AcidRain Wiper Joins the List of Modern Wipers
This publication has covered how malicious malware called wipers have seen an uptick in use following the start of the Ukrainian war. Several new wipers have been discovered since the outbreak of war. Following these discoveries, the FBI warned that satellite communication infrastructure was coming under increased attack. The warning was not without incident as Viasat routers were rendered practically useless following a cyber incident.
Now, new research published by Sentinel Labs links the attack on Viasat infrastructure to the use of a new wiper.
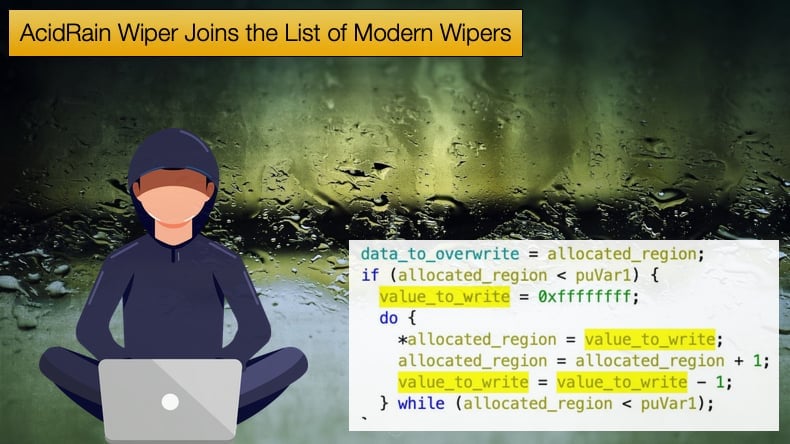
According to the security firm, the new wiper, called AcidRain, is the seventh new wiper discovered since the conflict began. To this extent and how the general public has perceived the cyberwar so far, researchers noted,
“The Russian invasion of Ukraine has included a wealth of cyber operations that have tested our collective assumptions about the role that cyber plays in modern warfare. Some commentators have voiced a bizarre disappointment at the ‘lack of cyber’ while those at the coalface are overwhelmed by the abundance of cyber operations accompanying conventional warfare. From the beginning of 2022, we have dealt with six different strains of wiper malware targeting Ukraine: WhisperKill, WhisperGate, HermeticWiper, IsaacWiper, CaddyWiper, and DoubleZero. These attacks are notable on their own. But there’s been an elephant in the room by way of the rumored ‘satellite modem hack’. This particular attack goes beyond Ukraine.”
What is referred to in the above quote as a “satellite modem hack” resulted in not only the outage of modems but nearly 6,000 wind turbines across Germany were rendered useless as remote monitoring and control systems reliant on a modem connection were impacted.
The strike on Viasat modems happened in conjunction with Russia’s invasion, this led to much speculation as to who was responsible and many believed Russia was responsible and the impact on the wind turbines was attack spillover.
Much of the speculation continued until March 30, then Viasat issued a statement to help explain what occurred. Regarding the attack the company stated,
“Subsequent investigation and forensic analysis identified a ground-based network intrusion by an attacker exploiting a misconfiguration in a VPN appliance to gain remote access to the trusted management segment of the KA-SAT network. The attacker moved laterally through this trusted management network to a specific network segment used to manage and operate the network, and then used this network access to execute legitimate, targeted management commands on a large number of residential modems simultaneously. Specifically, these destructive commands overwrote key data in flash memory on the modems, rendering the modems unable to access the network, but not permanently unusable.”
Sentinel Labs Analysis
Viasat’s statement did little to end the speculation as no incident report had been published however, researchers were able to glean a few details from the statement. These details include:
- Could be pushed via the KA-SAT management segment onto modems en masse
- Would overwrite key data in the modem’s flash memory
- Render the devices unusable, in need of a factory reset or replacement but not permanently unusable.
These three details led to Sentinel One researchers formulating an alternate theory for what had happened. Their theory involves the threat actor using the KA-SAT management mechanism to conduct a supply-chain attack.
Then the attacker pushed a wiper designed for modems and routers. The wiper designed for this kind of device would overwrite key data in the modem’s flash memory, rendering it inoperable and in need of reflashing or replacing. Viasat would later confirm that this analysis is accurate.
Researchers were then able to link what they had found regarding the wiper to an earlier oddity they had discovered in the middle of March that was uploaded to VirusTotal. As to AcidRain’s functionality, researchers noted,
“AcidRain’s functionality is relatively straightforward and takes a bruteforce attempt that possibly signifies that the attackers were either unfamiliar with the particulars of the target firmware or wanted the tool to remain generic and reusable. The binary performs an in-depth wipe of the filesystem and various known storage device files. If the code is running as root, AcidRain performs an initial recursive overwrite and delete of non-standard files in the filesystem.”
Despite the recent surge in variants of wiper malware, including, AcidRain, they are relatively rare malware strains. Ones that target Internet of Things devices like modems are even rarer.
VPNFilter is the best example of this. Researchers have noted that there is an interesting code overlap between the two malware strains. The code overlap is interesting but nothing conclusive in linking the two malware strains with any certainty.
In conclusion, Sentinel One noted that there are still many questions needing answering, particularly given the seriousness of the case. As Sentinel Lab believes the attack involved the deployment of AcidRain to render the modem unusable, at least temporarily, several inconsistencies still need to be ironed out.
One of these is the potential link between AcidRain and VPNFilter. Sentinel Lab’s researchers have asked the broader InfoSec community in helping bring more light to the matter.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion