CERT France Warns of Ransomware Gang Targeting Local Government
Governments and companies are increasing lockdown measures to prevent the spread of COVID19, this has placed increase strain on governments as well as private industry. As has been seen and documented by this publication hackers and state-sponsored groups are looking to leverage the pandemic to better spread malware, exploiting people’s fears. For other gangs, it is business as usual. CERT (Computer Emergency Response Team) France has issued a warning that some local governments have been infected with a new version of Mespinoza ransomware.
The warning goes on to state that authorities believe a new ransomware gang is targeting local governments within France. The warning comes in the wake of multiple cases involving the new strain of Mespinoza seen been used in attacks within the European country. Mespinoza was first seen in the wild in October 2019, discovered by GrujaRS the ransomware would simply attach the .locked extension onto encrypted files.
The new version, referred to as Pysa, because it added the extension .pysa, was seen two months later in the wild. More on these two below. French authorities say the Pysa gang has moved to target French organizations, with the agency receiving reports of multiple infections. This is a split in previous tactics used by Mespinoza/Pysa as most of the victims were companies, suggesting that the group behind this new ransomware was specifically targeting large corporate networks in an attempt to maximize ransom demands and inherently its profits, placing the ransomware amongst other big-game hunting variants.
It is not yet clear how exactly Pysa is infecting machines but based on clues left behind following attacks investigators are beginning to develop a picture on how the gang operates. Evidence collected by CERT-FR suggests that the gang initially launches brute-force attacks against management consoles and Active Directory accounts. Once access is granted the gang will proceed to exfiltrate data relating to the target accounts as well as data associated with password databases. Previous victims also noted that unauthorized RDP connections to their domain controllers and the deployment of Batch and PowerShell scripts were detected. Further, French authorities believe the Pysa gang also deployed a version of the PowerShell Empire penetration-testing tool, to further carry out the attack.
PowerShell Empire
In the attacks mentioned above the penetration tool was used to stop various antivirus products, and even uninstalled Windows Defender in some instances. The penetration testing tool known as Empire proved a popular framework for those tasked with making networks as secure as possible. It was later to be a favored tool amongst hackers. The framework initially began development in 2015 when security researchers noted that nation-state actors began using Microsoft's PowerShell scripting language as part of their normal malware arsenals and mode of operations. The threat actors used PowerShell as a method of carrying out fileless attacks by running malware through memory without leaving a trace on the disk. These PowerShell scripts had another advantage in that they could move through networks without triggering any security alerts at the time.
To counter this problem the developers of Empire modeled their project on the architecture of malware seen in the wild. This meant that Empire would run as a PowerShell agent reliant on a command and control server for instructions. This made Empire an incredibly handy tool for security researchers and system admins to test network defenses as well as help create better detection rules for security products. Given how useful the tool became to defenders, it was only a matter of time till attackers noticed. A researcher paper published in 2018 predicted that the tool may become a favorite among attackers stating,
“PowerShell Empire is a unique attack framework in that its capabilities and behaviors closely resemble those used by current nation-state advanced persistent threat actors. That is to say that Empire is effective at evading security solutions, operating in a covert manner, and enabling attackers' total control over compromised systems. Of particular note is Empire's command and control traffic…Empire C2 traffic is asynchronous, encrypted, and designed to blend in with normal network activity. These characteristics in particular make it exceptionally difficult for defenders to identify PowerShell Empire C2 traffic in the enterprise. As such, it is likely that Empire will only increase in popularity amongst attackers, particularly as the framework continues to evolve and mature.”
This prediction came true, first nation-state actors began abusing the tool to break into networks rather than defend them. This was closely followed by cybercriminal gangs, normally financially motivated. This abuse is one of the reasons the original developers ended the project, but one positive was that security firms were made more aware of the threat. Chris Ross, one of Empire's lead developers noted,
“The original objective of the Empire project was to demonstrate the post-exploitation capabilities of PowerShell and bring awareness to PowerShell attacks used by (at the time) more advanced adversaries. We feel that we've accomplished that objective and are proud to see the security optics and improvements that have been provided by Microsoft in the past few years; in addition to the increased focus, the EDR [Endpoint Detection and Response] community has placed on PowerShell based attacks. With that in mind, the project's time has passed and newer frameworks with better capabilities have been released…So it's time to say farewell to Empire. We will not be updating or maintaining the project any further.”
Other Mespinoza/Pysa Features
Despite the original developers of Empire closing the book on their involvement, cybercriminals have been all too keen to keep the flame alive. Cybercriminals like those behind the latest Mespinoza campaign included. The use of PowerShell Empire in infecting machines is an indication that hackers will still use the penetration tool. The abuse of legitimate tools is nothing new, and neither is the abuse of encryption algorithms by ransomware operators. Pysa is no exception. Investigators analyzed the encryption process and sadly there are no weaknesses either in the encryption or the code that initiates the encryption, at least for the time being. Sometimes weaknesses can be used to create decryption keys so that victims have another option other than paying the ransom.
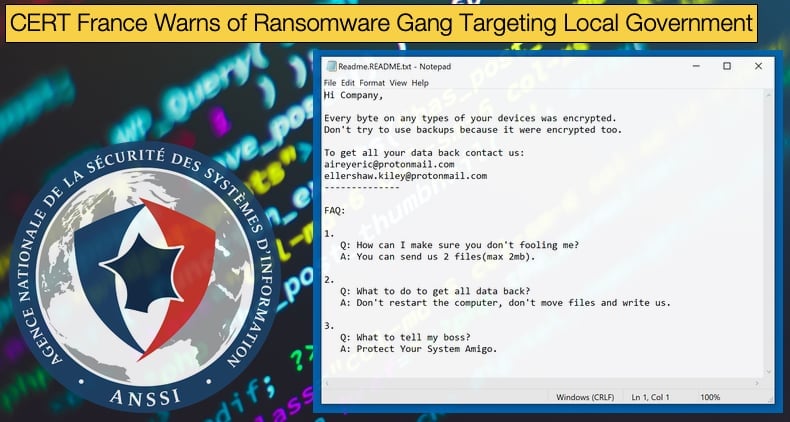
Once encryption is complete the ransom note is dropped. The ransom note, or at least one of the versions that has been analyzed, is dropped it has the file name Read.README, the contents have been reproduced below. As a side note, the differences in ransoms notes dropped on victims’ machines seem to differ only in the email addresses provided. The note reads as follows,
“Hi Company,
Every byte on any types of your devices was encrypted.
Don't try to use backups because it were encrypted too.
To get all your data back contact us:
raingemaximo@protonmail.com
gareth.mckie3l@protonmail.com
--------------
FAQ:
1.
Q: How can I make sure you don't fooling me?
A: You can send us 2 files(max 2mb).
2.
Q: What to do to get all data back?
A: Don't restart the computer, don't move files and write us.
3.
Q: What to tell my boss?
A: Protect Your System Amigo.”
According to Michael Gillespie in an interview with ZDNet it is not only local governments within France that have been targeted in this latest campaign. The gang is targeting companies and organizations across the globe. With all the evidence available it is clear that the ransomware is looking to join the big-game hunting club of ransomware. The club includes Sodinokibi, Ryuk, and Maze just to name a few. The club goes after large organizations and companies in the hope that they will get paid more. Demands can reach millions of dollars, which for some companies can be less than the costs associated with recovering from an attack.
A new term has emerged to describe ransomware operators which target organizations rather than massed home users. “Human Operated Ransomware” is defined as attacks not spread via auto-spreading tactics like massed spam email campaigns or worm-like ransomware such as WannaCry. The attacker rather specifically targets single or multiple organizations at a time but they are not reliant on trying to infect as many machines as possible. Rather, the attacker will remain on the target network undetected and slowly gain increased privileges and then chose to strike when it is best suited. The process involves the attacker to be reliant on themselves rather than just using automated programs. Often emails sent to gain a foothold on the company are specially crafted per victim using social engineering, a tactic best done by a human operator.
Whether the terms big-game hunting or human-operated ransomware are used, the result for companies and governments can be the same, devastating.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion