Hidden Bomb In The Building Email Scam
Phishing/ScamAlso Known As: Hidden Bomb In The Building spam
Get free scan and check if your device is infected.
Remove it nowTo use full-featured product, you have to purchase a license for Combo Cleaner. Seven days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com.
What is "Hidden Bomb In The Building"?
"Hidden Bomb In The Building" is an email scam. There are many scams of this type, most of which are sextortion-type: they are used to trick people into believing that humiliating or compromising material (videos or photos) have been obtained and shared with all users on the recipient's contacts list.
Note, however, that "Hidden Bomb In The Building" differs, since it is categorized as a terrorist threat.
Cyber criminals use the "Hidden Bomb In The Building" scam to make threats about an explosive that has supposedly been planted. They make ransom demands in the Bitcoin cryptocurrency. The email message states that a bomb has been planted in the recipient's company building. It goes on to state that the explosive is small but powerful enough to harm many people.
They also warn recipients that if a 'recruited person' notices any unusual activities (such as people calling the police), this person will detonate the explosive. Cyber criminals demand payment of "20.000 $" in Bitcoins (using a Bitcoin wallet address provided) by the end of the day, otherwise the explosives will be detonated.
They also state that this is not a personal threat and that only the recipient's company is being threatened. They will not check the email and will only check the Bitcoin wallet every thirty minutes. Once payment is received, they will inform the 'mercenary' present in the building to leave with the explosives, thus eliminating the threat.
There is also a note for authorities stating that they are not terrorists (do not belong to any terrorist group) and do not take responsibility for explosions in other buildings. Cyber criminals behind this email scam have used many different messages and have sent them to various facilities, however, all include identical demands: to pay "20.000 $" in Bitcoins to an identical Bitcoin wallet.
| Name | Hidden Bomb In The Building Email Scam |
| Threat Type | Phishing, Scam, Social Engineering, Fraud |
| Symptoms | Unauthorized online purchases, changed online account passwords, identity theft, illegal access of one's computer. |
| Distribution methods | Deceptive emails, rogue online pop-up ads, search engine poisoning techniques, misspelled domains. |
| Damage | Loss of sensitive private information, monetary loss, identity theft. |
| Malware Removal (Windows) |
To eliminate possible malware infections, scan your computer with legitimate antivirus software. Our security researchers recommend using Combo Cleaner. Download Combo CleanerTo use full-featured product, you have to purchase a license for Combo Cleaner. 7 days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com. |
As mentioned above, many email scams are of the sextortion type and are popular amongst cyber criminals. If you have not already received such an email, be aware that you might in future. They sometimes contain attached links that lead to various computer infections. In these cases, scammers invite recipients to watch a video or view an image before transferring payment.
The video/photo is a download link (for example, Google Docs) that leads to a file, usually an archive that contains executables. When opened, these files download and install high-risk computer infections. Read more about sextortion email scams that proliferate viruses here.
How do spam campaigns infect computers?
Spam email campaigns (those that proliferate infections through attachments) cannot infect computers without users first opening the attachment or executing a malicious executable file. If the attached file is a Microsoft Office document, the downloaded malicious attachment will demand permission to enable macro commands.
If enabled, these commands allow the infection to be downloaded/installed. Remember that infections proliferated through these malicious email attachments cannot do any harm unless they are opened.
How to avoid installation of malware?
Be careful with emails received from unknown or suspicious addresses, especially those that contain attachments or web links. If the email seems suspicious or irrelevant, ignore it. Do not use untrustworthy sources when downloading software - this includes various software downloaders, peer-to-peer networks, and so on.
These are often used to promote rogue applications that might cause computer infections. Download and install software with care: check "Custom", "Advanced", and other settings of the download/installation setup. Deselect offers to uninstall unwanted apps and only then finish the process.
Update your software using tools or implemented functions provided by official software developers, and not fake/unofficial updaters. Use newer versions of Microsoft Office (later than 2010), since these have "Protected View" mode that prevents malicious attachments from automatically downloading/installing malware or other computer infections.
If you have already opened malicious attachments, we recommend running a scan with Combo Cleaner Antivirus for Windows to automatically eliminate infiltrated malware.
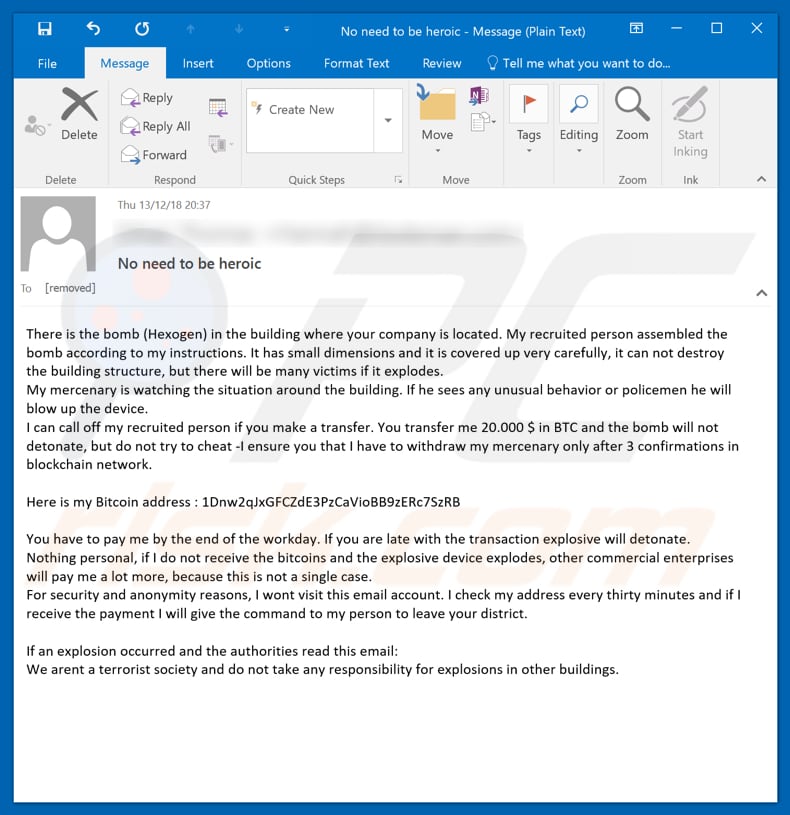
Text presented in the first "Hidden Bomb In The Building" email message:
Subject: No need to be heroic
There is the bomb (Hexogen) in the building where your company is located. My recruited person assembled the bomb according to my instructions. It has small dimensions and it is covered up very carefully, it can not destroy the building structure, but there will be many victims if it explodes.
My mercenary is watching the situation around the building. If he sees any unusual behavior or policemen he will blow up the device.
I can call off my recruited person if you make a transfer. You transfer me 20.000 $ in BTC and the bomb will not detonate, but do not try to cheat -I ensure you that I have to withdraw my mercenary only after 3 confirmations in blockchain network.Here is my Bitcoin address : 1Dnw2qJxGFCZdE3PzCaVioBB9zERc7SzRB
You have to pay me by the end of the workday. If you are late with the transaction explosive will detonate.
Nothing personal, if I do not receive the bitcoins and the explosive device explodes, other commercial enterprises will pay me a lot more, because this is not a single case.
For security and anonymity reasons, I wont visit this email account. I check my address every thirty minutes and if I receive the payment I will give the command to my person to leave your district.If an explosion occurred and the authorities read this email:
We arent a terrorist society and do not take any responsibility for explosions in other buildings.
Screenshot of a second "Hidden Bomb In The Building" email:
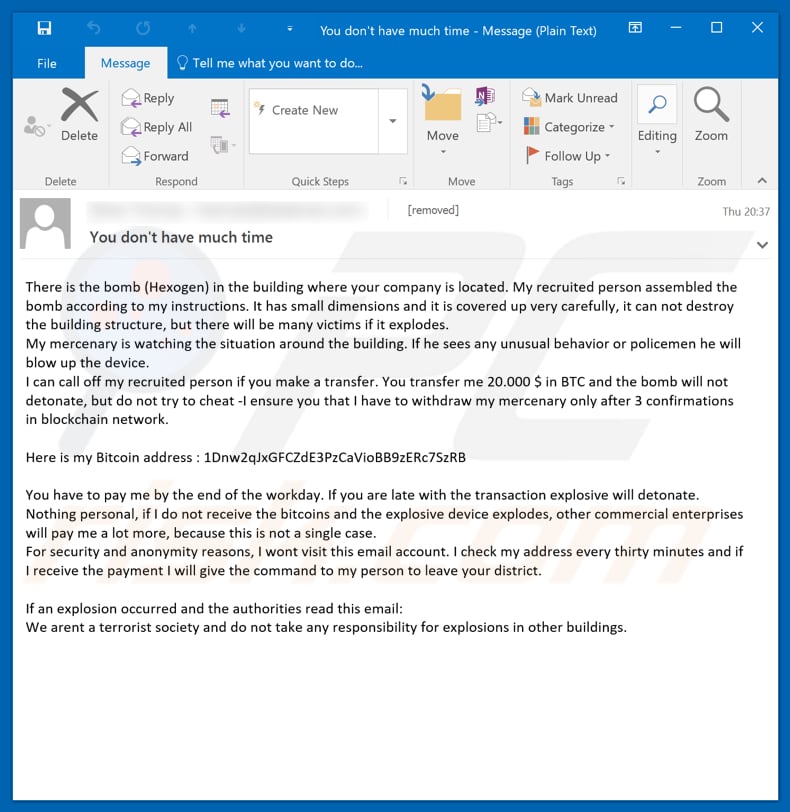
Text presented in the second "Hidden Bomb In The Building" email message:
Subject: You don't have much time
There is the bomb (Hexogen) in the building where your company is located. My recruited person assembled the bomb according to my instructions. It has small dimensions and it is covered up very carefully, it can not destroy the building structure, but there will be many victims if it explodes.
My mercenary is watching the situation around the building. If he sees any unusual behavior or policemen he will blow up the device.
I can call off my recruited person if you make a transfer. You transfer me 20.000 $ in BTC and the bomb will not detonate, but do not try to cheat -I ensure you that I have to withdraw my mercenary only after 3 confirmations in blockchain network.Here is my Bitcoin address : 1Dnw2qJxGFCZdE3PzCaVioBB9zERc7SzRB
You have to pay me by the end of the workday. If you are late with the transaction explosive will detonate.
Nothing personal, if I do not receive the bitcoins and the explosive device explodes, other commercial enterprises will pay me a lot more, because this is not a single case.
For security and anonymity reasons, I wont visit this email account. I check my address every thirty minutes and if I receive the payment I will give the command to my person to leave your district.If an explosion occurred and the authorities read this email:
We arent a terrorist society and do not take any responsibility for explosions in other buildings.
Instant automatic malware removal:
Manual threat removal might be a lengthy and complicated process that requires advanced IT skills. Combo Cleaner is a professional automatic malware removal tool that is recommended to get rid of malware. Download it by clicking the button below:
DOWNLOAD Combo CleanerBy downloading any software listed on this website you agree to our Privacy Policy and Terms of Use. To use full-featured product, you have to purchase a license for Combo Cleaner. 7 days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com.
Quick menu:
- What is Hidden Bomb In The Building spam?
- Types of malicious emails.
- How to spot a malicious email?
- What to do if you fell for an email scam?
Types of malicious emails:
![]() Phishing Emails
Phishing Emails
Most commonly, cybercriminals use deceptive emails to trick Internet users into giving away their sensitive private information, for example, login information for various online services, email accounts, or online banking information.
Such attacks are called phishing. In a phishing attack, cybercriminals usually send an email message with some popular service logo (for example, Microsoft, DHL, Amazon, Netflix), create urgency (wrong shipping address, expired password, etc.), and place a link which they hope their potential victims will click on.
After clicking the link presented in such email message, victims are redirected to a fake website that looks identical or extremely similar to the original one. Victims are then asked to enter their password, credit card details, or some other information that gets stolen by cybercriminals.
![]() Emails with Malicious Attachments
Emails with Malicious Attachments
Another popular attack vector is email spam with malicious attachments that infect users' computers with malware. Malicious attachments usually carry trojans that are capable of stealing passwords, banking information, and other sensitive information.
In such attacks, cybercriminals' main goal is to trick their potential victims into opening an infected email attachment. To achieve this goal, email messages usually talk about recently received invoices, faxes, or voice messages.
If a potential victim falls for the lure and opens the attachment, their computers get infected, and cybercriminals can collect a lot of sensitive information.
While it's a more complicated method to steal personal information (spam filters and antivirus programs usually detect such attempts), if successful, cybercriminals can get a much wider array of data and can collect information for a long period of time.
![]() Sextortion Emails
Sextortion Emails
This is a type of phishing. In this case, users receive an email claiming that a cybercriminal could access the webcam of the potential victim and has a video recording of one's masturbation.
To get rid of the video, victims are asked to pay a ransom (usually using Bitcoin or another cryptocurrency). Nevertheless, all of these claims are false - users who receive such emails should ignore and delete them.
How to spot a malicious email?
While cyber criminals try to make their lure emails look trustworthy, here are some things that you should look for when trying to spot a phishing email:
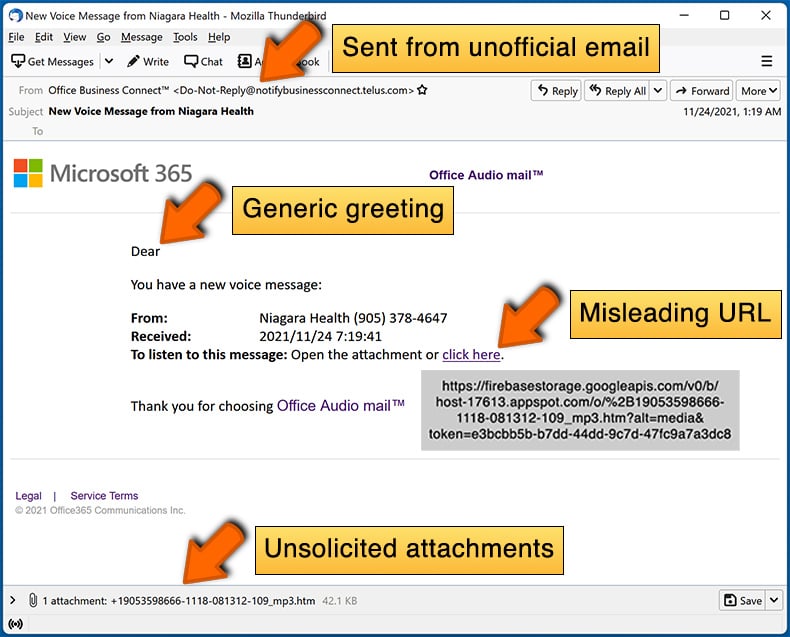
- Check the sender's ("from") email address: Hover your mouse over the "from" address and check if it's legitimate. For example, if you received an email from Microsoft, be sure to check if the email address is @microsoft.com and not something suspicious like @m1crosoft.com, @microsfot.com, @account-security-noreply.com, etc.
- Check for generic greetings: If the greeting in the email is "Dear user", "Dear @youremail.com", "Dear valued customer", this should raise suspiciousness. Most commonly, companies call you by your name. Lack of this information could signal a phishing attempt.
- Check the links in the email: Hover your mouse over the link presented in the email, if the link that appears seems suspicious, don't click it. For example, if you received an email from Microsoft and the link in the email shows that it will go to firebasestorage.googleapis.com/v0... you shouldn't trust it. It's best not to click any links in the emails but to visit the company website that sent you the email in the first place.
- Don't blindly trust email attachments: Most commonly, legitimate companies will ask you to log in to their website and to view any documents there; if you received an email with an attachment, it's a good idea to scan it with an antivirus application. Infected email attachments are a common attack vector used by cybercriminals.
To minimise the risk of opening phishing and malicious emails we recommend using Combo Cleaner Antivirus for Windows.
Example of a spam email:
What to do if you fell for an email scam?
- If you clicked on a link in a phishing email and entered your password - be sure to change your password as soon as possible. Usually, cybercriminals collect stolen credentials and then sell them to other groups that use them for malicious purposes. If you change your password in a timely manner, there's a chance that criminals won't have enough time to do any damage.
- If you entered your credit card information - contact your bank as soon as possible and explain the situation. There's a good chance that you will need to cancel your compromised credit card and get a new one.
- If you see any signs of identity theft - you should immediately contact the Federal Trade Commission. This institution will collect information about your situation and create a personal recovery plan.
- If you opened a malicious attachment - your computer is probably infected, you should scan it with a reputable antivirus application. For this purpose, we recommend using Combo Cleaner Antivirus for Windows.
- Help other Internet users - report phishing emails to Anti-Phishing Working Group, FBI’s Internet Crime Complaint Center, National Fraud Information Center and U.S. Department of Justice.
Share:

Tomas Meskauskas
Expert security researcher, professional malware analyst
I am passionate about computer security and technology. I have an experience of over 10 years working in various companies related to computer technical issue solving and Internet security. I have been working as an author and editor for pcrisk.com since 2010. Follow me on Twitter and LinkedIn to stay informed about the latest online security threats.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion