the analyzed Datper variant used the compromised website of a legitimate Korean laundry service to host their C&C. Located at whitepia[.]co.kr, the site does not use SSL encryption or certificates, which rendered it vulnerable to attacks. This what not the only website and C&C server used in the campaign. A number where seen been used leading the researchers to develop the drive-by download infection theory.
Talos further noticed that certain hosts were being used as C&C servers although they were not connected to compromised websites. This would suggest that the hackers initially deployed the C&C infrastructure on legitimately obtained hosts. This led researchers to conclude,
“The actor behind this campaign deployed and managed their C&X infrastructure mainly in South Korea and Japan. We confirmed that the actor periodically changed their C&C infrastructure and appears to have a history of identifying and penetrating vulnerable websites located in these countries… Talos’ investigation into attacks conducted by this actor indicates commonalities between the Datper, xxmm backdoors, and Emdivi malware families. Specifically, these similarities are in the C&C infrastructure of attacks utilizing these malware families. Some C&C domains used in these attacks resolve to hijacked, legitimate South Korean and Japanese hosts and may have been purchased by the attacker,”
Tick’s other Infamous Campaigns
In June 2018, reports began surfacing of a cyber espionage group attempting to target a secure USB drive built by a South Korean defense company. The attack was believed to be an attempt to compromise the defense company’s secure air gaped system. Air-gapping a network is a security measure employed on one or more computers to ensure that a secure computer network is physically isolated from unsecured networks, such as the public Internet or an unsecured local area network.
According to researchers at Palo Alto, the attack was an attempt to weaponize a secure USB drive. This is an attack technique uncommon for Tick, which led security researchers to the conclusion that the assault was likely aiming at air-gapped systems. The malware used in these attacks was designed to target systems running Windows XP or Windows Server 2003, which are older, out-of-support OS versions. Air-gapped systems are commonly used in many countries by governments, militaries, defense contractors, and other industry verticals in an attempt to secure sensitive often classified information.
In the report published by the researchers at Palo Alto could not determine if a compromise occurred. This is due to there was being little no compromised USB drive, the security researchers were not able to determine the manner in which the USB drives have been compromised. The researchers concluded,
“Specifically, we do not know if there has been a successful compromise in the supply-chain making these devices, or if these have been compromised post-manufacturing and distributed using other means such as social engineering,”
Tick is also known for the creation of a malware family. That malware family, dubbed SymonLoader, targets older versions of Windows. The malware once on an infected system continuously looks for these specific USB drives. When detecting the presence of a targeted secure USB drive, SymonLoader attempts to load the unknown malicious file using APIs that directly access the file system via saving the file to a temporary directory.
Advanced Persistent Threat groups like Tick may not provide a risk to the general public. They do, and can, place the geopolitical landscape under further strain. This is one of the reasons that researchers dedicate resources to tracking and analyzing the actions of such groups. When the tools of such groups reach financially motivated hacker’s hands a lot of damage can be done to the public at large.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion