Sodinokibi Rises Again on the Back of Geopolitics
Back in October 2021, this publication covered how Sodinokibi operations were ceased following Russian law enforcement seizing the ransomware gangs infrastructure. Now following the Russian invasion of Ukraine, Russian and US officials are no longer collaborating on fighting cybercrime. This has now left the door open for Sodinokibi, also tracked as REvil, to make a comeback.
The story so far is somewhat long and convoluted so a quick history lesson is probably in order. In the middle of October, it was reported that the Tor websites used by the gang had been hijacked.
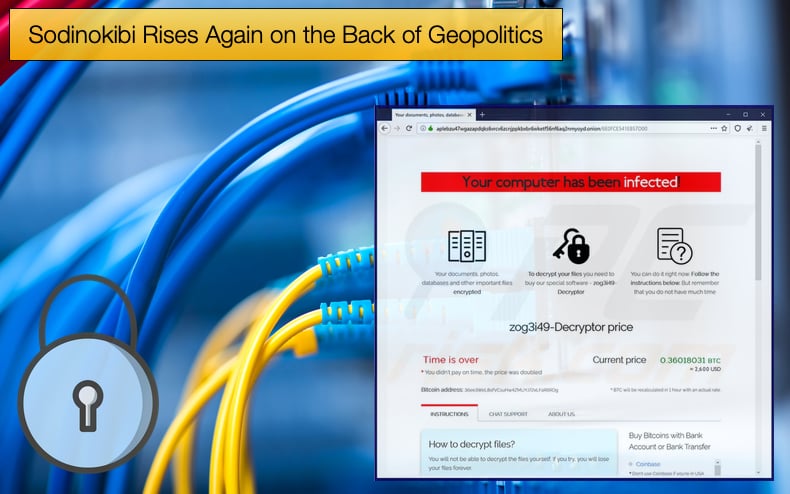
The websites that were down included both the payment portal and the data leak website used to both announce victims and leak their data.
Security researchers discovered that the sites were down following an announcement by an affiliate on an underground hacking forum.
At the time there was no evidence to prove who was behind the hijacking but law enforcement was believed to have been involved following a collaboration between Bitdefender and US law enforcement agencies to develop a free decryptor for Sodinokibi victims.
Other Sodinokibi operators tried to bring the websites and operations back online but were yet again hampered.
In January 2022 it was reported that Russian law enforcement stepped up operations against the ransomware gang.
This “stepping up” of operations can be seen as somewhat of an understatement as not only were arrests made but 66 million USD was seized from the gang's operators. Russia’s Federal Security Service stated,
“The basis for the search activities was the appeal of the competent US authorities, who reported on the leader of the criminal community and his involvement in encroachments on the information resources of foreign high-tech companies by introducing malicious software, encrypting information and extorting money for its decryption…As a result of the joint actions of the FSB and the Ministry of Internal Affairs of Russia, the organized criminal community ceased to exist, the information infrastructure used for criminal purposes was neutralized”
In total 14 individuals were arrested and both fiat currency and cryptocurrency were seized. Russian authorities also confiscated 20 luxury cars purchased with money obtained from cyberattacks, computer equipment, and cryptocurrency wallets used to develop and maintain the ransomware as a service (RaaS) operation.
The arrest of Russian individuals follows the arrest of Ukrainian individuals associated with Sodinokibi by US law enforcement along with the arrests of two Romanians by Romanina law enforcement in November 2021.
With such a sustained effort many security researchers saw the return of Sodinokibi as highly unlikely.
Back…again
On April 7, 2022, the Russian news agency TASS reported that,
“Washington announced that it unilaterally shuts down the communication channel on cybersecurity with Moscow, Russian Security Council Deputy Secretary Oleg Khramov said in an interview for Rossiyskaya Gazeta Thursday…He noted that, after the elimination of the REvil hacker group in February this year, Russia sent its proposals to the White House on the development of joint measures on the defense of both countries’ critical infrastructure. According to the official, prior to that, Russia and the US exchanged a list of critical infrastructure within the "Kremlin - White House" joint group under the aegis of the Russian Security Council and US National Security Council.”
Further, Russian Security Council Deputy Secretary Oleg Khramov noted,
“...according to its military doctrine, US cyber command and cyber forces may use information and communication technologies to carry out pre-emptive strikes on critically important objects. The US also has "cyber bases" abroad, the official said, such as the National Security Agency (NSA) headquarters in Hamburg, where, "outside of Germany’s jurisdiction, apparently, hundreds of professional hackers are working tirelessly for US’ interests," or like NATO cyber operations centers in the Baltics”
Given that Russian news agencies report directly to the Kremlin statements as to what the US will do as a result of quitting the cooperation between the two states, while possible, still require numerous facts to prove true.
However, what is certain is that the ending of cooperation between the two states regarding the crackdown on cybercriminals definitely leaves space for said criminals to take advantage of.
On April 20, 2022, reports emerged that Sodinokibi’s Tor websites were online once again, but were redirecting visitors to URLs for an as-yet-unnamed ransomware operation. The new websites included a list of old Sodinokibi victims as well as some new including Oil India.
Following this discovery a few days later security researchers discovered that the websites were being promoted on underground hacking forums. While this suggests that Sodinokibi had returned, security researchers needed a new malware sample to prove this is the case.
Jakub Kroustek, a security researcher for Avast, discovered a new malware sample of Sodinokibi. What was discovered by Kroustek was a new patched executable based on, but importantly not, the original source code.
This code includes new changes not previously seen in other malware samples and goes a long to prove that the Sodinokibi gang is back at it. The new sample has been seen by several well-known security researchers who confirm Kroustek’s findings.
The return of Sodinokibi is certainly not good news for those already hard-pressed to defend corporate networks.
Not only has the war in Ukraine caused spikes in energy costs and inflation in several economies but we have seen a host of new data-wiping malware. Now, ransomware strains believed to be gone are coming back from the dead.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion