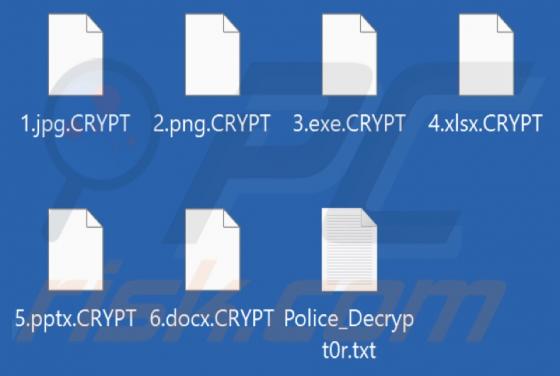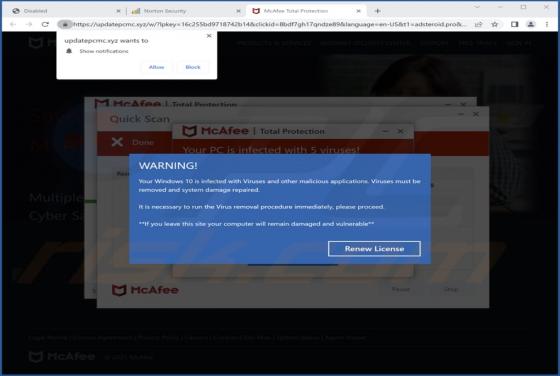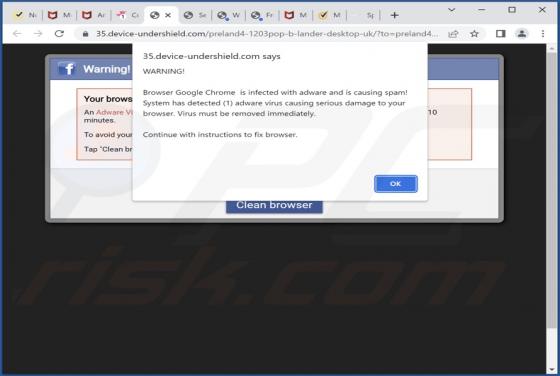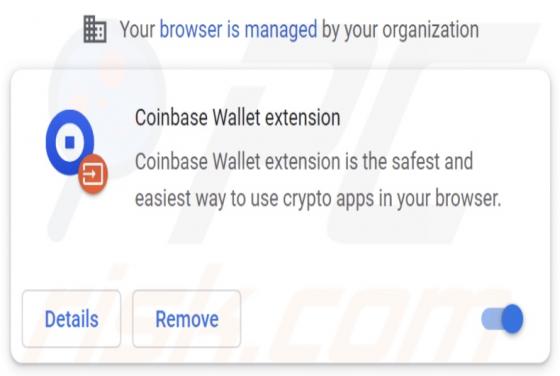
Fake Coinbase Wallet Extension
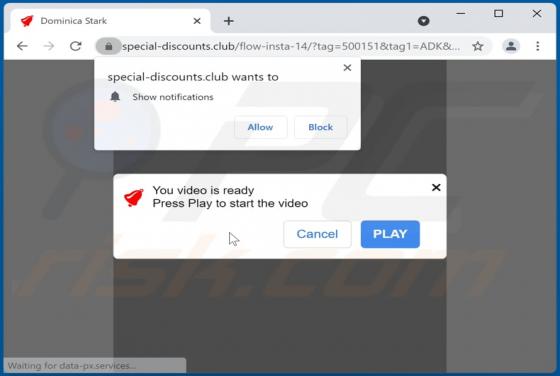
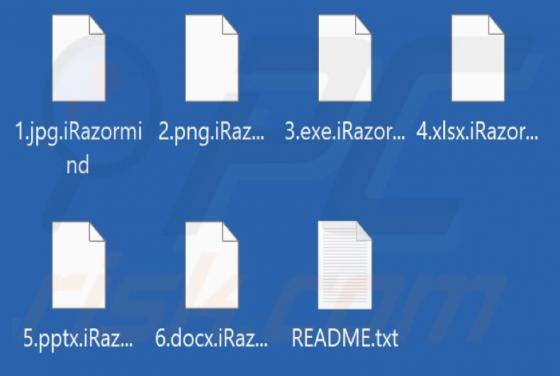
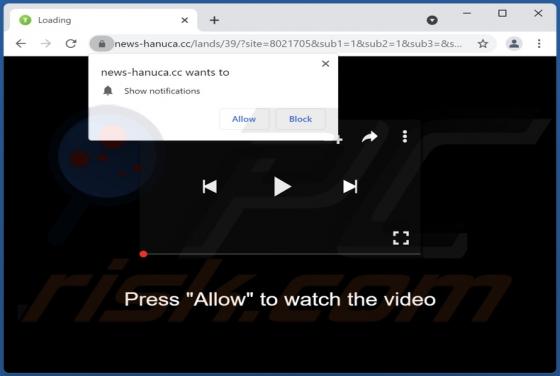
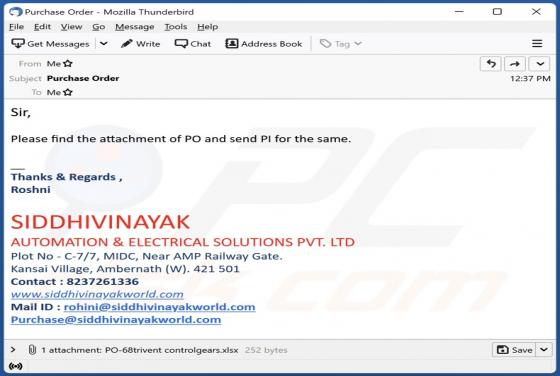
Fake Coinbase Wallet extension - refers to a rogue browser extension disguised as a Coinbase product. Unwanted software often uses the names, graphics, and other content belonging to legitimate products - in order to trick users into download/installation. Typically, software that uses deceptive