Mechatronics Industrial Equipment Email Virus
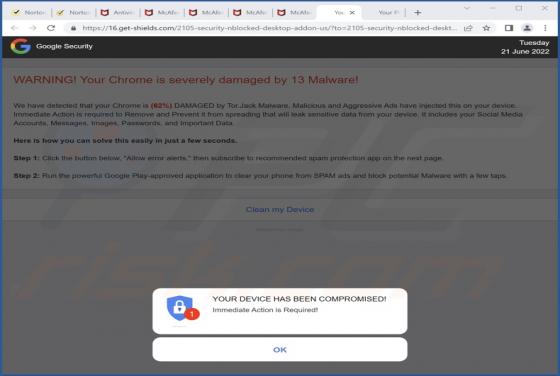
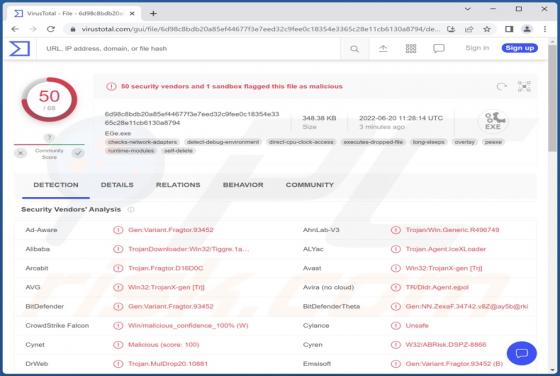
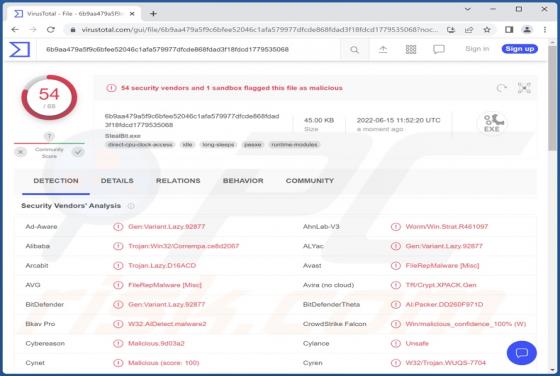
Our inspection of this "Mechatronics Industrial Equipment" email revealed that it is fake and intended to infect recipients' devices with the Agent Tesla RAT (Remote Access Trojan). This spam email supposedly relates to a payment. However, this letter is in no way associated with the legitimate M