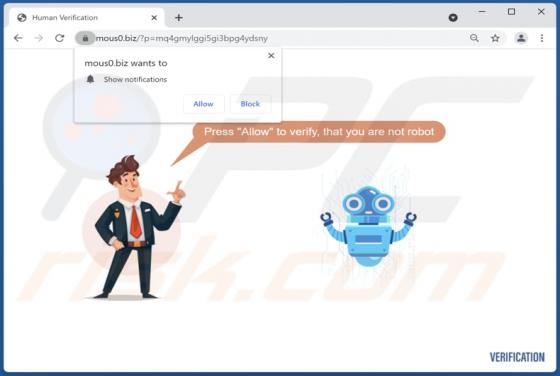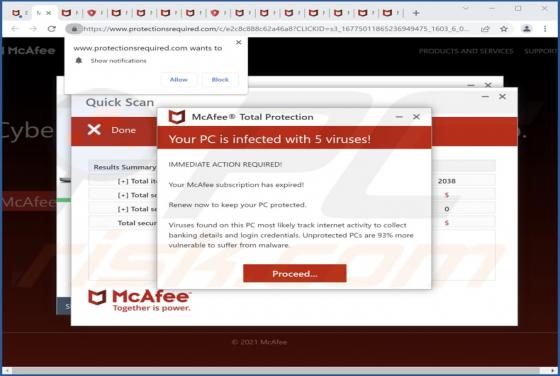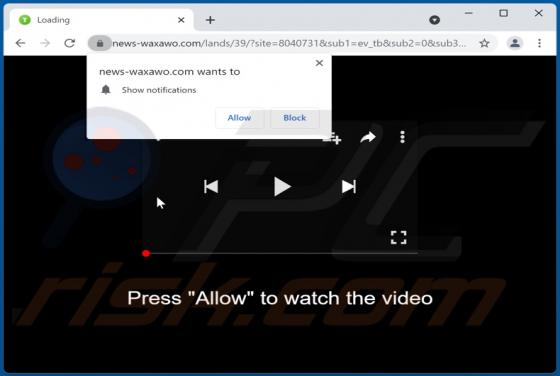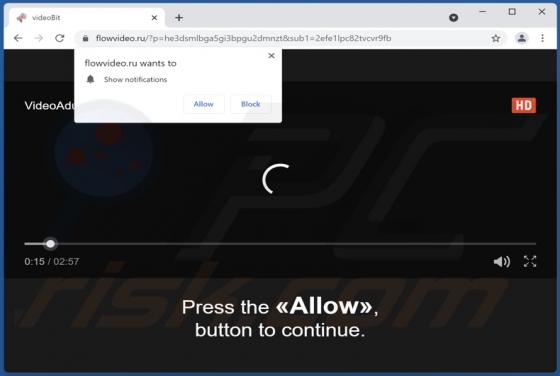
Flowvideo.ru Ads
Flowvideo[.]ru is a rogue page that we discovered while inspecting untrustworthy websites. This webpage is designed to promote spam browser notifications and lead visitors to other (likely dubious/malicious) sites. Most users enter rogue webpages via redirects caused by sites using rogue advertis