Black Basta: Ransomware’s Newest Gang
In what can only be described as a meteoric rise to prominence, the Black Basta ransomware gang is believed to be behind 12 separate attacks in only a matter of weeks. The first known Black Basta attacks seemed to have occurred in the second week of April 2022. Further, it appears as if the gang is not focussing its efforts on one single region as victims are reporting instances worldwide.
As it would appear based on Bleeping Computer’s article the gang is certainly in its infancy. There appears no effort currently to advertise the malware or hire affiliates on underground hacking forums.
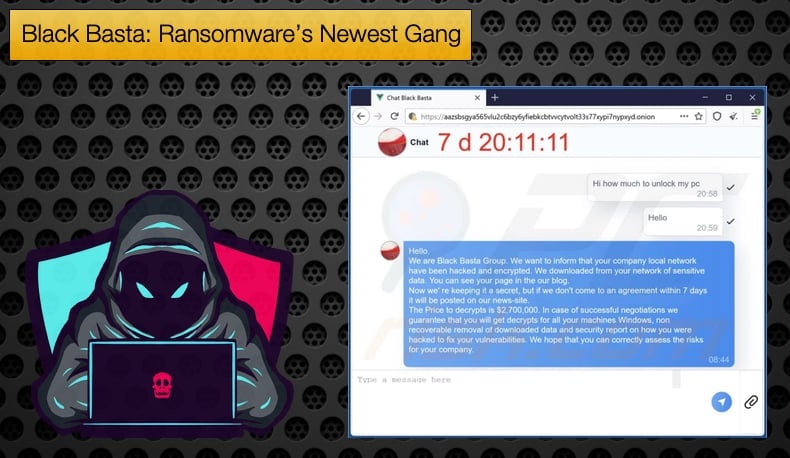
This has led to some speculation that Black Basta is a rebranding of already popular ransomware with affiliates already on board. This view can be supported by Black Basta’s ready adoption of the double extortion tactic complete with a website used to announce victims and leak data of those victims refusing to pay the ransom.
As to ransom demands, information on the ground is still relatively sparse, but sources for Bleeping Computer have stated that in at least one instance 2 million USD was demanded by ransomware operators for decrypting data and not leaking data stolen before encryption.
As for the malware, a few discoveries have been made by Michael Gillespie and the Malware Hunter Team along with Lawrence Abrams of Bleeping Computer. Abrams’ analysis revealed that,
“Like other enterprise-targeting ransomware operations, Black Basta will steal corporate data and documents before encrypting a company's devices…This stolen data is then used in double-extortion attacks, where the threat actors demand a ransom to receive a decryptor and prevent the publishing of the victim's stolen data…The data extortion part of these attacks is conducted on the 'Black Basta Blog' or 'Basta News' Tor site, which contains a list of all victims who have not paid a ransom. Black Basta will slowly leak data for each victim to try and pressure them into paying a ransom.”
At the time of writing the leak site contained data belonging to at least 11 different companies. It is believed that there are more as some companies have not disclosed attacks possibly related to Black Basta operations. It was further discovered that the Black Basta encryptor needs to be run with administrative privileges, or it will not encrypt files.
Once launched, the encryptor will delete Volume Shadow Copies. It will then hijack an existing Windows service and uses it to launch the ransomware encryptor executable. In Bleeping Computer’s analysis, Microsoft’s Fax Service was hijacked for this purpose.
The ransomware will also change the wallpaper to display a message stating, "Your network is encrypted by the Black Basta group. Instructions in the file readme.txt."
In Michael Gillespie’s analysis, the encryption routine was discovered to be the ChaCha20 algorithm. The ChaCha20 encryption key is then encrypted with a public RSA-4096 key included in the executable. Files encrypted by the ransomware will have .basta appended to the end of the filename name.
In each folder on the encrypted device, the ransomware will create a readme.txt file that contains information about the attack and a link and unique ID required to log in to their negotiation chat session. As for negotiations these are held on another Tor website titled “Chat Black Basta”.
Unfortunately, those looking for a freely available decryptor are out of luck as the encryption routine is solid meaning that there is no current way to decrypt data without paying the ransomware if backups weren’t sufficient to restore business operations.
Malware Hunter Team is of the opinion that Black Rasta is a rebranding of the Conti Ransomware. Conti has come under increased scrutiny of late which is far from ideal for ransomware operators to continue safely turning a profit. Malware Hunter Team listed the following similarities between the two operations:
- The leak site feels too similar to Conti's.
- The payment site is also very similar.
- How their support people talk to victims is also basically same.
- How their support people behave is also reminiscent of Conti.
Scalps
As mentioned above Black Rasta has already been busy claiming scalps despite only being active for a few weeks. One such scalp is believed to be the American Dental Association (ADA). According to Bleeping Computer,
“This outage is causing online services to be inaccessible, including the ADA Store, the ADA Catalog, MyADA, Meeting Registration, Dues pages, ADA CE Online, the ADA Credentialing Service, and the ADA Practice Transitions. The company has also resorted to using Gmail addresses while its email systems are offline…When BleepingComputer reached out to ADA for comment about the attack, we were told that they were just suffering technical issues and were investigating the cause of the disruption.”
However, Bleeping Computer received an email sent to ADA members in response to the attack which stated,
“On Friday, the ADA fell victim to a cybersecurity incident that caused a disruption to certain systems, including Aptify and ADA email, telephone and Web chat. Upon discovery, the ADA immediately responded by taking affected systems offline and commenced an investigation into the nature and scope of the disruption,”
Following this Black Basta began posting leaked data allegedly belonging to ADA. The data leak site claims to have leaked approximately 2.8 GB of data, which the threat actors state is roughly 30% of the data stolen in the attack.
This data includes W2 forms, NDAs, accounting spreadsheets, and information on ADA members from screenshots shared on the data leak page.
It is important to note that the leaking of dentists' information can be particularly damaging, as small dental practices typically do not have dedicated network security let alone network admins to monitor the data stored.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion