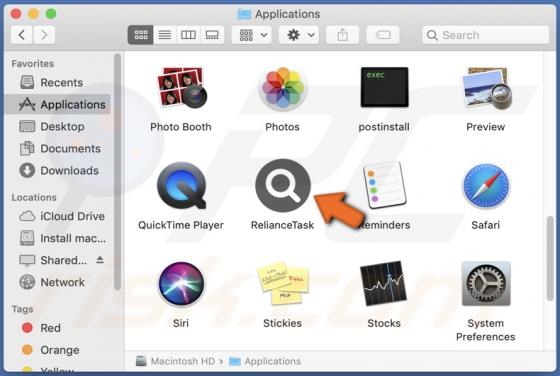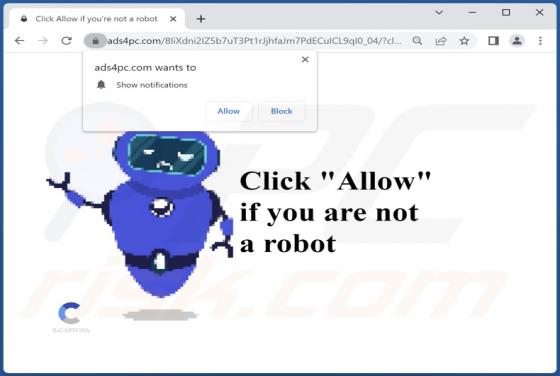
Ads4pc.com Ads
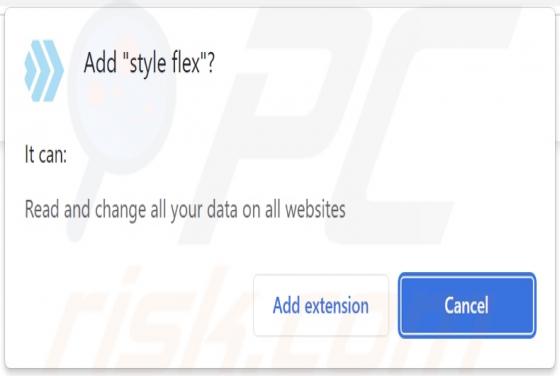
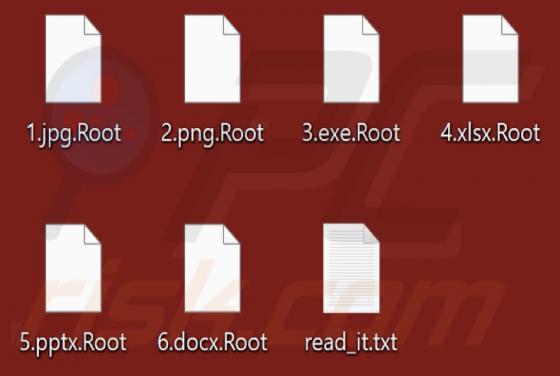
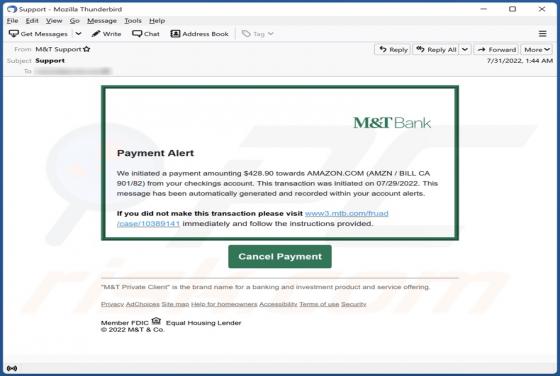
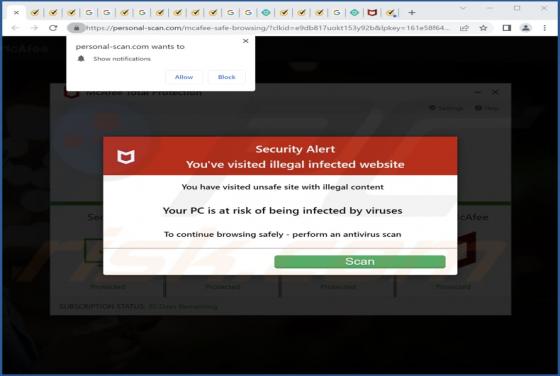
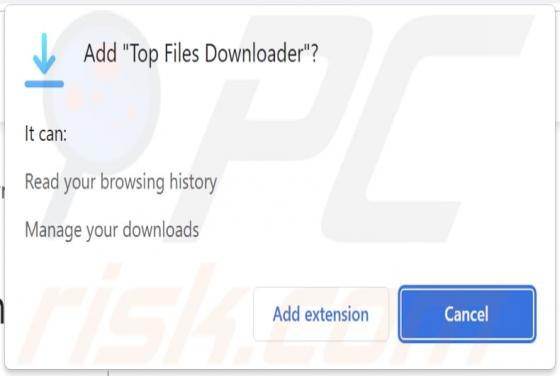
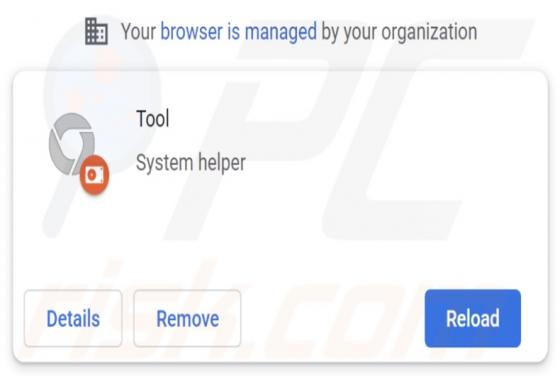
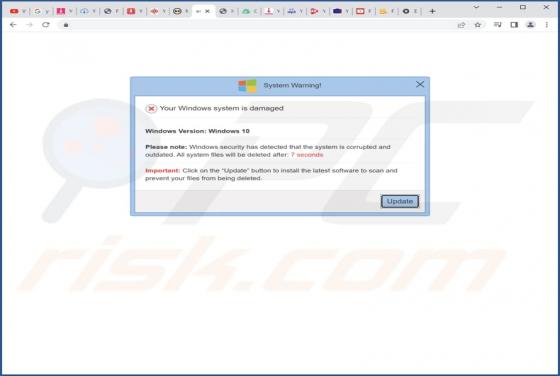
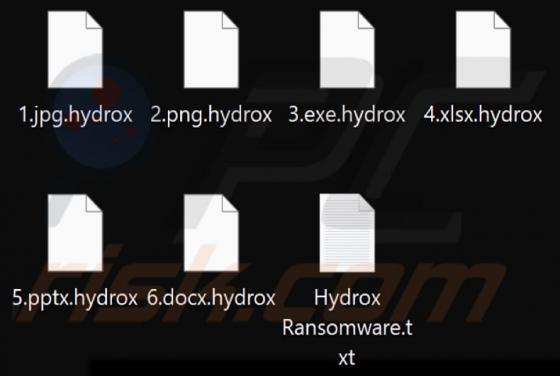
During a routine inspection of untrustworthy sites, our researchers found the ads4pc[.]com rogue webpage. It operates by pushing browser notification spam and redirecting visitors to other (likely unreliable/harmful) websites. Most users enter these pages through redirects caused by sites using ro