Ransomware
Ransomware is malware that encrypt data files that can only be decrypted when the data file owner pays a ransom. The only recovery method is to go to a backup. Guessing the password to unlock the file is for all practical purposes impossible because of the nature of cryptography. Regarding defenses the only good defense is to make lots of backups and to train users not to click on phishing emails. Antivirus software might help, but certainly will not work in all cases.
The way that ransomware works (for example TeslaCrypt, CryptoWall, Locky, Crypt0L0cker and Cerber) is it scans the user’s drive and encrypts each files using an encryption key that only the hacker knows. It also sets up some kind of communication channel so that is can alert the hacker that it has found a victim. It also adds software code to the encrypted file that causes a screen to pop up when a user opens it. This screen both tells the user that their data is locked and provides a screen where the user can enter the code to unlock it and where to go to pay the ransom.
One type of ransomware attacks the boot sector of the hard drive of a PC thus taking control from Windows or other software when the machine boots.Then when the machine boots up the hacker makes their ransom demand known right up from by taking over the screen with a full-screen message saying that. This type of attack goes after home users who are often older people or some without a lot of technical expertise (That would be most people.) who would be started by this message and at a loss as what to do.
Screenshot of CryptoWall file encrypting ransomware:
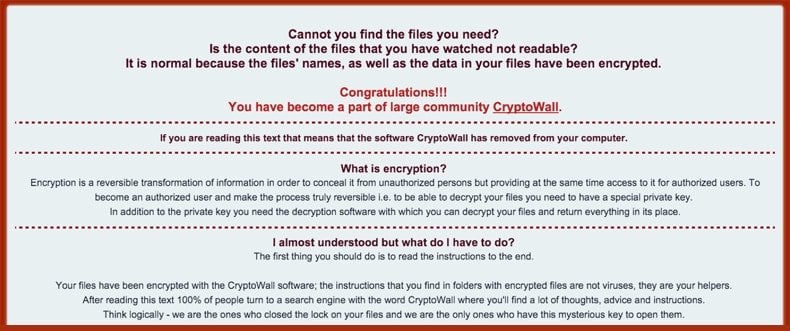
Only someone who understands disk partitions would be able to update the boot sector on their computer without erasing the whole computer to allow the computer to boot. They could then install another OS to be able to at least see the data files. Or they could run Linux from a USB drive to be able to data files as well. That removes the problem of not being able to start the PC. But it does not remove the problem of how to decrypt the data that the hacker has encrypted. That for all practical purposes is impossible to do. The only hope is that some files can be salvaged as ransomware usually only encrypts specific file suffixes.
The other type of hack can work on a PC data file, data files on a server, or data in the cloud. In the last two scenarios the attack is not localized to one victim but attacks a whole business or organization especially if that file is, say, the Oracle database raw data files.
Screenshot of Locky ransomware:
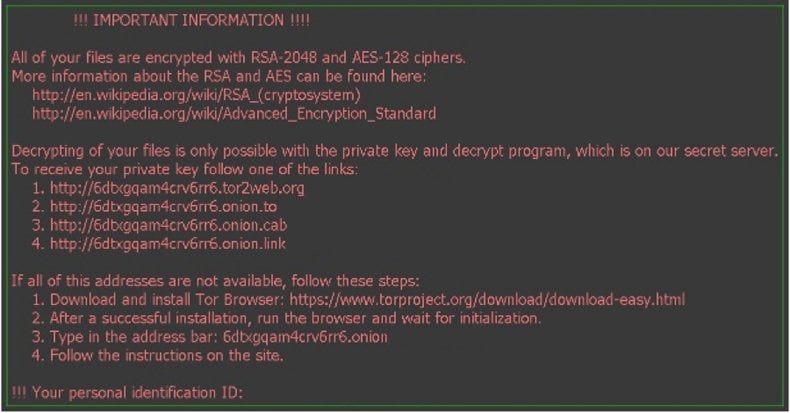
There have been reports in the media about police departments and even hospitals who, faced with this situation, went ahead and paid hackers to unlock police and medical files. That they had to pay shows how dire the situation was and the impossibility of recovering from that even when they had forensics security expert help.
Is it Possible to Recover from This?
There is only one way to recover data lost like this and that is to go to some kind of backup. In a transactional system, like the accounting system, the longer it takes to discover that data is lost the more data will be lost as those transactions have been entered over time. The recovery procedure would be to wipe all the computers to replace the operating system, and thus the virus, and the do a point-in-time recovery. Then the victim could try to add back the transactions that had to be abandoned. If there is some email trail or printed receipts that might be possible. At worst case, and one that would damage a business’s reputation, they might have to inform their customers and ask their help in getting their data back by using the customer’s paper trail.
Screenshot of KeRanger ransomware:
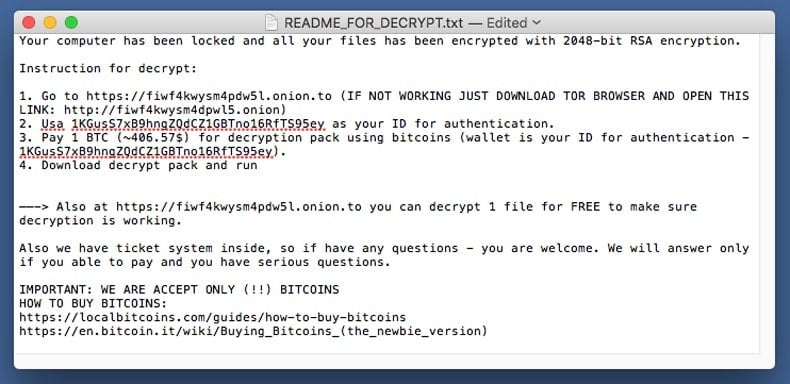
Ransomware is perhaps one of the worst kinds of computer viruses because it goes right after what is most valuable to uses: the data they use every day. As we said above, there is no good way to protect against that except be careful where you click. In this case the user cannot be faulted. The fault would lies with the people who maintain the Transmission opensource project and their failure to stop someone from uploading a modified version of their program there.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion