BlackMatter Ransomware now has a Linux Version
While classified as a new strain of ransomware BlackMatter is strongly believed to be a rebranding of the DarkSide ransomware operation infamous for the Colonial Pipeline Incident that drew far too much attention to the gang. BlackMatter is more than a rebranding and does boast some unique features, including the capability of targeting Linux machines. This appears to be an ever-increasing trend amongst other ransomware gangs seeing the potential is not just targeting Windows machines.
According to a recently published report by Recorded Future, researchers have analyzed both Windows and Linux variants of the ransomware. The Windows variant appears to have been created by an experienced ransomware operator, the malware has several obfuscation and anti-analysis techniques within the code.
While the Linux version is capable of targeting network-attached storage (NAS) devices, an increasing trend amongst other ransomware gangs. Both versions are being offered through the developer’s ransomware-as-a-service model to its trusted affiliates.
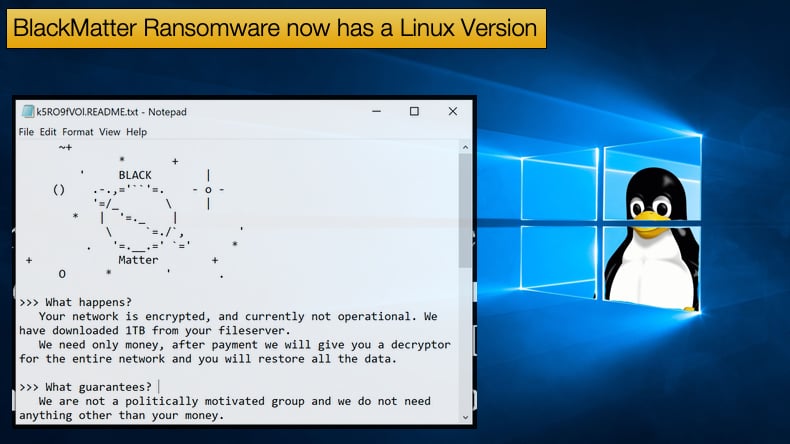
The Windows version is being advertised by the developers as version 1.2 and if the advert is to be believed the ransomware will work on Windows Server 2003 through 2021, Windows 7 and newer. That is not all, the ransomware is available in executable form, Reflective DLL, and PowerShell.
Regarding the obfuscation methods, one of the primary techniques employed is by obfuscating values. Three critical values are hidden behind junk code and include imported function calls, strings used by the ransomware, and configuration information essential to the encryption process. Commenting further on the anti-analysis techniques employed, researchers noted,
“Although the import obfuscation technique is somewhat simple, the technique makes it difficult for a reverse engineer to directly view which library functions are being called at what point. Instead of directly calling the exported function from the DLL, which would make the call target plainly visible, the ransomware calls code at an address, that XORs two values together to compute the address of the call: one that depends on the function it wishes to call, and the other is 0x22065fed. Similarly, the string obfuscation technique is also XOR-based and uses a rolling XOR seed over 4-byte chunks of the encrypted text…For configuration data, including the C2 information and the list of services the ransomware looks to stop, a second deobfuscation routine is performed, followed by a base64-decode of the data.”
When it comes to encrypting data the ransomware will stop the following processes: encsvc, thebat, mydesktopqos, xfssvccon, firefox, infopath, winword, steam, synctime, notepad, ocomm, onenote, mspub, thunderbird, agntsvc, sql, excel, powerpnt, outlook, wordpad, dbeng50, isqlplussvc, sqbcoreservice, oracle, ocautoupds, dbsnmp, msaccess, tbirdconfig, ocssd, mydesktopservice, and visio. Services stopped includes: mepocs, memtas, veeam, svc$, backup, sql, vss.
The Windows variant will also provide the attacker the ability to encrypt logical drives and network shares attached to the victim’s machine. Once the encryption process is completed the system is then booted in normal mode with the victim’s wallpaper now being the ransom note.
Linux Variant
Based on the research published by Recorded Future the Linux variant may still be in the early phases of development. According to researchers, the ransomware has several log messages, including those providing the name of the function in which they are present, and it contains several ESXI-targeted functions suggesting either that the discovered version is in early development or what was discovered was an early version.
In terms of operation and functionality, the Linux version is eerily similar to the Windows version. Like with the Windows version many of the same obfuscation techniques are applied including obfuscating key values.
When it comes time to execute the encryption routine the malware will first stop running virtual machines, excluding those on the “ignore list” in the configuration file. Interestingly VMWare was one of the virtual machines listed in the ignore list. However, when it comes time to kill processes VMWare’s Syslog process is stopped.
For the attacker to receive important victim information including the hostname, operating system, username, architecture, and disk information it creates what has been termed a “web reporter” that exfiltrates this data. Later, the ransomware will also report information about the encryption process, such as execution time, start time, how many files were encrypted, and bot version information. Regarding the encryption of data researchers noted,
“There are several configuration parameters related to encryption, including the mode (single or multiple), encryption size (dark size), white size, and minimum size. The ransomware specifically targets files with the extensions vmdk, vmem, vswp, and log per the configuration file…Ultimately, the Linux version of the ransomware has similar functionality to other ransomware variants made to target ESXI systems, but an assessment of potential code overlap is ongoing.”
To protect systems from the Linux variant before the developers start marketing it aggressively researchers have provided several mitigation strategies. Including having a comprehensive backup policy and properly segmenting the network to prevent and slow propagation in the event of an attack.
Remote access protocols should be implemented with two-factor or multi-factor authentication. Administrators should also monitor for suspicious file modification activity. Other measures include:
- Cobalt Strike is frequently used by both criminal and state-sponsored threat actors, including many ransomware operators, both to gain a network foothold and for lateral movement. Defenders should monitor for Cobalt Strike C2 servers.
- Consider keeping sensitive client information on systems that are disconnected from the internet or segmented from the rest of the corporate network. Since ransomware will encrypt all files on a victim system and often will search for directories on the network (eg: networked file shares) to also encrypt, moving highly sensitive customer data to a system with no internet access or access to the rest of the network will minimize the access ransomware would have to those files.
DarkMatter’s Rise
The stir caused by the Colonial Pipeline Incident resulted in a lot of unwanted attention for those involved with DarkSide, from affiliates to developers. Much of the attention garnered was from exactly the type of people hackers want to avoid, government officials and law enforcement.
This attention most certainly had a negative impact on business as the FBI managed to recover the vast majority of the Bitcoin handed over as the ransom. Further it was reported that much of the gang’s infrastructure was seized by an unknown third-party. The third party could be law enforcement who have the resources to do so but other theories are still readily available online as to who was responsible.
Like many businesses, losing large parts of their revenue and infrastructure the result is hanging the closed sign permanently over the organization’s door. Given the returns that ransomware gangs can achieve and the “career opportunities” that ransomware-as-a-service can offer unless hackers are arrested and face stiff legal penalties, they pivot to develop new malware strains, a new name and begin advertising once more on underground forums.
This seems to be exactly what some of DarkSide did. Towards the end of July 2021, reports began emerging that a new ransomware was being detected targeting corporate networks. It was further discovered that the ransomware, now called DarkMatter, was being advertised as a ransomware-as-a-service on underground forums. The ransomware was advertised to potential affiliates as combining the best of DarkSide, LockBit, and Sodinokibi.
In attacks seen by researchers involving BlackMatter ransoms as high as 4 million USD were being demanded. Researchers also discovered that the encryption routines used by BlackMatter were the same as those used by DarkSide previously. Namely the use of both RSA and Salsa20 algorithms.
Several other similarities, less significant, but similarities between the two were also found including similar craving of media attention and similar color themes for their TOR sites. Lastly, in the adverts posted by BlackMatter developers, the group stated that it will not target the oil and gas industry. The same industry that led to DarkSide’s fall from grace.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion