Helphack Ransomware
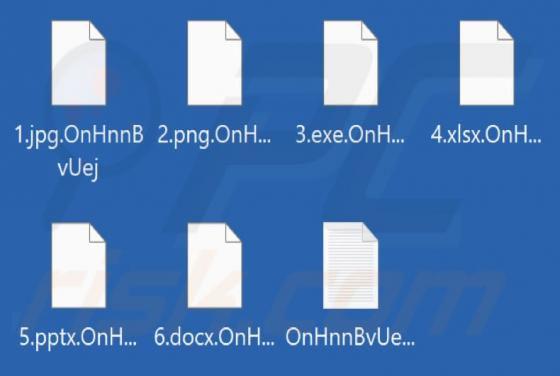
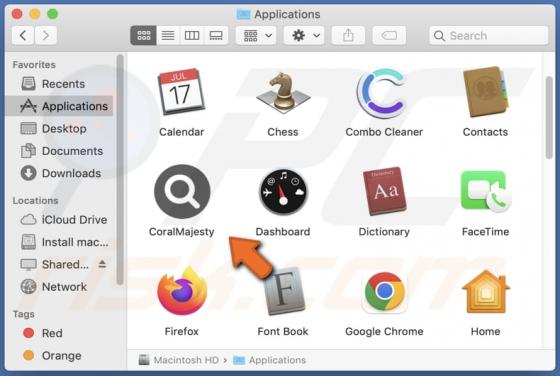
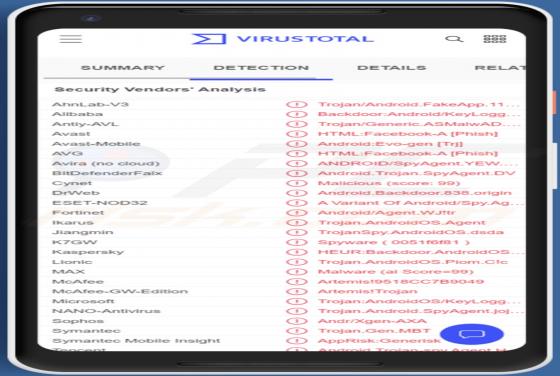
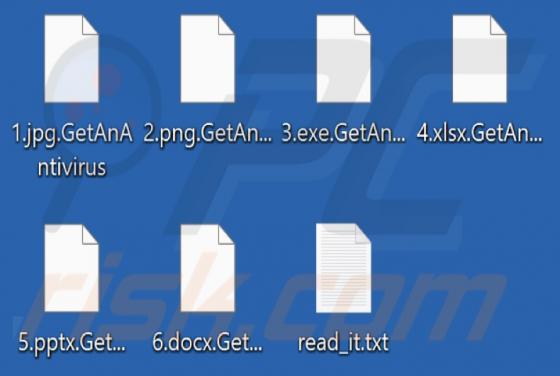
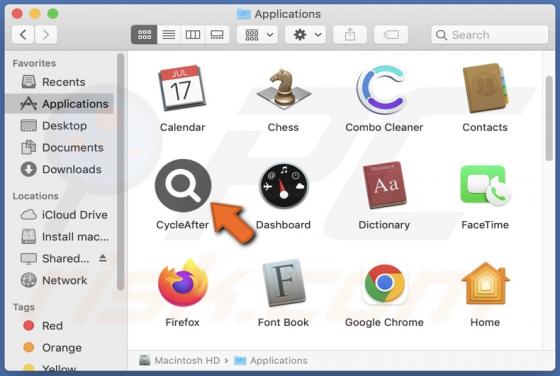
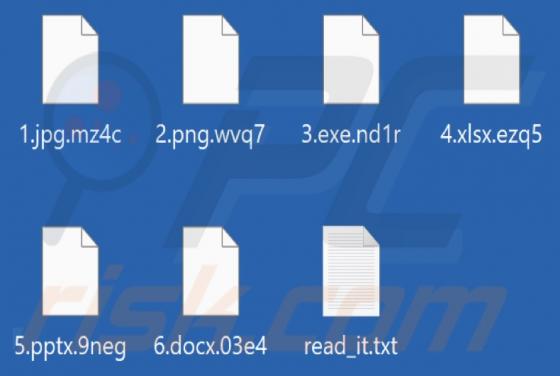
Our researchers discovered the Helphack ransomware during a routine inspection of new submissions to VirusTotal. We determined that Helphack is based on the Chaos ransomware. Once we executed a sample on our test machine, Helphack encrypted files and appended their names with an extension consist