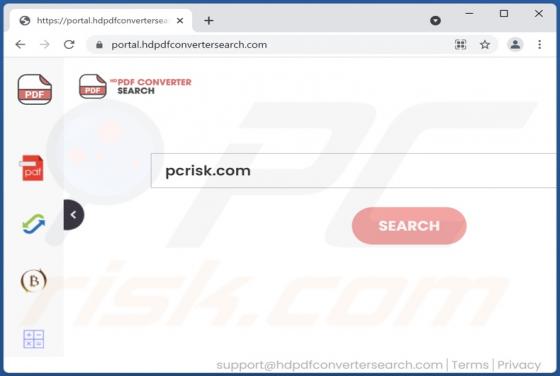
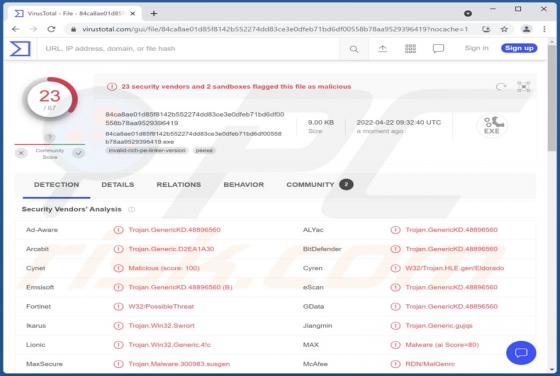
TopConverterSearch Browser Hijacker
We have discovered the TopConverterSearch application while inspecting various shady websites. After downloading and installing it, we found that it is a browser hijacker designed to promote topconvertersearch.com (a fake search engine). TopConverterSearch hijacks a web browser by modifying its se