Thanos and Jigsaw Linked to 55 Yead Old Cardiologist
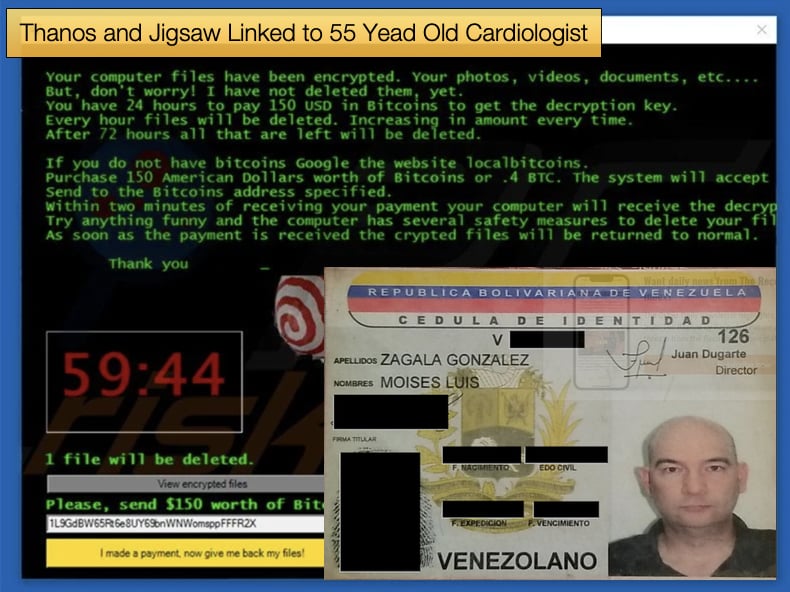
The US Department of Justice announced via the US Attorney’s Office of the Eastern District of New York that Moises Luis Zagala Gonzalez (Zagala), a 55-year-old cardiologist with French and Venezuelan citizenship residing in Ciudad Bolivar, Venezuela, created and rented Jigsaw and Thanos ransomware to cybercriminals.
Zagala who also went by the following online pseudonyms Nosophoros, Aesculapius, and Nebuchadnezzar, would not only rent the ransomware to other cybercriminals but would also provide varying degrees of support to help customers deploy the ransomware successfully.
US Attorney Breon Peace explained that,
“As alleged, the multi-tasking doctor treated patients, created and named his cyber tool after death, profited from a global ransomware ecosystem in which he sold the tools for conducting ransomware attacks, trained the attackers about how to extort victims, and then boasted about successful attacks, including by malicious actors associated with the government of Iran…Combating ransomware is a top priority of the Department of Justice and of this Office. If you profit from ransomware, we will find you and disrupt your malicious operations.”
It was further noted by Assistant Director-in-Charge Driscoll that,
“We allege Zagala not only created and sold ransomware products to hackers, but also trained them in their use. Our actions today will prevent Zagala from further victimizing users. However, many other malicious criminals are searching for businesses and organizations that haven't taken steps to protect their systems - which is an incredibly vital step in stopping the next ransomware attack,”
For the cardiologist’s more illicit activities if found guilty it is possible that the doctor could face up to five years’ imprisonment for attempted computer intrusion, and five years’ imprisonment for conspiracy to commit computer intrusions. In court documents unsealed by the court and in the announcement made by the Department of Justice the details of Zagala’s exploits dating back to 2019 are covered in great detail.
In 2019, the accused began advertising a new tool online described as a “Private Ransomware Builder” which was named Thanos, likely after the Marvel Comics villain, who in turn seems to be heavily influenced by conceptions of the Greek god of death Thanatos.
For further reading regarding Zagala’s now misadventure with the cybercriminal underground, it is advised that the announcement by the Department of Justice be read.
That said, things seem to have come to a head in May 2022, when law enforcement agents conducted a voluntary interview of a relative of Zagala who resides in Florida. The individual had a PayPal account that was used by Zagala to receive illicit proceeds. It was further noted that,
“The individual confirmed that Zagala resides in Venezuela and had taught himself computer programming. The individual also showed agents contact information for Zagala in his phone that matched the registered email for malicious infrastructure associated with the Thanos malware."
Thanos
While Thanos was being advertised in 2019 activity seemed to kick off in 2020. In that year researchers for Palo Alto’s Unit42 discovered files associated with an attack on two state-run organizations in the Middle East and North Africa. These would later be attributed to Thanos and the discovery allowed security researchers a better insight into the ransomware.
One of Thanos’ key attributes is that it is configured to overwrite a machine's master boot record (MBR). A machine's MBR allows for the computer to locate and load the operating system.
Overwriting the MBR would essentially leave the machine useless. This tactic is commonly used by another malware family called data wipers, or just referred to as wipers, which in some cases will look to masquerade as ransomware.
Modern ransomware will look to just encrypt data once the decryption key is handed over after the ransom is paid data is easily recoverable. If the MBR is overwritten data recovery for the victim becomes a vastly more difficult hurdle to overcome. Interestingly, some samples observed by researchers showed that the MBR overwrite feature was bugged and would not work.
Another feature of Thanos is its reliance on Powershell to not only initiate the ransomware but it will use the shell to spread laterally across a network to infect other devices.
The spreader was named LogicalDuckBill by researchers and regarding the spreader functionality, the module responsible for lateral movement starts with the script using the Get-NetTCPConnection cmdlet to get the remote addresses of the current TCP connections on the system.
The spreader will then search for other devices on the network suitable for infection. Lastly, the script will then use wmic to run “process call create” on the remote system to run the newly copied LogicalDuckBill sample on the remote system and delete copied iterations of LogicalDuckBill.
In samples observed by researchers, Thanos would drop a ransom note demanding the victim pay 20,000 USD in Bitcoin to have access to their data once again. It should also be noted that encrypted files have the .locked extension added to their filenames.
Jigsaw
The other ransomware strain that has been attributed to Zagala is Jigsaw and the ransomware uses a vast number of extensions appended to filenames upon encryption. This can make identifying the ransomware somewhat of a pain. Currently this publication has identified the following list of extension used by Jigsaw:
"NDGHacks", ".epic", ".HYDRA", ".paycoin", ".pennywise", ".data", .locked_by_mR_Anonymous(TZ_HACKERS), .spaß, .F*ckedByGhost, .#__EnCrYpTED_BY_dzikusssT3AM_ransomware!__#, .lockedgood, .pleaseCallQQ, .hacked.by.Snaiparul, .dat, .tedcrypt, .invaded, .black007, .F*ckED, .##___POLICJA!!!___TEN_PLIK_ZOSTA, .coder007@protonmail.com, .choda, .booknish, .hac, .LolSec, .email-[powerhacker03@hotmail.com].koreaGame, .jes, .Bitconnect, .contact-me-here-for-the-key-admin@adsoleware.com, .paymrss, .justice, .LOCKED_BY_pablukl0cker, .CryptWalker, .F*CKMEDADDY, .##ENCRYPTED_BY_pablukl0cker##, .####CONTACT_US_pablukl0cker638yzhgr@2tor.com####, .game, .#, .pablukCRYPT, .pabluk300CrYpT!, .pabluklocker, .afc, .korea, .kill, .rat, .Crypto, .paymts, .sux, .ghost, .R3K7M9, .tax, .lost, .beep, .ice, .die, .PAY, .Contact_TarineOZA@Gmail.com, .getrekt, .lckd, .crypte, .I'WANT MONEY, .nemo-hacks.at.sigaint.org, .jey, .gefickt, .uk-dealer@sigaint.org, .paytounlock, .hush, .locked, .payrmts, .afd, .paybtcs, .fun, .kkk, .gws, or .btc.
Jigsaw also includes a Doomsday clock of sorts, in that a counter is shown to the victim that when zero is hit the malware will delete a certain amount of files from the computer.
This is done on the hour, every hour until the ransom is paid. According to Donald Ashdown’s analysis of the ransomware, the ransomware will threaten to delete 1000 files if the machine is restarted or any process modification is detected.
Fortunately, Emisoft has released a free decryptor for victims of the ransomware which hopefully will mitigate the damage caused to victims.
The ransomware also makes use of several third-party tools for network monitoring and decompiling as examples. This is not uncommon to create completely custom tools to carry out tasks third-party tools are not worth the time of the malware developer. The tools used by Jigsaw include:
- Ghidra - Decompile .Net
- Glasswire - Live network connection monitoring
- Watch4 folder - Live file monitoring
- WireShark - Network traffic monitoring
- Hybrid Analyses - Sandboxing
- Dotpeek - Decompile .NET
While the arrest of Zagala is certainly a win for law enforcement, it is hoped that the information garnered from the investigation and hopefully, the subsequent court case will make it more difficult for other malware developers to develop and sell ransomware.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion