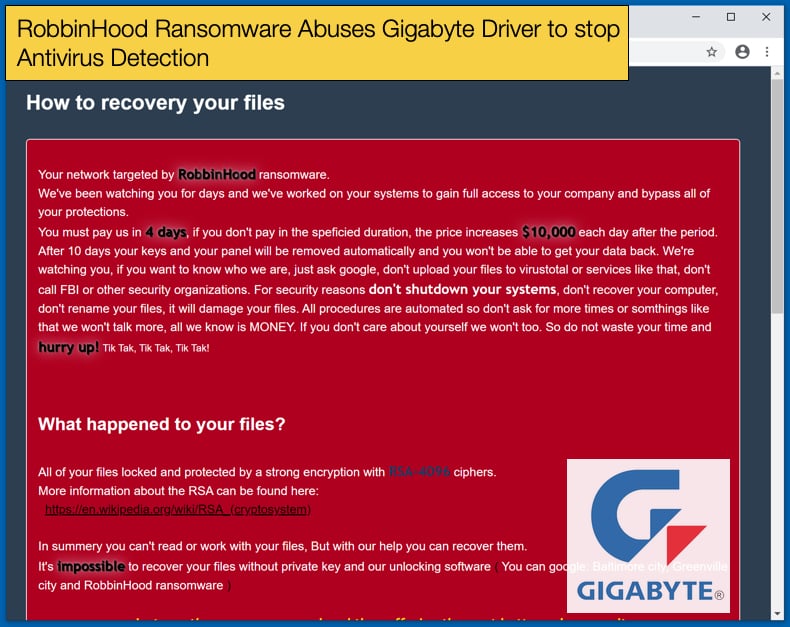
RobbinHood Ransomware Abuses Gigabyte Driver to stop Antivirus Detection
Often new developments on the malware front can be broadly defined into two categories those that involve unique methods to carry out its designed purpose and those that are not. The recent development of hackers threatening, and in some cases, releasing sensitive data to the public if ransomware ransoms are not paid would fall into the not unique category. Such developments are blunt and rather heavy-handed, especially when compared to the new and unique method that the RobbinHood ransomware employs to bypass antivirus detection so that it can encrypt files without interruption.
In two separate attacks discovered by researchers at Sophos Labs, the ransomware group was seen installing vulnerable Gigabyte drivers on computers it wants to infest along with the main ransomware payload. The purpose of installing the drivers is to allow the hackers to disable security products so the ransomware can encrypt files without being detected or stopped. According to the researchers, this method of nullifying antivirus security products has only been seen twice, with both instances also dropping RobbinHood. The ransomware is classified as a “big game” ransomware, like Sodinokibi and Ryuk, as it primarily targets large organizations, be they corporate or government organizations which are often seen as high-value targets.
The new technique is carried out over several steps starting with the attackers gaining the initial foothold onto the targeted network. Then what follows is the real heavy lifting done by the new technique, the steps are as follows:
- The attacker installs a legitimate Gigabyte driver with the name GDRV.SYS
- The attacker then exploits the privilege escalation vulnerability found on the driver to gain kernel access
- The attacker then uses the kernel access to temporarily disable the Windows OS driver signature enforcement.
- The attacker installs a malicious kernel driver named RBNL.SYS
- The attacker uses this driver to disable or stop antivirus products from running on an infected host
- Lastly, RobbinHood is then executed and file encryption begins
The vulnerable Gigabyte driver has been tracked as CVE-2018-19320 and was widely reported upon at the time. However, due to poor handling of the vulnerability by Gigabyte exploitation of the vulnerability is still possible. In summary, the company refused to acknowledge the problem existed and claimed its products were unaffected. This was despite proof-of-concept code existing that replicated the vulnerability for all to see. Rather than patching the vulnerability Gigabyte just discontinued it. Along with Gigabyte’s mishandling of the entire situation, Verisign should have revoked the legitimate certificate. If the certificate had been revoked then the vulnerability, and earlier vulnerabilities, could not have been exploited by the attacker in this method.
New Weapons Added to the Arsenal
A well-known trait of many hackers is their propensity to copy from others what has worked before. We can expect more attacks in the future that leverage this vulnerability with malware coming pre-packaged with the Gigabyte driver. For those looking to infect others with ransomware, another arrow has been added to their quiver so to speak. One more arrow on an ever-growing pile. Recently the InfoSec community has seen two other ransomware strains adopted similar techniques to stop antivirus products from detecting malicious applications. The first of which is Nemty which tried to mimic the Ransomware-as-a-Service business model to a relatively cold reception on underground forums. To try and gain traction with potential affiliates it underwent an aggressive update cycle to try and improve on the initial offering.
One of these updates was reported in September 2019 and involves the inclusion of code designed to kill processes so that encryption can occur unhindered. The code itself targeted processes associated with WordPad, Microsoft Word, Excel, Outlook, Thunderbird, SQL, and VirtualBox which is software that allows for the running of virtual machines. By targeting SQL and VirtualBox it became clear to researchers that the malware authors were targeting business and potentially looking to join the ranks of “big game” ransomware strains.
Clop ransomware is another strain that adopted similar tactics. In November 2019 it was reported that the ransomware strain was attempting to disable Windows Defender as well as remove the Microsoft Security Essentials and the now discontinued Malwarebytes' standalone Anti-Ransomware package. It attempts to disable Windows Defender by modifying Registry values to disable behavioral monitoring. This tactic would work on Windows versions before 10, as Windows 10 includes Tamper Protection designed to stop the modifying of Registry values but it must be enabled. As to the discontinued Malwarebytes product it simply tries to remove the program via a command.
A few months after the updated Nemty was reported on, another ransomware strain also included a new trick. In December 2019 it was reported that Snatch was updated to include a module which would allow for the ransomware to reboot an infected machine in Safe Mode and then encrypt files. This was the first time such a tactic had been seen in the wild and immediately garnered a lot of attention. This is mainly because most malware in circulation do not persist after a system reboots, Snatch not only persisted but carried out its main operation after rebooting. By rebooting in Safe Mode Snatch is also able to bypass detection by antivirus products.
In defending against RobbinHood and the other strains mentioned above researchers at Sophos Labs advise that user adopt strong security practices which include:
- Use multi-factor authentication (MFA)
- Use complex passwords, managed through a password manager
- Limit access rights; give user accounts and admins only the access rights they need
- Make regular backups, and keep them offsite and offline where attackers can’t find them
- Lockdown your RDP; turn it off if you don’t need it, use rate-limiting, 2FA or a VPN if you do
- Ensure tamper protection is enabled – other ransomware strains attempt to disable your endpoint protection, and tamper protection is designed to prevent this from happening
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion