High Profile Twitter Users caught in Crypto Scam
Reports began emerging on July 15 that certain high profile Twitter users, including Joe Biden, Elon Musk, and Wiz Khalifa, were advertising a way to double your money if you sent an amount of cryptocurrency to a specific wallet. Claims similar to this have been seen numerous times before in several other crypto scams, where scammers look to trick or extort cryptocurrency from individuals. It was later revealed by Twitter that the actual accounts of those listed above, and several others were hacked and used to spread the scam without the knowledge of the account users.
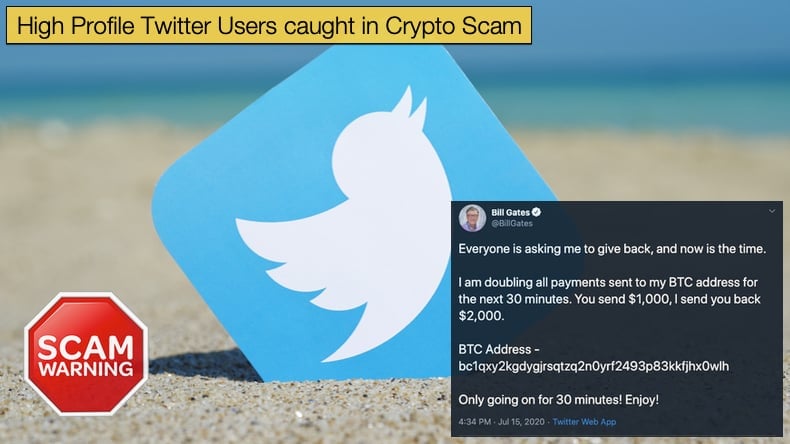
Other high profile accounts that were compromised included Kim Kardashian West, Jeff Bezos, Bill Gates, Barack Obama, Wiz Khalifa, Warren Buffett, YouTuber MrBeast, Wendy’s, Uber, CashApp, and Mike Bloomberg. Something to note is that the political figures, Joe Biden, Barack Obama, and Mike Bloomberg are all affiliated to the Democratic Party in one form or the other with Joe Biden being the current Democrat nominee set to take on the current president Donald Trump in November’s election. From a number of reports, it would seem that now Republican Party figures had their accounts compromised by the scammers. Further, Warren Buffet, a known and very vocal critic of cryptocurrencies who publicly stated that he does not own any cryptocurrency and has no plans to own cryptocurrency had his account compromised.
As to the exact details of how the scammer managed to access the accounts, very little is known. As the story is developing more information will surely surface. What reporters and the public at large do know is a comprehensive timeline for the attack. The attack seemingly began first with the scammer focusing on well-known cryptocurrency themed accounts.
These included @bitcoin, @ripple, @coindesk, @coinbase and @binance which all appeared to have been compromised at the same time with the following message being tweeted, “We have partnered with CryptoForHealth and are giving back 5000 BTC to the community,” an exceedingly generous offer, if only it was true. The message was followed by a link that was fortunately pulled down by the domains web hosting service. Twitter soon noticed something was off and opened an investigation but by this time it was clear that it was not only crypto-themed accounts that had been compromised. The initial opening of an investigation was spread to the public via the Twitter Support account which stated,
“We are aware of a security incident impacting accounts on Twitter. We are investigating and taking steps to fix it. We will update everyone shortly.”
This was followed shortly by,
“You may be unable to Tweet or reset your password while we review and address this incident.”
It was not just high profile individuals and crypto-themed accounts that fell victim to the mass account compromise. Even Apple, a company that looks to have as robust of a cybersecurity policy as possible was one of the victims. The scale of the compromise seems unprecedented. In the past, a hacker might be able to gain access to a few accounts using phished credentials and then post a message to try and con the account's followers. Often the accounts targeted will boast hundreds of thousands, or millions, of followers so only a small percentage of people need to fall for the scam and it becomes profitable. The sheer scale of the compromise in this instance means that the scammer can hit far more followers for an increased potential pay out, even if a similar or smaller percentage of followers fall for the ruse.
Sadly, people have fallen for the scam and ones before it. For example, the Bitcoin wallet associated with the scam has raked in 12.5 Bitcoin and has seen this amount increasing at a steady rate since the scam. At the time of writing, this amounted to nearly 114,000 USD. This all begs the question as to how the scammer managed to compromise all the accounts listed above and a number not mentioned. It is clear that the scammer managed to fully take over the accounts in question in order to be able to post a message as if they were the account owner but the how remains unanswered?
Twitter Confirms Internal Tools Used
While exact details are thin on the ground Twitter did announce that they believed several employees may have fallen victim to a concerted social engineering campaign that allowed the scammer to use internal admin tools to take over verified accounts. Twitter stated the following,
“We detected what we believe to be a coordinated social engineering attack by people who successfully targeted some of our employees with access to internal systems and tools…We know they used this access to take control of many highly-visible (including verified) accounts and tweet on their behalf. We're looking into what other malicious activity they may have conducted or information they may have accessed and will share more here as we have it.”
For many readers, they may feel helpless if their account was compromised in such a way. For the most part, these feelings are warranted as the fault was not of the account holders but the company charged to secure the accounts. However, users can take measures to educate themselves about such scams so as not to fall victim to them. Having an account compromised is bad, but to hand over a sum of money no matter the size expecting a return to only find out you’ve been scammed is worse. To help educate our readers a couple of previous similar scams have briefly been described below.
In March 2020, a hacker managed to broadcast a crypto-Ponzi scheme on YouTube pretending to be Bill Gates. In order to broadcast the scam, the hacker managed to hijack a number of existing YouTube accounts. The hacker then proceeded to rename the account after popular Microsoft brands with a supposed message from company founder Bill Gates. Again the scam revolved around a user sending an amount of cryptocurrency to receive double in return. Like with the Twitter scam listed above the hacker was generating thousands of dollars while live-streaming the broadcast.
Another scam, which occurred from April through to June 2020 masqueraded as Elon Musk. In the two months that the scam ran for a total of nearly two million USD was practically stolen from unwary victims. This time the wallet addresses made use of what has come to be called vanity Bitcoin address, which is essentially wallet addresses that have sections that closely resemble the holder’s name. They can be compared to personalized license plates. The addresses used were "1MuskPsV7BnuvMuHGWmmXUyXKjxp3vLZX6" and "1ELonMUsKZzpVr5Xok8abiXhhqGbdrnK5C." In total it was believed that 67 addresses featured alphanumeric similarities to the name Elon Musk were used and had received 214 Bitcoin by June when journalists began reporting on the scam. These scams are relatively low effort, in that they often don’t require the development of specialized malware and tend to use social engineering techniques.
Central to how these scams operate is the use of high-profile individuals or celebrities. If celebrities are not used then reputable companies make a good alternative. This is done to give the scam an air of legitimacy. In order for the scam to be profitable, it only requires a small percentage of people to fall for it. If these scams are carried out over a sustained period of time they can be immensely profitable as with the Elon Musk vanity address scam. Also, as the Twitter scam has illustrated, that in the space of a day over a hundred thousand dollars was practically stolen. This example did involve first compromising Twitter and then popular high profile individuals but the aim of the scam is the same. Security firm Kaspersky summarised the scam and how to avoid it rather nicely, noting,
“If you're following celebrities and executives on social media, you can't be sure that you're not following impostor accounts. The same applies to cryptocurrencies, where malicious, impersonating bots are rampant. Don't trust offers that come from Twitter or Facebook, especially if there seems to be an impossible result. Fake accounts are everywhere.
If someone on these platforms asks for even a small amount of your cryptocurrency, it's likely you can never get it back. Just because others are replying to the offer, don't assume they aren't bots, either. You have to be extra careful.”
You can find more insights on who could be behind this hack in Brian Krebs article here.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion