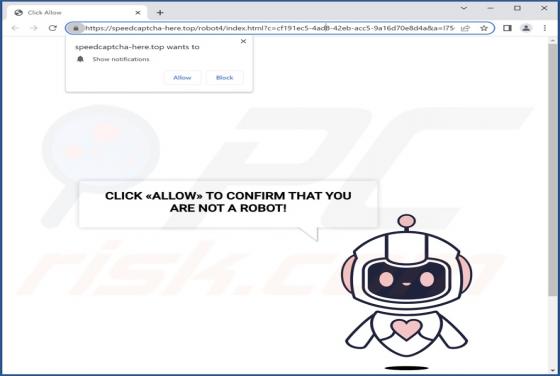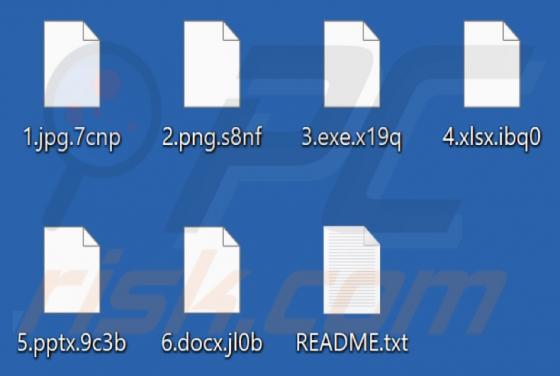
ZORN Ransomware
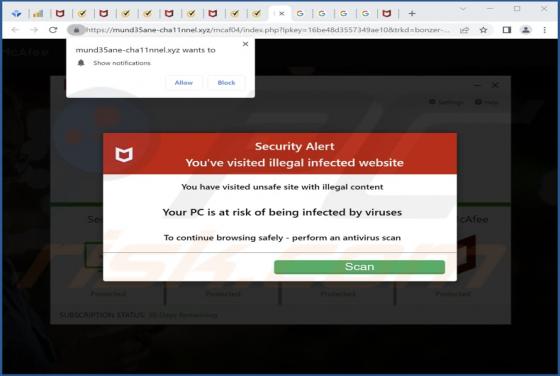
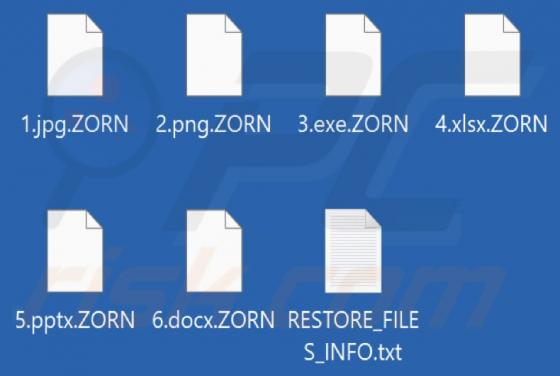
ZORN is ransomware that encrypts files and appends the ".ZORN" extension to filenames. It also creates the "RESTORE_FILES_INFO.txt" text file (a ransom note) and displays a black screen with text on it before logging into Windows. We have discovered ZORN ransomware while analyzing malware samples