Nemty Ransomware Now Spread Via Botnet
Since the operators of GandCrab ceased operations, a void in the Malware-as-a-Service sector was left open. Since proving how effective it could be to rent out ransomware as well as partner up with other cybercriminal syndicates to improve distribution, for example, other malware authors have been left looking to follow the business plan developed by GandCrab. To a greater or lesser extent, many have looked to emulate the GandCrabs notion of Ransomware-as-a-Service (RaaS), to varying levels of success. One such scheme is currently been deployed by those behind the Nemty ransomware.
First discovered by researchers in August, Nemty is new to the ransomware party currently dominated Ryuk and .STOP. This has not discouraged the malware authors, who even were quite heavily criticized on underground hacking forums. This did not discourage them it seems and the ransomware has gone through several changes and updated versions. Now they have found a new partner in helping distribute the ransomware, further helping the operators develop their RaaS business model. According to research published by Symantec, those behind Nemty have partnered with the operators of the Trik botnet, also referred to as Phorpiex, to help spread the new ransomware. Trik is a veteran malware when compared to Nemty and has been operating for at least 10 years. IN those 10 years the malware has been used to spread numerous other malware variants including GandCrab.
Trik can spread Nemty by exploiting weak credentials for systems that use the Server Message Block (SMB) network communication protocol. This SMB abusing component is Trik’s latest addition who was previously using the botnet to distribute sextortion spam mails without the use of the SMB component. It might be that Nemty is the first to take advantage of this distribution method which not only includes the SMB component but hardcoded credentials used to compromise the SMB protocol. The component works by first compromised systems to see if Nemty is not ready installed on the system, if not the malware proceeds to spread Nemty via the SMB protocol.
It appears that the spreading is done by the malware generating random IP addresses and attempting to connect to them on port 139 and then using the hardcoded credentials to gain access to the system. Once access is gained Nemty is dropped but only after the malware does another check to see if Nemty is not already on the compromised machine.
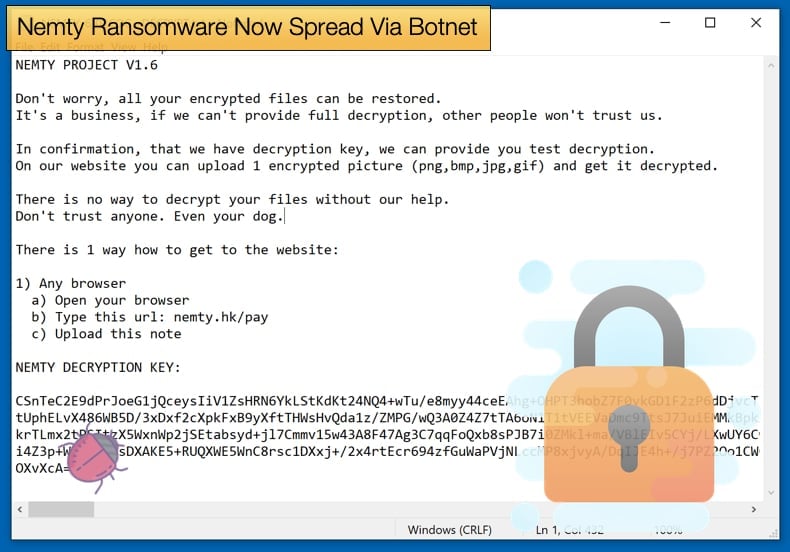
As mentioned above Nemty has gone over several updates already. The current version being spread by Trik is version 1.6. For several earlier versions, a free decrypter has been made available by security firm Tesorion. It appears that those behind Nemty are deadest on deploying the malware as a RaaS looking to get affiliates like GandCrab once did, despite early criticism the operators have stuck to the plan and by partnering with Trik interest in Nemty is expected to rise. While being a work in progress Nemty is to be taken seriously as the ransomware’s evolution suggests that the operators are continually looking for newer better distribution methods to further their less than ethical business model.
Process of Trial and Error
Despite being a product still under development the developers of Nemty have showed no small amount of tenacity in looking to break into the ransomware market. Not only do they look at better ways of distribution but look to add features making infections harder to prevent such as the backup and shadow copy features discovered by security researcher Vitaly Kremez. Further, features were added to the ransomware that would enable it to detect computers in Russia, Belarus, Kazakhstan, Tajikistan, and Ukraine. Researchers at Symantec were also quick to note that even by version 1.6 the ransomware was making use of the RIG exploit kit for distribution before switching to the partnership with Trik. While using the RIG exploit the ransomware was spread to users predominantly in Korea and China.
Even Nemty’s encryption process suggests that a lot of work has gone into the ransomware's development. Nemty uses a combination of AES-128 in CBC mode, RSA-2048, and the unusual RSA-8192 for its file encryption and key protection. Writing on the initial discovery of Nemty researchers at Fortinet noted,
“Using RSA encryption with 8192 bits of key size is very unusual. In fact, this may be the first time that we have seen a ransom malware use such strong – albeit overkill and inefficient for its purpose – encryption algorithm to protect information. In most cases, 2048 and 4096 key sizes are more than enough to secure any message. Using the longer key size adds a large overhead due to significantly longer key generation and encryption times. And lastly, RSA-8192 can only encrypt 1024 bytes at a time, even less if we consider the reserved size for padding. Since the configuration’s size will surely be more than that because it contains the encoded Private Key (from step 4), the malware cuts the information into chunks of 1000 (0x3e8) bytes and performs multiple operations of the RSA-8192 until the entire information is encrypted.”
When this is considered along with Nemty’s ability to quickly adapt it may be that a new severe threat is on the horizon. To say it may succeed in surpassing GandCrab may be a little premature, however, what is for certain is that those behind Nemty have learned many of the lessons GandCrab did. Not only have they appeared to have learned from others they have also learned from their mistakes and are quick to rectify and improve their code. Added to this they are willing to develop and try new approaches in a trial and error process to better create victims out of users. All in all, it may be that they prove how dangerous dedicated and skilled hackers are to internet users.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion