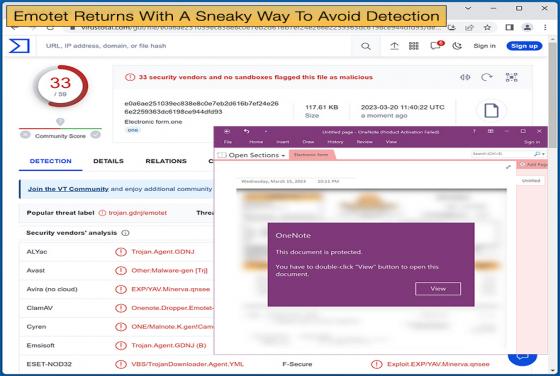
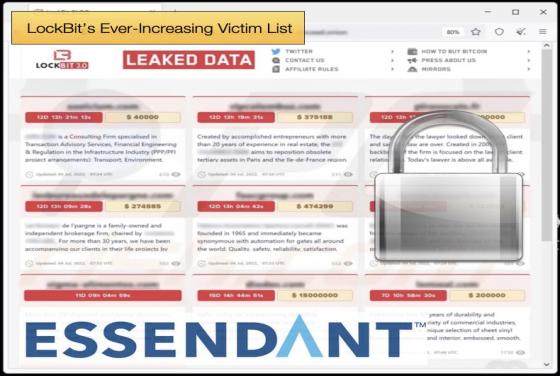
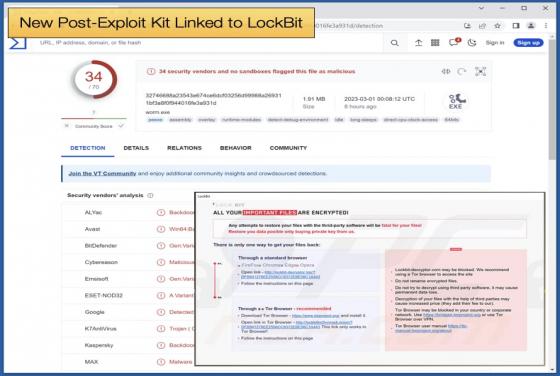
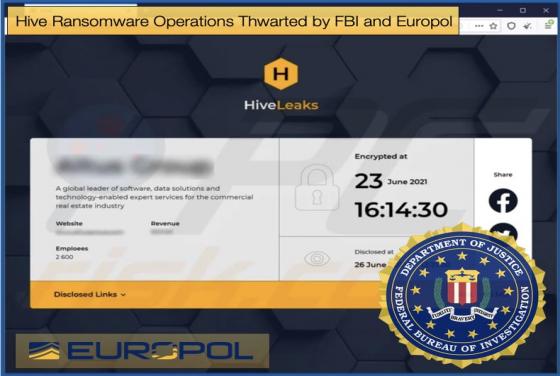
New BlackGuard Variant Capable Of Targeting 57 Wallets And Extensions
Security researchers for the major telecommunications company AT&T have discovered a new variant of BlackGuard, a new info stealer that is gaining popularity with threat actors using underground hacking forums. This new variant is actively being distributed in the wild and boosts several new fe