LockBit Now Boasts a Linux Version
In the second half of 2021, this publication covered the emergence of a Linux variant of the BlackMatter ransomware. The group behind the ransomware strain would make the news again when the group behind BlackMatter would cease operations following a law enforcement crackdown on several ransomware gangs and their infrastructure for high profile attacks conducted earlier in the year.
Now, new research suggests those behind the LockBit ransomware have taken a page out of BlackMatter’s book and developed a Linux variant of their ransomware. It is a pity they did not take the cease operations page out of BlackMatter’s book.
According to research published by Trend Micro, LockBit which has been incredibly active for much of the past year, has developed additional Linux and VMware ESXi variants to broaden their already formidable toolset.
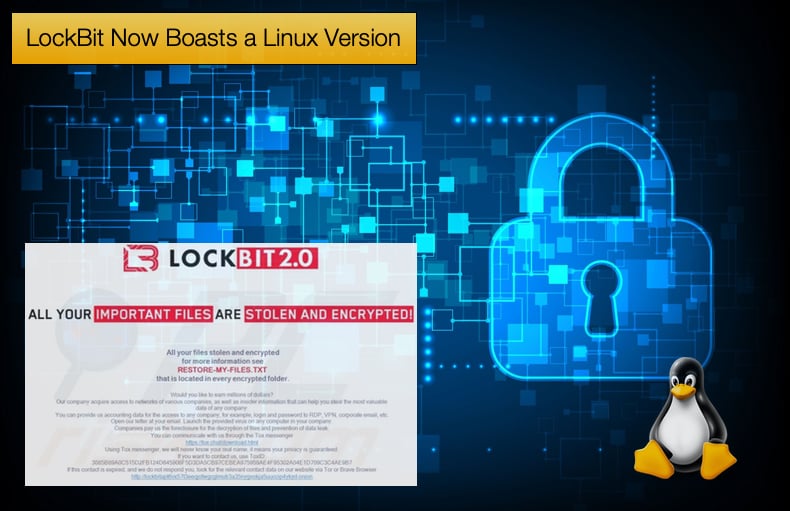
Further, researchers discovered that the LockBit Linux-ESXi Locker version 1.0 in question is actively being advertised on an underground forum. As it stands LockBit and subsequent variants have developed a reputation for erring to the sneaky side, with detections happening too late and only once the data encryption process is well underway.
It is feared that LockBit Linux-ESXi Locker can now spread the potential attack to a larger surface area within an infected network to include a wider variety of servers and data stored within virtual machines. This will further place increased pressure on victims to pay the ransom.
In August 2021, LockBit re-emerged with a new version, handily dubbed LockBit 2.0, which was advertised as being much improved and much faster than the previous version on underground hacker forums. Now, LockBit Linux-ESXi Locker version 1.0 is advertised to be as fast as LockBit 2.0 according to the ransom note dropped on victims’ machines.
The ransom note also includes information pertaining to the leak sites where the LockBit group threatens to publish stolen information, also known as the double extortion tactic and ends with a recruitment ad for potential insiders enticing them with “millions of dollars” in exchange for access to valuable company data.
The new Linux variant includes a number of interesting features to help enable it to Linux machines. These include a logging module that can capture information pertaining to:
- Processor information
- Volumes in the system
- Virtual machines (VMs) for skipping
- Total files
- Total VMs
- Encrypted files
- Encrypted VMs
- Total encrypted size
- Time spent on encryption
The malware also contains several commands necessary for encrypting virtual machine images hosted on ESXi servers. Researchers further noted as to the new variants potential impact,
“ESXi offers organizations an easier way to manage their servers. But ransomware operators are also mirroring the transition of organizations to platforms such as ESXi. This development adds LockBit to the list of ransomware families capable of targeting Linux hosts in general and the ESXi platform in particular…The release of this variant is in line with how modern ransomware groups have been shifting their efforts to target and encrypt Linux hosts such as ESXi servers. An ESXi server typically hosts multiple VMs, which in turn hold important data or services for an organization. The successful encryption by ransomware of ESXi servers could therefore have a large impact on targeted companies. This trend was spearheaded by ransomware families like REvil and DarkSide.”
Data Breaches Related to Ransomware Doubles
According to the Identity Theft Resource Center’s (ITRC) 2021 Annual Data Breach Report the overall number of data compromises totaling 1,862 is up more than 68% compared to 2020 which saw a total of 1,108. Out of the 1,862 compromises, 1,600 of those were cyberattacks.
More worrying statistics showed that ransomware-related data breaches have doubled in each of the past two years. It is estimated at the current rate, ransomware attacks will surpass phishing as the number one root cause of data compromises in 2022, according to researchers.
Given that LockBit is one of the known ransomware families to steal and release victims’ sensitive data and that the ransomware is one of 2021’s most active families it is little surprise the stats above reflect this reality.
Now that more variants are including the capabilities to target both Linux machines and VMware ESXi for Linux Server management the trend of ransomware attacks being responsible for data breaches will continue.
One question that needs to be answered is why are ransomware gangs, who were traditionally focused on infecting Windows machines given Window’s dominance of the business sphere, turning to target Linux machines as well?
One reason is that research conducted in 2019 showed that Linux Webservers effectively powered the Internet with Linux web servers amounting to 74% of the active web running Linux over other popular operating systems. Given the increased adoption of cloud computing by businesses and organizations this percentage may be even larger now.
Further, given the low number of security applications available for Linux-based machines detection is left up to the organization and hackers are constantly looking for security vulnerabilities in what effectively remains a community-developed open-source operating system.
It is also important to note that many Linux web-servers will likely contain vast databases full of sensitive data ransomware gangs are just waiting to steal in order to provide an added revenue stream and apply more pressure to pay the ransom. Given these realities, more and more ransomware gangs will also target Linux as a means to make potentially millions of dollars.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion