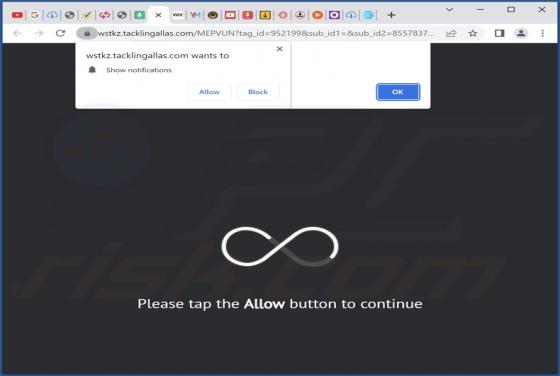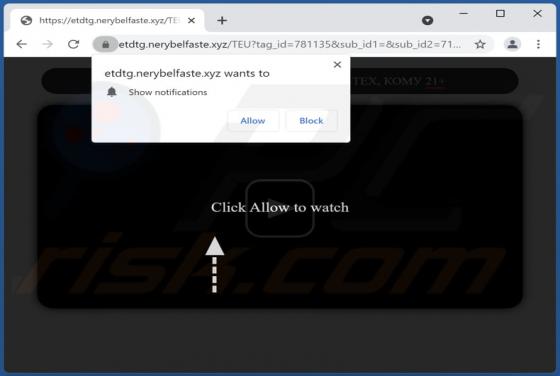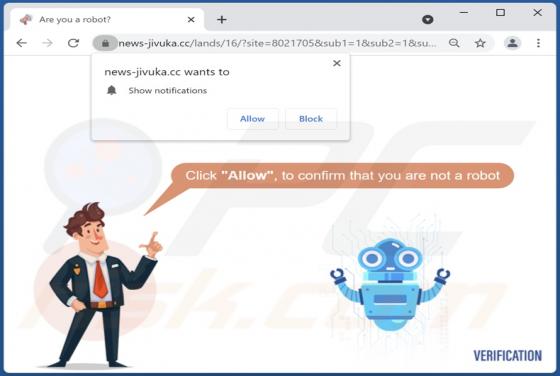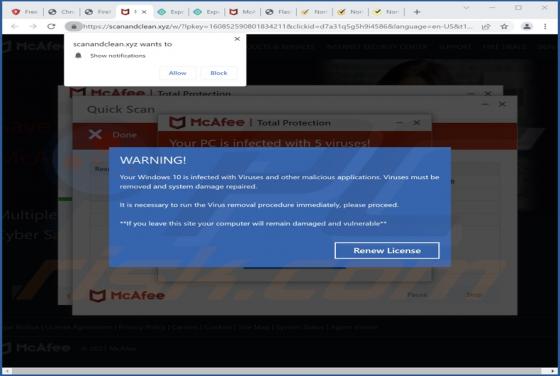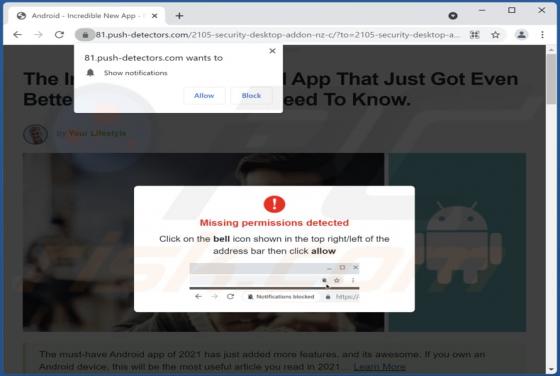
Push-detectors.com Ads
Push-detectors[.]com is an untrustworthy website that displays deceptive content to trick visitors into agreeing to receive notifications. Moreover, it redirects to other websites of this kind. Our team has discovered push-detectors[.]com while examining pages that use rogue advertising networks.