News-nubuyo.cc Ads
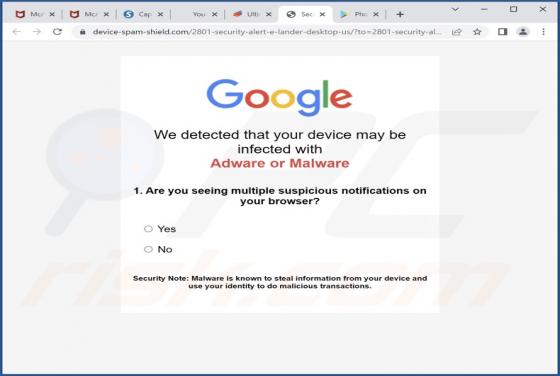
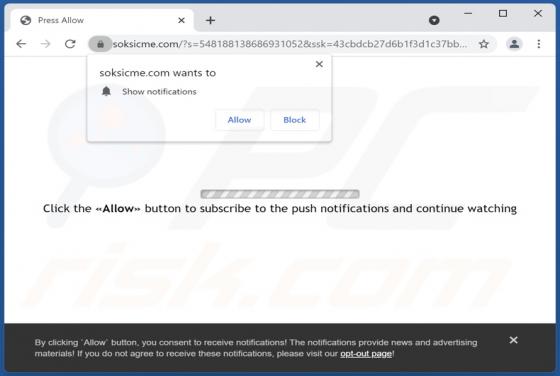
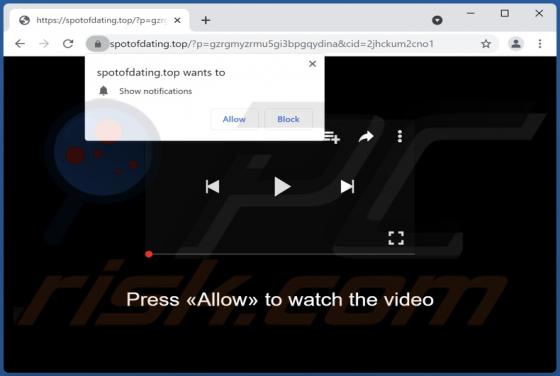
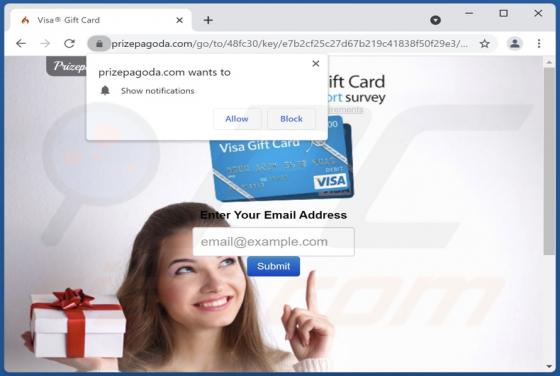
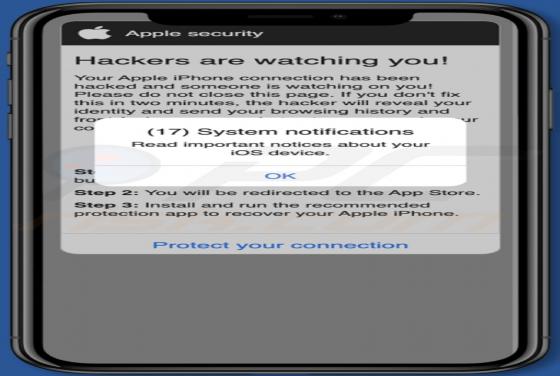
News-nubuyo[.]cc is a deceptive page designed to trick visitors into agreeing to receive its notifications. Another issue with this site is that it redirects to other pages of this type. Our team has discovered news-nubuyo[.]cc while examining illegal movie streaming pages, torrent sites, and simi