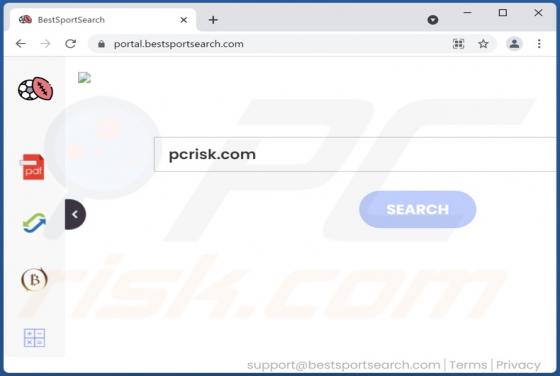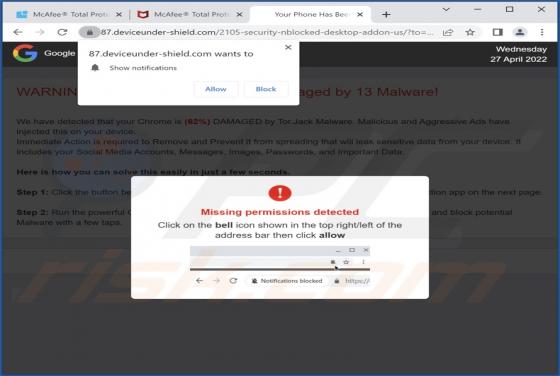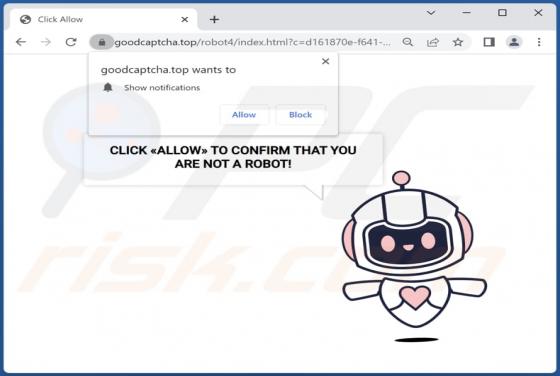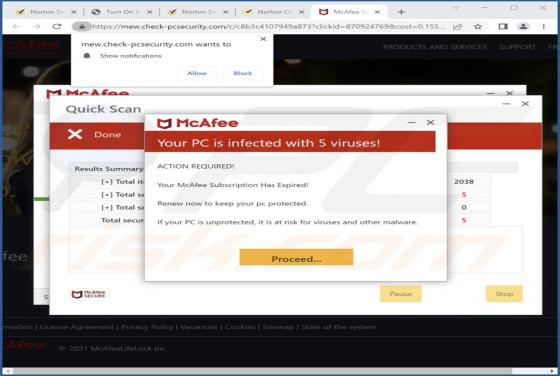
Check-pcsecurity.com Ads
Check-pcsecurity[.]com is an untrustworthy website running the "McAfee - Your PC is infected with 5 viruses!" scam. It is designed to trick visitors into believing that their computers are infected. Also, this site asks for permission to show notifications and may redirect to other shady pages.