Notifinfoback.com Ads
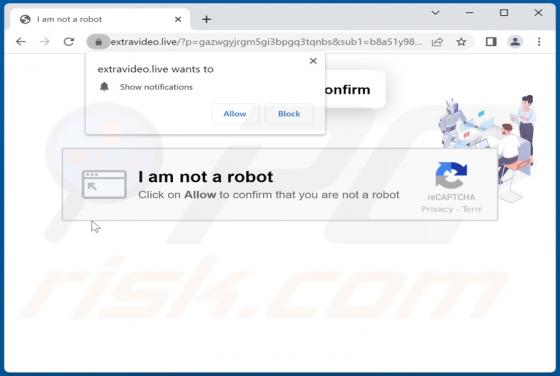
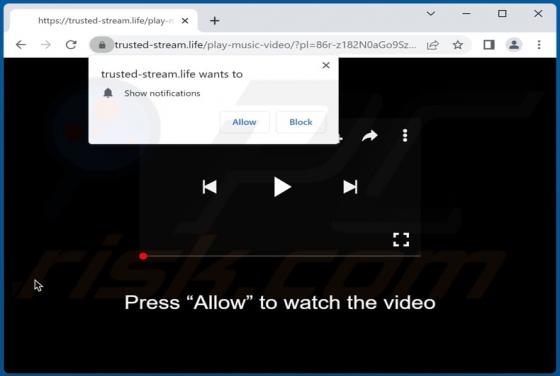
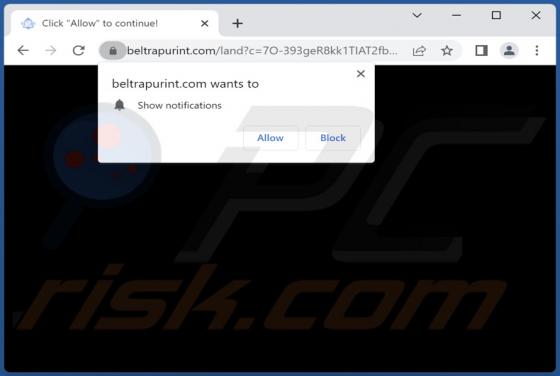
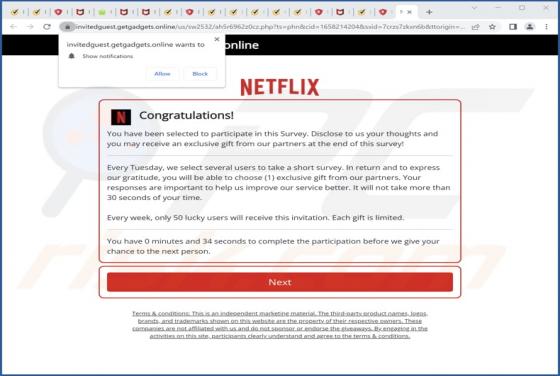
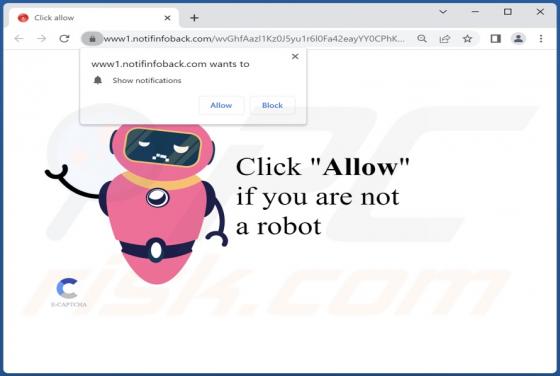
During a routine inspection of untrustworthy websites, our researchers found notifinfoback[.]com - yet another rogue webpage promoting browser notification spam. This site attempts to trick users into allowing it to deliver its notifications. Additionally, notifinfoback[.]com can cause redirects t