News Archive July 2013
Monthly Cyber Security News Archive: July 2013 Summary
Table of contents:
- Fake Profile Viewer
- Spoofed Adobe Flash Installs Audio Ads
- Styx Exploit Pack
- Facebook, Fake Flash Installation, and BitCoin Mining
- Bitcoin Mining Malware on the Rise
- Fake Antivirus Programs Getting More Devious
Fake Profile Viewer
07.07.13
As social media has risen in popularity, there have been numerous programs claiming to allow users to see who may be viewing their public profile on sites like Facebook and Twitter. Unfortunately, these programs are always fake as social media sites do not include an API to track profile views as these programs claim. Typically, users attempting to download the software are inundated with surveys or free software offers in an attempt to generate marketing revenue for the creators.
In a new version of this popular scam, a Tumblr blog is being used to disseminate a “Profile Viewer” executable file.
The malware seems to be targeting both the FireFox and Chrome web browsers at this time. The exe file is being offered from the URL hxxp://candycrushsagafreelifes.tumblr.com. Candy Crush Saga is a very popular game for both Facebook and Android/iOS smartphones and tablets.
The blog pops up with a notification informing users that multiple people are viewing their profile and that downloading the Profile Viewer will allow them to see who is viewing it.
Unlike many of the similar scams that have been reported in the past, this notification is filled with instructions for downloading and activating the executable file. Previous versions typically have surveys in the notification that must be completed before installing the program.
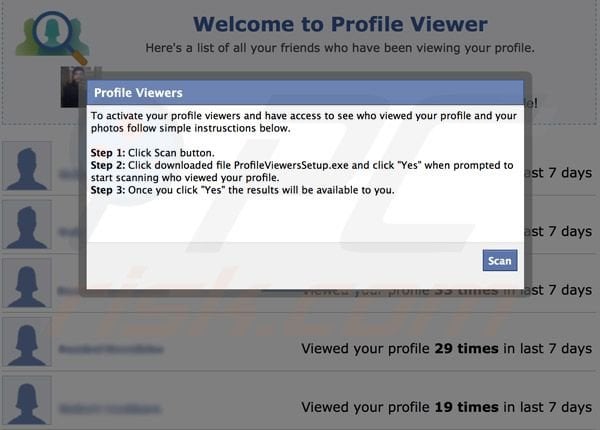
The instructions read as follows:
Step 1: Click Scan Button
Step 2: Click download file ProfileViewerSetup.exe and click yes when prompted to start scanning who viewed your profile.
Step 3: Once you click yes the results will be available to you.
Once a user clicks the scan button the download process begins. The malware performs two different actions depending on if the user is using FireFox or Chrome. In regards to FireFox, it will flash a screen informing the use that something is being installed. Unfortunately, this notification cannot be interacted with and occurs so fast before disappearing that most users will not even notice it at all. What the profile viewer is actually installing is a .xpi extension for FireFox referred to as WhoViewS 5.2 with the developer listed as Crock Safari. The extension uses the Adobe Flash icon as its extension image. At this time, the extension doesn’t appear to be doing very much but could be a placeholder for something more malicious planned for the future. The Profile Viewer affects the Chrome browser in a completely different manner. Instead of installing an extension, Chrome users will be redirected to another fake Profile Viewer website located at hxxp://ulolnow.info. This site pops up multiple notifications filled with surveys as the creators try to make some affiliate income from this malware.
The Chrome install seems to be more troublesome at this point but the FireFox vulnerability could lead to a dangerous extension update in the future.
Although many users would like the ability to view who may be looking at their social media profile, there is simply no way to do this unless you happen to be employed by Facebook or another social media site. Regardless of what claims a software company makes, Profile Viewer applications are always a scam and can even pack a malware punch as demonstrated by this latest threat.
Spoofed Adobe Flash Installs Audio Ads
10.07.13
Audio advertisements are popping up as unwanted software on many user’s computers. These ads completely take over the processor and render the computer practically useless for anything other than listening to the audio. To make matters worse, the audio often sounds like a garbled mess and is extremely annoying. The purpose of this new wave of audio hijacks to generate ad revenue by resolving hundreds of IP addresses that create ticks on the visit counter and create an income stream for the hackers behind the malware. This is why the computer becomes unusable; the processor is forced to establish and close hundreds of connections at a time.
The latest threat comes disguised as a completely legitimate version of the Adobe Flash installer program. The installer window that pops up is indistinguishable from the real Adobe Flash update window so it typically does not raise any red flags for the user. The difference is that no matter which of the three options (Allow Update, Notify Me, and Never Check) the user chooses, once they hit “Next” the script installs on the machine.
Once the status bar is filled and the “Finish” option is presented, the computer is force restarted without allowing users time to save any work in progress.
After the computer reboots, everything appears normal for a couple minutes while the newly installed malware is loading. Suddenly, the machine slows to a crawl and the audio advertisements begin.
Upon careful examination of background processes involved, it appears that the malware uses a hijacked version of the “svchost.exe” process. This fake process uses up almost the entire processor’s capacity by establishing multiple connections to ad servers. Although properly updated antivirus software is typically capable of detecting this attack once it has occurred, it is not very hard to remove once you understand what has happened. When looking at the Windows startup entries there are going to be two entries named “Software Modem” and “Utility Suite.” These two programs point to rogue DLL files located in appdata. By removing the files in the appdata folder and then the associated startup keys, this particular malware is easily removed from the system. Not quite as common, but definitely more dangerous, there are some versions of the spoofed Adobe Flash installer that use rootkits to infect the Master Boot Record of the machine. Unfortunately, these versions are much more difficult to remove because they are loaded before any Windows security features have been activated.
Detection using antivirus software is also not guaranteed once the MBR has been infected.
Updated antivirus software may help lessen the likelihood of downloading the rogue installer in the first place. Ensure that any updates you install are from trusted sources and look for anything suspicious during the installation process that might tip you off to a potential malware installation.
Styx Exploit Pack
14.07.13
As the sale of malware kits continues to become more mainstream, it is becoming easier for cybercriminals to purchase a variety of exploit kits with relative ease. Purchasing these kits used to require “connections” within the hacking underworld or at the very least, access to various private hacking forums where the malware was offered for sale. The Styx exploit kit, among others, is available on the open market via websites operated by hackers around the world.
Named after the river that separates mortals from the underworld in Greek mythology, Styx is a malware kit targeting the hacking underground but available for sale to the public at styx-crypt.com. Not only can customers who purchase the $3,000 malware package use the kit in anyway they choose but the website is also offering a 24 hour virtual help desk for customers should they run into problems during deployment. As an exploit kit, Styx relies on a multitude of exploits to be effective.
When an unsuspecting user visits an infected site, each exploit is attempted.
If the user’s computer does not include all the latest security updates, the machine is silently infected with any number of malware packages. After researching a recent Styx control panel, it appears that most of the exploits revolve around vulnerabilities in Java. Specifically, CVE-2013-0422, CVE-2013-2423, and CVE-2013-1493 seem to be the targeted vulnerabilities. All of these Java exploits were patched earlier this year but reports show that 1 out of every 10 computers targeted is successfully infected.
 It is also worth noting that almost all of the infected machines were using Internet Explorer as a web browser. Computers using Google Chrome are seemingly immune to these attacks and Mozilla Firefox users are much less likely to be infected as well. In fact, Chrome is so effective at stopping these drive-by download attacks that many malware creators attempt to trick Chrome users into downloading fake browser updates instead. The Styx installation reviewed was setup on June 24th and has already successfully infected over 13,000 machines worldwide. This latest installation relied on only three Java bugs as well as CVE-2011-3402 (a Windows font flaw) and installs malware ranging from the Reveton ransomware package to the infamous Zeus banking trojan. Kits like this can be designed to target attackers anywhere in the world depending on which malicious websites are used. Although this particular Styx installation seems to be targeting European users, it could just as easily be redirected to United States computers by infecting a U.S.-based website instead.
It is also worth noting that almost all of the infected machines were using Internet Explorer as a web browser. Computers using Google Chrome are seemingly immune to these attacks and Mozilla Firefox users are much less likely to be infected as well. In fact, Chrome is so effective at stopping these drive-by download attacks that many malware creators attempt to trick Chrome users into downloading fake browser updates instead. The Styx installation reviewed was setup on June 24th and has already successfully infected over 13,000 machines worldwide. This latest installation relied on only three Java bugs as well as CVE-2011-3402 (a Windows font flaw) and installs malware ranging from the Reveton ransomware package to the infamous Zeus banking trojan. Kits like this can be designed to target attackers anywhere in the world depending on which malicious websites are used. Although this particular Styx installation seems to be targeting European users, it could just as easily be redirected to United States computers by infecting a U.S.-based website instead.
It is important to realize that just like most of the other dangerous exploit kits on the market, Styx relies on zero-day exploits that are months and sometimes even years old.
These threats are easily blocked by having updated browsers and Java environments. The number of machines infected by just a couple of Java exploits is yet another strike against Oracle as it continues to deal with widespread exploitation and a global community that is hesitant to incorporate Java into any future releases.
Facebook, Fake Flash Installation, and BitCoin Mining
18.07.13
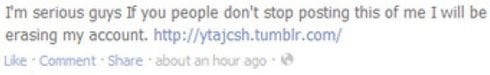
Using Tumblr as a launching pad, a new phishing scheme as emerged with multiple facets that can really get users into trouble. A Facebook message has been circulating on random profiles that entices users to click on a Tumblr link where they are redirected to a Facebook credential phishing page and then on to a rogue Flash player installation. The fake Facebook message reads: “I’m serious guys if you people don’t stop posting this of me I will be erasing my account.” Many users will be interested to learn more about this statement and will click on the link embedded within the post that directs them to ytajcsh.tumblr.com.
Existing as nothing more than a spam blog, the Tumblr site attempts to redirect users immediately to a fake Facebook login page that looks perfectly legitimate. For those of you familiar with Facebook, you may realize that it is not uncommon for Facebook to ask for your credentials every once in awhile so this may not tip off users to the threat.
After providing their login credentials to the phishing site, the user is also asked to provide the answer to a security question of their choosing. At this point, the Facebook account is totally compromised. This is most likely how the rogue post is being disseminated and can lead to further exploitation of the account in the future.
Once the user has answered the security question they are redirected to a fake Flash player page that is identical in wording to the Twitter spam run of 2012.
The page reads: “An update for Youtube player is needed. The Flash player update 10.1 includes *Smoother video with hardware acceleration support *Enhanced performance and memory management *Support for multi-touch and gesture-enabled content *Private browsing support and security enhancements.” Although the landing page is identical to the Twitter scam, the downloaded program has a different intent. When the executable is run, the user is notified that the computer needs to reboot. This is simply a distraction away from what the program is really doing. If Java is not installed, the program attempts to install it automatically. The computer is then logged into a remote server where more .JAR files are downloaded. At this point, it is impossible to examine many of the files because they are password protected and cannot be downloaded unless the infected machine follows a pattern of specific steps. It is apparent that many of the extra files downloaded relate to mining. Most likely, this is an attempt to convert the machine into a Bitcoin mining operation. In the competitive world of Bitcoin mining, it is impossible to mine Bitcoins without a massive server room or a botnet of mining machines. It appears that the later is being attempted through this malware installation. It doesn’t appear that the mining software is operating at this time.
The criminals behind this attack are probably waiting until a large enough botnet has been creating before starting the mining operation.
At the rate that this rogue program is being installed, however, it will not take long for the botnet to be in full operation.
Bitcoin Mining Malware on the Rise
21.07.13
Bitcoin is a decentralized, virtual currency that relies on peer to peer file sharing to solve complex algorithms and generate additional coins. The machines that perform these calculations are called Bitcoin miners and are typically comprised of large server rooms full of machines. Bitcoin Mining has become a very competitive business in and of itself and it appears that criminals are now trying to leverage the power of botnets to increase revenues by generating Bitcoins. The newest trend appears to be an affiliate program that pays people for mass installation of mining programs onto unsuspecting users computers.
These programs come in many forms and are picked up by a couple of antivirus programs as Trojans. Most antivirus software, however, does not notice the malicious software at this time. Thanks to a registry entry in the Windows start up menu the mining program begins as soon as the computer is turned on and runs continuously.
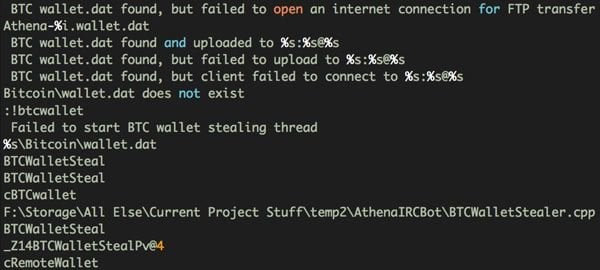
Mining software is notoriously CPU intensive and infected users can expect their machines to be practically unusable for anything other than basic tasks while the mining program is running.
A Russian language affiliate program known as FeodalCash is responsible for paying members to distribute the mining software to as many machines as possible.
The affiliate program has been in operation since May of this year and is actively recruiting new members who can positively demonstrate their control of enough bots to guarantee hundreds of installs per day.
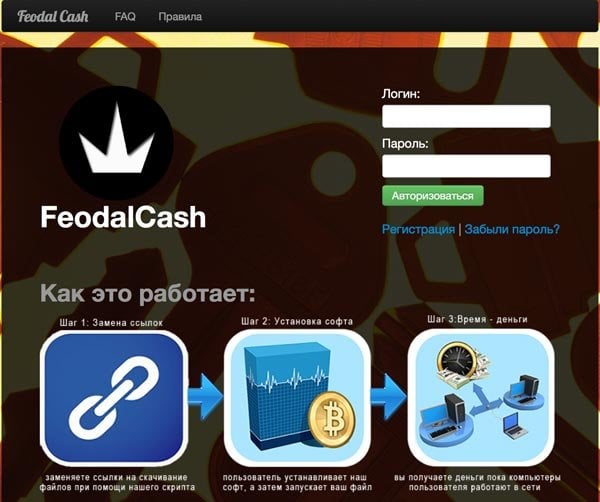
Although the administrator of the program denies that his mining program is considered malware he cautions all affiliates against submitting the program to multi antivirus scanners such as Virustotal. Scanners such as this will report malicious software to participating antivirus vendors so it is obvious that the administrator of FeodalCash is worried about the legitimacy of the software. Even with claims that the software is not malicious the affiliate website includes a graphical tool that helps new affiliates create custom installer programs capable of installing on Windows machines using a variety of disguises; namely icons that are very similar to legitimate Windows icons.
An undisclosed source was able to gain administrator level access to the backend database for the affiliate program and discovered hundreds of messages between affiliates and the administrator most of which pertained to web traffic numbers.
At this time, FeodalCash has a confirmed 238 working affiliates and it is unclear exactly how many machines have been infected. The software forces machines to become part of the Eligius Bitcoin Mining pool. Mining pools are open source collectives where people can sign up and install mining software for a small piece of the Bitcoin revenue generated. According to the FeodalCash administrative panel, the infected machines have only created approximately 140 Bitcoins so far.
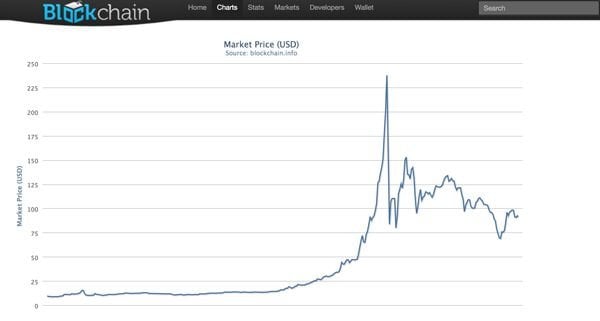
Although the exchange rate tends to fluctuate greatly in the Bitcoin world, currently each coin is worth approximately $100. With a total pull of $14,000 so far, it is certainly not the most devastating of schemes. The Bitcoin system typically only generates approximately 4.7 Bitcoins per day worldwide. Expect this affiliate program to continue spreading as the administrator attempts to take a larger piece of the action.
Fake Antivirus Programs Getting More Devious
25.07.13
Rogue, or fake, antivirus software is nothing new. Recently a new version has come out that does have an interesting trick up its sleeve capable of fooling even experienced users. The dialog window that pops up simply refers to the program as Antivirus System. Many of these programs in the past have had fancy sounding names but this one seems to aim for a more “no-frills” approach. Like all the fake antivirus programs before it the main premise of this program is to block any executable that you try to launch and flag it as malicious.
Eventually an interface pops up and begins a “scan” of the machine. Most of these programs do not actually scan anything and just provide users with graphics that appear like a scan is occurring.
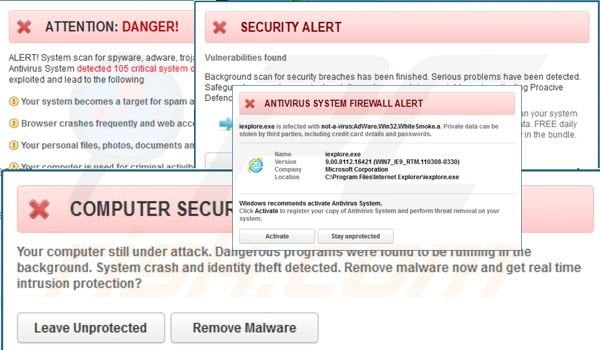
This version actually scans the machine and pops up with legitimate files within your system and claims they are malicious.
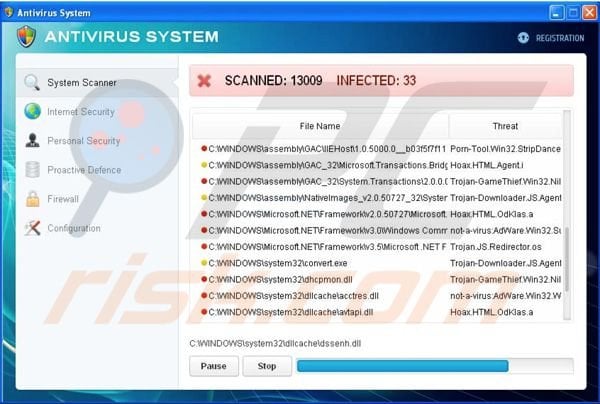
Of course when you try to remove these programs you are prompted with the payment screen for the fake antivirus software. It is unclear at this time if your payment information is used for other malicious purposes besides stealing your money for this fake service.
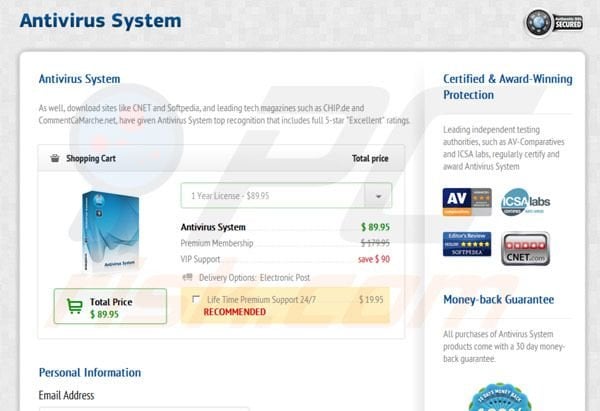
The software adds to its professional appearance by offering many features commonly found on legitimate antivirus programs such as Internet Security and Personal Security.
Both of these services are commonly offered by just about every major antivirus carrier. The difference is that these don’t do anything other than bring you to the payment screen. The biggest change that this program presents is that it blocks safe mode.
Usually, the best method for removing rogue antivirus is to reboot into safe mode with networking and run an anti-malware program from that interface.
Since this program attaches itself to the Explorer shell (which is loaded in safe mode) it will flag executables such as the registry editor and task manager as malicious in addition to any third-party virus removal tools you may have installed. One of the methods for removing this rogue program is to boot into safe mode with command prompt and then access the user account screen using the command “control nusrmgr.cpl” and create a new account from that dialogue.
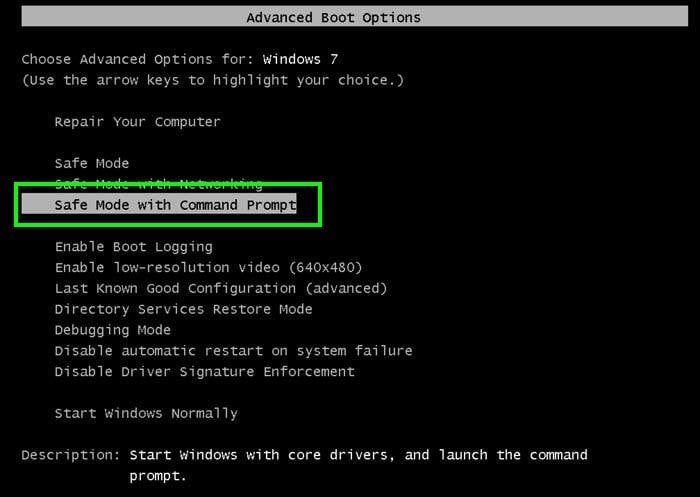
This new account will not have been infected by the malware and can be used to search for and destroy its related files.
Make sure the newly created account has Administrative privileges.
Certainly many users are not comfortable using the command prompt for much of anything and this solution may not appeal to most. Other option to remove Antivirus System is using a removal guide which can be found here: Antivirus System – how to remove? This new technique is interesting and it demonstrates perfectly how an old and outdated malware package can be revamped to create havoc with just a couple of minor tweaks.
As usual, the best way to avoid infection is to avoid downloading any files if you are unsure of the source and to make sure your antivirus applications are always updated to the latest version.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion