South Africa’s Largest City Suffers Novel Attack Demanding a Ransom
While not one of the Republic of South Africa’s capitals, Johannesburg is the country’s largest city in terms of size, populace, and GDP contribution. The city now has another less pleasant feather in its cap, the city has now experienced a novel method of cyber-attack. On October 24, the City announced that it had suffered a cybersecurity incident. Taking to Twitter, city officials announced that the municipal authority, City of Joburg, had suffered a security breach, as a result, many of the municipality’s e-services had been taken offline and residents were unable to access certain services with officials stating,
“The incident is currently being investigated by City of Joburg cybersecurity experts, who have taken immediate and appropriate action to reinforce security measures to mitigate any potential impacts. As a result of several customer-facing systems — including the city’s website, e-services and billing systems — have been shut down as a precaution.”
Soon various local news agencies including Daily Maverick and Business Live began reporting that the city was been held to ransom to the tune of 4 Bitcoins. At the time of writing the hackers’ demands amounted to approximately 37,000 USD. City employees were greeted with a note in the form of a logon screen revealing that the attackers want to go by the name Shadow Kill Hackers and which subsequently read,
“All your servers and data have been hacked. We have dozens of back doors inside your city. We have control of everything in your city. We can shut off everything with a button. We also compromised all passwords and sensitive data such as finance and personal population information.”
Traditionally ransomware attacks involve the encryption of certain file formats. The encryption process forms part of the programmed operations for a piece of malicious code. Ryuk is such a piece of malware, typically referred to as ransomware, which encrypts data and will only decrypt the data once a ransom is paid.
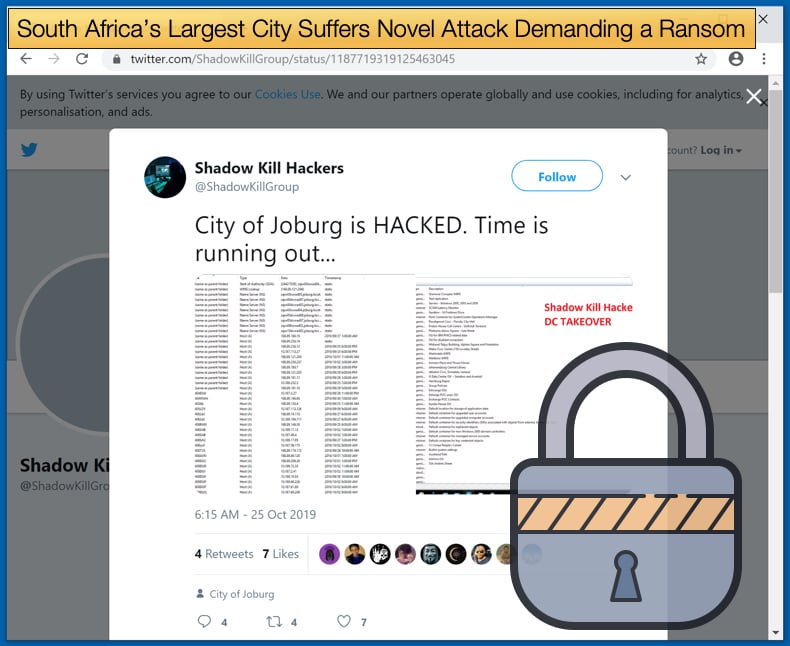
The attack conducted by the Shadow Kill Hackers does not appear to be a typical ransomware attack, nor is there any evidence of a particular piece of malware been used. Rather the hackers are demanding a ransom if the ransom is not paid the hackers will release sensitive information. The hackers state that they have backdoors to the municipalities network, but no other evidence of malware or ransomware been used to encrypt data. The hackers did post pictures of the alleged sensitive data they have to Twitter, however, it is unclear whether the data they have access to contains any sensitive data related to residents of the city. Rather than being a ransomware attack this attack is rather one of pure extortion and is been treated as one.
A spokesperson for the municipality, Nthatisi Modingoane, admitted that the hackers did gain access to locations where sensitive data is kept, however, it is not known to what extent and whether data exfiltrated. According to the spokesperson only after a thorough investigation is done will the extent of the security breach be known. The spokesperson also stated,
“We realized that something was wrong when one employee's computer's screen turned blue on Thursday afternoon. She tried to refresh and reboot the computer and then her neighbor's screen also turned blue as well as other people. We quickly spotted that we were being hacked and shut down the system. The target was at the user level which means everything in people's computers was corrupted.”
Not the First Attack the City has Suffered
The city previously suffered a cyber incident in July 2019, when a ransomware attack successfully encrypted data belonging to the municipally run electricity provider City Power. This time the attack was definitely an example of a ransomware attack as the malware encrypted the company's database, internal network, web apps, and official website. To make matters worse the encryption of data prevented customers, operating on pre-paid meters, from buying electrical power units or feeding electrical power back into the grid, which some residents are producing from solar panels. To further aggravate consumers the attack fell during the period where traditionally salaries are paid and electricity is purchased for the upcoming month.
To date little is known about what ransomware family was deployed in the attack and whether the electricity supplier paid the ransom. What was clear however is that certain consumers were left without power for over 12 hours and left angry and in the dark. It is not only South African consumers that have been left without services government departments and municipalities provide. Ransomware operators have changed tactics, once going after private users and household computers, now government departments of all shapes and sizes are been targeted. As more government services are been offered as e-services to the convenience of citizens they have also opened themselves up to attack.
An example of this occurred when Jackson County, Georgia, paid over 400,000 USD to ransomware operators so that daily operations could continue. This trend is expected to rise with more and more government departments falling victim to ransomware infections. The latest City of Joburg seems to ride on the back of this trend as although no ransomware is deployed, the hackers still look to extort funds, holding the data itself to ransom. One of the reasons government departments across the globe have come under fire is that hackers hope to better ensure payment of the ransom by one, putting a stop to daily operations, and two, only charging amount believed to less than if they were not to pay the ransom. Often calling in forensic experts is not cheap and that combined with other losses could make paying the ransom to appear more attractive. Paying the ransom is not advised as funds criminal activity and further perpetuates more ransomware infections.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion