Spanish Radio Station and IT Provider Struck by Ransomware
The list of high profile companies and government departments hit by ransomware infections continues to grow at an alarming rate. Last week this publication covered how the City of Joburg municipality of Johannesburg South Africa was hit by hackers demanding a ransom. Although it seems no specific piece of ransomware was used, it illustrates why hackers are looking to target companies and government departments. This week it emerged that both a Spanish IT provider, Everis an NTT DATA company, better described as a managed services provider (MSP) and Cadena SER (Sociedad Española de Radiodifusión), Spain’s largest radio station, both suffered ransomware attacks resulting in file encryption.
At the time of writing, Everis had not confirmed the attack, however, a leaked image sent to Bleeping Computer showing the ransom note displayed on Everis’ computers seems to confirm the attack. Based on the ransom note Bleeping Computer believes the specific ransomware used to be BitPaymer or a variant thereof. Further evidence of the attack also comes from the publication receiving an Everis internal communication stating,
“[Everis systems] are suffering a massive virus attack on the Everis network. Please keep the PCs off…The network has been disconnected with clients and between offices. We will keep you updated. Please, send urgently the message directly to your teams and colleagues due to standard communication problems,”
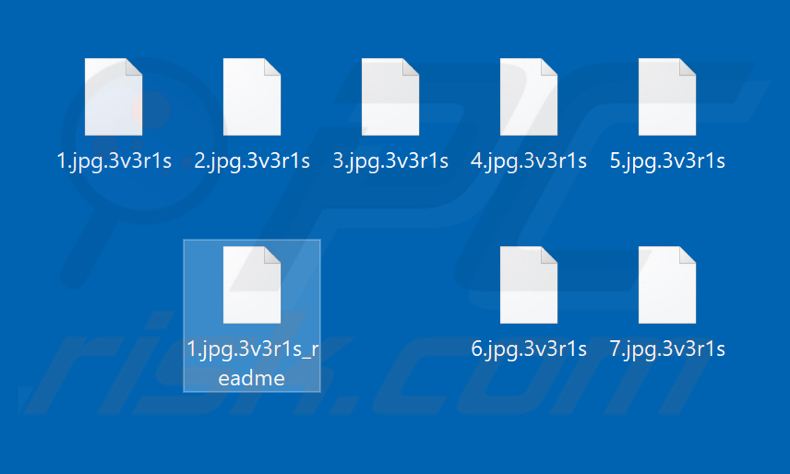
More information regarding the attack can be gleaned from the note sent to the publication which has developed a reputation for analyzing and uncovering ransomware incidents. According to the ransom, note files were encrypted with the .3v3r1s extension which indicates the targeted nature of the attack. This is also in line with modern ransomware tactics of specifically targeting large companies as well as MSPs in an attempt to target clients of the company. The note further warns against disclosing the information to the public and demanded a ransom of 835,923 USD in order to decrypt encrypted files.
Files encrypted by Everis ransomware:
Ransom demanding message shown by this ransomware:
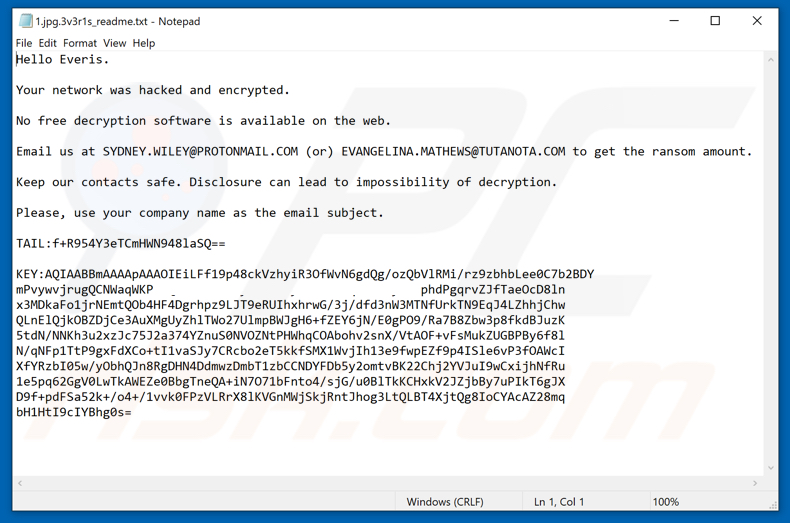
Ransom demanding message presented by Everis ransomware:
Hello Everis.
Your network was hacked and encrypted.
No free decryption software is available on the web.
Email us at SYDNEY.WILEY@PROTONMAIL.COM (or) EVANGELINA.MATHEWS@TUTANOTA.COM to get the ransom amount.
Keep our contacts safe. Disclosure can lead to impossibility of decryption.
Please, use your company name as the email subject.
TAIL:-
KEY:-
As to the attack suffered by Cadena, the radio station, it is not yet known what ransomware variants may have been used to compromise their network. Unlike Everis, Cadena did admit to the public that an attack had occurred in the form of a press release on their website. Other than that very little is known about the attack. We do know that Cadena responded by disconnect all of its computers from the Internet and it is currently continuing activity with the help of equipment at its Madrid headquarters. Spain's Department of Homeland Security (Departamento de Seguridad Nacional) also confirmed the ransomware attack that impacted Cadena SER as did Spain's INCIBE (Instituto Nacional de Ciberseguridad) who are helping restore encrypted data. The company further stated,
“The SER chain has suffered this morning an attack of a computer virus of the ransomware type, file encrypter, which has had a serious and widespread affectation of all its computer systems, The technicians are already working for the progressive recovery of the local programming of each of their stations,”
Ransomware Attacks Keep On Rolling
Readers would be forgiven for thinking that two high profile ransomware attacks are surely enough for one week. Sadly, hackers and cybercrime enterprises don’t seem to feel the same and the punches keep on coming. On November 5, news began emerging that the Canadian Nunavut government's network suffered a ransomware attack. The government department released a press release showing revealing that the incident appeared to begin over the previous weekend and that it appeared that “a new and sophisticated type of ransomware” was to blame. The statement also mentioned that all government departments, other than those in the energy sector, that rely on access to electronic information stored by the authority have been impacted. This included education, family services, medical services, as well as the government’s legal services. It is obvious that such attacks cause immense disruption and frustration, it is also important to remember that they cause a great financial loss to governments and by default taxpayers.
However, new tactics adopted by hackers and ransomware developers may make the current problem even harder to combat. As was seen with the Everis attack MSPs are fast becoming a prime target. This is primarily due to the fact that MSPs are often connected to their clients’ networks so that updates and fixes can be done often to the convenience of both the MSP and client. It is this convenience that has attracted the attention of hackers and by infecting or at least compromising the MSP they hope to infect the clients of the MSP as well.
As to the attacks affecting both the Spanish radio station and MSP, it is not yet clear if these incidents are related. The timing of both been so close to one another can lead some to speculate that they are. Cybersecurity consultant Arnau Estebanell Castellví believes this may be the case and stated in a Tweet that Orange, a telecommunications company, cut off Everis' access to the network in order to prevent the ransomware attack from affecting them.
Only once a thorough investigation is conducted will a link, if any, be determined. What is apparent is the increase in ransomware attacks targeting higher profile victims. If the hackers believe they can extort over 800,000 USD from such victims, such a payday is hard to ignore and more high profile attacks can be expected in the future. It is hoped just not at the rate they are currently happening, and the past few days are merely an anomaly.
Security researchers who want to analyze this ransomware can find it's sample of VirusTotal.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion